Blog
Updates and insights on data ownership in the AI era — exploring how permission builds a safer, more transparent, and rewarding digital future.

Recent Articles
Permission’s $ASK Coin Listed on Gate.io Exchange
Permission is delighted to announce that the ASK digital currency will be listed on Gate.io, one of the top ten cryptocurrency exchanges globally with over ten million registered users. ASK will begin trading on Gate.io on February 17, 2022, with an ASK/USDT pairing.
The exchange offers spot, margin, futures and contract trading in addition to DeFi products through Hipo DeFi, custodial services through Wallet.io, investments through Gate Labs and its dedicated GateChain platform. Users can participate in a number of activities with ASK, including a liquidity mining rewards program where they can earn for providing liquidity for ASK.
“It has been an exciting year for the crypto industry, and we are looking forward to having ASK be more readily available to crypto enthusiasts globally through our partnership with Gate,” said Charlie Silver, CEO of Permission.io. “ASK is the currency of permission, and we look forward to expanding ASK’s visibility while continuing our mission to empower consumers to own and earn from their data.”
Global privacy regulations, ad blockers, and ever-changing ad tech trends are calling for a new and improved advertising model-one built on consent and value exchange. Permission.io enables a global tokenized ad system whereby consumers can securely grant permission and monetize their data across the web, and marketers can build loyalty and trust while achieving better return on their ad spend.
Permission Partners With Amasa
Permission is delighted to announce a new partnership with Amasa. Aligning with Permission’s mission to empower users to own and earn from their data, Amasa is a Web 3 and DeFi platform that enables users to capture and capitalize on the wealth-building potential of micro-income streams and DeFi.
In this collaboration, Amasa users will be able to combine their Permission income with other background streams, then amplify this combined value via DeFi. Permission and Amasa will collaborate on technical integration opportunities to maximize income potential for users, and Permission looks forward to expanding its network of like-minded projects through Amasa’s Web 3 platform.
“Partnering with Amasa is right in line with our shared vision of truly empowering people to own and earn from their data – this connection serves to speed up the process for consumers who are now producers in Web 3” says Bobby Petersen, Permission’s VP of Marketing.
About AmasaBy building the world’s first micro income stream investment app, Amasa is working to inspire mass adoption of Web 3.0 platforms that reward participants for their gaming, time, energy, attention, content, data and interactions.
What Is Staking Crypto and How Much Can You Earn?
While traditional finance solutions offer very low or even negative interest on their savings products, the crypto industry is always coming up with new ways to earn money.
In addition to investing and trading, the decentralized finance (DeFi) sector offers an excellent alternative to generating passive income through numerous ways, such as yield farming and cryptocurrency lending.
Today, we will introduce you to staking, a popular activity both in the DeFi and broader digital asset space. Staking crypto not only allows you to put your coins to work and earn rewards but also helps secure the networks of various blockchain solutions.
In this article, we will explore what crypto staking is, how it works, where to get started, as well as the potential risks and revenue you can generate with the activity.
What Is Crypto Staking?
Crypto staking refers to the activity in which a user locks coins in a wallet for a certain period of time to secure the network of a blockchain based on a Proof-of-Stake (PoS) consensus mechanism (or its variant, i.e., Delegated-Proof-of-Stake).
In terms of blockchain security, the network will choose a user who has staked his coins to validate the next block either randomly or by utilizing various factors (e.g., the amount of tokens staked).
In exchange for maintaining the ecosystem, users who stake their coins earn rewards, which is usually the combination of the cryptocurrency included in the block they validated and the fees associated with the transactions they processed for users.
What Is the Difference Between Crypto Staking and Mining?
It’s important to talk about the difference between crypto staking and mining. While both activities have the same purpose – to secure the network, generate new blocks, and validate transactions – they use two distinct approaches to achieve this goal.
Cryptocurrency mining is present mostly in Proof-of-Work (PoW) blockchain networks (e.g., Bitcoin), where validators (called miners) are required to leverage their computational power to solve complex mathematical puzzles to validate blocks.
For this, they purchase specialized hardware (e.g., ASICs and GPUs), which they operate continuously to compete with other miners to secure the reward for each block.
The higher the hash rate (computational power) in a PoW network is, the better it can protect against both internal and external threats, such as 51% attacks and malicious nodes.
As you can see, this is a rather energy-intensive process, which the PoW consensus algorithm has been long criticized for.
On the other hand, PoS blockchains do not require validators to utilize physical hardware or computational hardware to secure the blockchain. Instead, validators lock up their coins in their wallet via staking. Simply put, they guarantee the network’s safety with their money.
While this significantly reduces the energy consumption of the blockchain, staking is a similarly efficient mechanism in protecting users as mining blocks via the PoW algorithm.
In terms of investment, staking can be a more attractive method for users as it doesn’t feature the high upfront costs of mining (where you have to purchase the equipment first to get started) while providing a more predictable revenue stream (in a similar way as a savings account or a government bond).
Furthermore, staking has a well-established infrastructure within the crypto space. As a result, plenty of services offer an easy, flexible way for users to stake their coins. This contrasts with cryptocurrency mining, which requires miners to possess the technical knowledge and skills to maintain their equipment.
How Does Crypto Staking Work?
Now that you know the basics, let’s see how crypto staking works in practice.
First, it’s important to mention that staking is present in the crypto space in two different forms.
We have already taken a look at the first, where validators lock up their coins in their wallets to secure blockchain networks based on the PoS algorithm.
The process works as follows:
- A user deposits cryptocurrency into a supported wallet or staking service.
- The user selects the period (e.g., one month) he/she seeks to stake coins and utilizes the service to lock them up in his or her wallet. Alternatively, some solutions allow flexible staking, where users are free to withdraw their crypto holdings at any time without a mandatory lock-up time.
- After the lock-up period ends (or, in the case of flexible staking, the user is satisfied with the rewards), the staking provider releases the user’s coins and distributes the earnings after deducting the fees for providing the service (usually a percentage rate subtracted from the profits).
- The user is free to withdraw, spend, or re-stake the coins to generate more rewards.
The second type, called DeFi staking, is utilized not for safety purposes, but to offer a desirable user experience on certain decentralized exchanges (DEXs) that feature non-custodial atomic swaps between cryptocurrencies.
Unlike centralized exchanges, these DeFi solutions called automated market makers (AAMs) feature an entirely decentralized process for swapping coins. However, as they lack the order books of centrally-operated services, AAMs have to acquire liquidity from their users to facilitate efficient trading.
For that reason, they incentivize their users to supply both tokens of a trading pair at a 1:1 ratio in a liquidity pool. These rewards are usually offered in the platforms’ native coins after liquidity providers (LPs) have staked a special type of cryptocurrency called LP token.
LP tokens represent the users’ share in a liquidity pool, which they can redeem at any time for the tokens they supplied to the protocol along with their rewards.
By staking LP tokens, users lock the liquidity they provided to a specific platform for a certain period. Since this is a beneficial scenario for the service provider, it makes sense for the protocol to offer staking rewards for LPs.
Now let’s see an example for DeFi staking:
- A user connects his wallet to a DeFi AAM protocol and deposits DAI and ETH at a 1:1 ratio (1 ETH and $3,485 DAI based on October 11 prices) in the DAI/ETH liquidity pool.
- As the next step, the protocol issues the amount of DAI-ETH LP tokens that represent the user’s share in the pool and distributes them to his or her wallet.
- The user locks the DAI-ETH LP tokens on the protocol for 30 days to earn native token rewards from the service provider.
- After 30 days, the user redeems the DAI-ETH LP tokens for his or her original tokens as well as to claim any staking and liquidity provider rewards (e.g., a share of trading fees from the pool).
As you can see, no matter the staking type you choose, the process is similar in both cases and rather straightforward. And, while the mechanism is utilized to achieve different goals for the platforms, it serves the same purpose for stakers: to generate profits.
How Much Staking Rewards Can I Earn?
Besides its simplicity and lack of upfront costs, staking has become so popular in the cryptocurrency industry because it’s an excellent way for users to generate a passive income.
Staking rewards vary by the coin, which can range from anywhere from 1-2% to as high as 150% annually, especially if we take compound interest into account (when you maximize your gains by continuously re-staking or reinvesting your profits along with the principal sum).
In most cases, cryptocurrencies with larger market caps offer lower annual percentage yields (APYs) than smaller coins.
For example, while Ethereum (ETH) and Cardano (ADA) features 5-6% APYs, smaller-cap digital assets like DefiChain (DFI) or the Mirror Protocol (MIR) allow stakers to earn a yearly 70-75% after their coins.
Furthermore, rewards can also vary by the platform or service you utilize for staking. For example, while Binance and Everstake offer a 5.54% APY on ADA, some pools only feature a 3-4% ratio.
The reason for the variance in rewards may be due to two factors.
First, all of these services operate staking pools where they combine the locked coins of users to increase their chances to become validators and gain rewards.
At the same time, many PoS-based blockchains choose a validator for a block based on the amount of staked cryptocurrency. This means that the larger the pool, the greater chance it has to produce blocks and the better rewards it can generate for users.
Second, the commission service providers deduct from user profits can greatly impact one’s staking rewards. While some pools operate without fees, others charge 3-12%, and there are also platforms with extraordinarily high rates (30-50%).
For that reason, it’s crucial to research both the coins and the staking providers to generate the best staking rewards.
Is Staking Crypto Safe?
In general, crypto staking can be considered a safe activity within the digital asset space. However, it definitely comes with certain risks.
Unlike crypto lending, where lenders mostly earn revenue on stablecoins – digital assets pegged to one or a basket of other financial instruments (e.g., USD, EUR) to stabilize its price movements – staking predominantly involves locking up “standard,” non-stablecoin cryptocurrencies.
For that reason, the coins you dedicate to staking are subject to the high volatility associated with the cryptocurrency asset class (especially if you stake small-cap coins). As they can increase and decrease in value in short periods, this increases the risks of stakers.
These risks increase if you choose a staking service where users must lock up their coins for a specific period as you won’t be able to liquidate your crypto holdings in the case of a sudden market crash or another price movement (even if it’s favorable).
However, if you choose a flexible staking provider with no mandatory lock-up periods, you can mitigate your risks.
That said, volatility is not the only risk that comes with staking. For that reason, you should also be aware of the following factors:
- Counterparty risks: You can choose to stake your coins either on a centralized service where the provider stores your crypto holdings on your behalf or via a decentralized, non-custodial solution. If you choose the former, you should know that the platform is in custody of your private keys, which provide access to your coins. For that reason, you face increased risks of a loss in case of a successful hacker attack or an “internal” exit scam, unless the provider features the necessary security measures and guarantees.
- Smart contract bugs: If you stake coins as a liquidity provider on a DeFi protocol, you should be aware of the risks of smart contract bugs. Since these platforms use smart contracts to operate, a small issue in the code can lead to grave consequences for users. Therefore, you should always ensure that you use a reputable platform that features audited smart contracts.
- Slashing: Staking services handle all the technical parts of staking for you, including operating a blockchain node and validating blocks. However, suppose the provider is dishonest or fails to maintain a 100% uptime. In that case, some networks punish it by refusing to distribute rewards for a block or even slashing all its cryptocurrency stake. In the latter case, all users who have staked crypto via the service would lose their locked-up tokens.
Based on the above information, staking can be a high-risk activity. However, that is only true if you fail to do your own due diligence.
For example, you can significantly decrease your risks by staking your coins via a secure wallet through a reputable provider that features a long-standing history of continuous uptime and honest activity as part of a non-custodial solution.
Where to Start Staking Coins
Earlier on, we discussed the process you have to follow to stake your coins.
Now, you only need to choose the platform and method you will use to generate rewards after your cryptocurrency holdings.
For this, you can select between four different solutions:
- Cryptocurrency exchanges: Crypto exchanges provide one of the most convenient ways to stake crypto as you don’t have to move your holdings to other wallets or platforms to generate rewards. While this can come in handy when network transaction fees are high, this is a custodial solution that involves increased counterparty risks.
- Staking service providers:Like crypto exchanges, staking-as-a-service providers offer easy access to staking across numerous blockchains. However, these also involve custody over users’ funds.
- Crypto wallets: Many cryptocurrency wallet providers allow their users to stake their coins directly from their wallets without an intermediary. As a result, they don’t face the counterparty risks of custodial services while offering the same level of convenience (and similar reward rates).
- Manual staking: This is maybe the most complex method to start staking, which is a possibility for advanced users. Here, you operate your own node and stake your coins on your own. While this offers you the most freedom, it requires the necessary time and technical expertise to run your machine as well as a higher upfront investment for many blockchains (as there is usually a minimum amount validators have to meet).
It is also important to mention cold staking, where you generate a passive income via a wallet (e.g., a hardware wallet) that is not connected to the internet. For that reason, it’s probably one of the safest ways to earn revenue with the activity.
Staking: An Easy Way to Earn Rewards on Your Crypto Holdings
Crypto staking is a widely popular activity, where you can easily generate extra revenue on your digital assets without significant upfront investments.
As it only takes an initial deposit and a few clicks to get started, staking is a great way for both beginners and advanced crypto users to earn coin rewards.
At the same time, long-term investors can utilize staking to put the cryptocurrency they hold to work to maximize their profits.
In terms of risks, staking is generally a safe way to earn crypto. However, users must do their own due diligence as well as select reputable (ideally non-custodial) providers and coins with larger market capitalizations to minimize their risks.
Mastering Loyalty Programs: 6 Killer Options + Pro Advice
Stories of free flights, incredible deals, and “just used my points” are common these days. And for people who aren’t into loyalty programs, those who manage to travel so much on a low budget almost have this mystical aura about them. How do they do it? What do you mean she got a free flight and 4-star hotel for nothing?
Loyalty programs are designed to get you to come back to businesses, and they can be cumbersome and draining if you’re in too many or don’t choose the right ones, but if you know how to play the game, you can save yourself thousands of dollars on purchases you would have made anyway.
One of the keys to winning in loyalty programs is staying on top of the latest offers and loyalty programs. And while points and cash back programs have dominated the space for years, we’re going to show you how to both make the most of existing loyalty programs and show you what the future of loyalty programs looks like — that way you can stay on top of things.
Let’s go!
Common Types of Loyalty Programs
Since loyalty programs are any sort of program that rewards customers for purchases, consistency, engagement, referrals, etc. There are a lot of types.
Here are a few of the most popular:
- Points programs like credit card or hotel points
- Subscription programs like unlimited monthly coffee, Regal Unlimited, or Amazon Prime
- Referral programs like The Hustle’s referral system
- Tier-based programs like Chick-fil-A
- Cashback programs like Capital One’s Quicksilver Cash Rewards Credit Card
- Perks programs like Kroger’s gas discount
- And many more!
There is an abundance of loyalty programs these days. So the trick isn’t finding them, it’s deciding which ones to use.
Why Should You Join Loyalty Programs?
When used correctly, loyalty programs save (or give) you more money than you would have had without them.
For example, if you spend $500 a month on groceries, have a credit card that gives you 2 points (worth a cent each) for every dollar spent, and pay off your credit card in full each month, you would get an automatic $10 back each month for doing exactly what you do anyway.
Or take credit card bonus fees. If you’ve been saving up for a new entertainment system that costs around $3,000, and instead of paying cash you signed up for a new credit card that had a “sign-up offer” that gives you $600 in points after spending $3,000 in the first two months, you could get $600 back on a purchase you were already going to make.
By optimizing your spending around the highest value programs whose points or rewards can be used on purchases you were already going to make anyway and strategically utilizing sign-up bonuses, you can save thousands of dollars over a few years, pay for flights, get free hotel rooms, and more.
It takes a bit of work to get set up and switch at the right times, but it’s still well worth the effort you put in.
The 6 Best Loyalty Programs You Should Consider Joining
Again, loyalty programs are designed to get you to spend more, but if you’re aware of that fact, you don’t have to.
By only joining programs that directly impact your existing spending, you can minimize the temptation to overspend / nullify the value of your rewards.
With that in mind, here are some of the best loyalty programs out there. We’ve included a diverse list — that way you could feasibly make a good decision by just going with all of these. These options are more useful when starting out than 5 different airline programs, for example.
Note: These are based off of NerdWallet’s 2021 Winners, personal experience, and other misc. research. The program details below were accurate at the time of the writing but may not remain the same.
Alaska Airlines Mileage Plan
Ideal for casual domestic flyers who like to take one other person on their trips.
While you won’t be able to fly anywhere, anytime, the rewards system of Alaska Airlines is fantastic. If you make $2,000 of purchases within 90 days, you get 40,000 bonus miles (around $440) and the Annual Companion Fare, which can drop a ticket for a friend down to $99 + fees. Add in rewards based on miles instead of cash and 3x miles for all Alaska Airlines bookings, and you can see why people love this loyalty program.
Reward Currency: Alaska Miles
Key Aspects:
- Reward based on miles flown instead of cash spent, which rewards smarter booking choices
- Can transfer points to Emirates and Cathay Pacific and other partners to 1,000+ destinations
- $75 annual fee
- 3 miles for every $1 on Alaska Airlines flights, 1 mile for $1 for all other purchases
- Free checked bags for up to 6 guests on the same reservation
- No foreign transaction fees
Amazon Prime
Best for frequent online shoppers who want quick deliveries.
You may not think about Amazon Prime as a loyalty program, but that’s because it is so good at what it does that it escapes the label. Amazon does everything they can to make you lose money by not being a part of Prime (assuming you shop at Amazon regularly).
From Prime video, to free shipping, to lower prices in Amazon, using Amazon and not having Prime doesn’t make any sense, and that’s the point.
Reward Currency: None
Key Aspects:
- Free two-day shipping on Prime eligible items
- Prime discounts
- Early access to deals
- Prime video streaming
- Pay monthly at $12.99 or yearly at $119
Chick-fil-A
Good for anyone who eats Chick-fil-A more than 2x a month.
Chick-fil-A, regardless of your opinion of fast food and their enterprise, is a brilliant business. They are superb at cleanliness, timeliness, consistency, and rewarding their customers.
Their loyalty program is legendary and has some really clever mechanisms to keep you coming back. So if you get down with Chick-fil-A at least more than 2x per month, then check it out.
Reward Currency: Points
Key Aspects:
- Three Tiers: Member, Silver Member, Red Member
- Points are rewarded for cash spent
- Birthday rewards
- Has giveaways for downloading the app and signing in consistently
- Mobile ordering through app makes pick-up easier
- Higher levels let you give away your gifts to others
- The higher level you are, the more points you earn per $1
- Higher levels have more say on the menu items Chick-fil-A releases
Capital One Venture Rewards Credit Card
A good “jack-of-all-trades” travel card for people who tend to fly on different airlines and use different hotels.
Capital One’s Venture Rewards Credit Card has been a big player in the credit card points game for a bit. The points are easy to earn and use, and you can transfer or spend your points on just about anything.
Reward Currency: Miles
Key Aspects:
- 60,000 mile bonus after spending $3,000 in the first month (~ $600 value)
- 2 miles per dollar spent on anything and everything
- $95 annual fee
- Best value when you redeem for travel
Permission
Good for anyone who wants to get paid for doing what they already do on the web.
Here’s the deal. Almost everything you do on the internet involves and leaves data, but since the dawn of the internet, YOU haven’t been paid for the use of your data. Meanwhile, huge internet companies have made massive fortunes off of your information.
Permission prescribes to a simple but radical idea: shouldn’t you get paid for your data?
And the best part? You don’t have to change any of your habits. You join Permission, and companies reward you with crypto in return for your time and attention. It’s that simple.
Reward Currency: ASK
Key Aspects:
- A new type of loyalty program driven by crypto rewards
- A browser extension that lets you earn crypto based on your existing searches and habits
- Earn crypto for engaging with ads and content
- Is expanding its reach to become the backbone of loyalty programs everywhere everywhere, making it easier and more flexible for earners to redeem across brands.
Start earning from your data (for free)
Regal Unlimited
Great for any movie buffs who see more than 2 movies a month.
This is Regal’s answer to the spectacular fall of MoviePass. For ~$20/month you can watch as many movies as you’d like and earn on concession purchases. Since movies cost between $12-15 these days, if you go to at least two movies a month, you’ll be saving money.
Reward Currency: Crown Club Credits
Key Aspects:
- Different tiers open up more and more theaters, but the middle tier for $20/month is usually more than enough.
- Earn credits on all purchases that can be redeemed for free tickets and food. Pay for your friends’ tickets to rack up points!
- Unlimited movies per month, including new releases.
- Fees can apply for booking less than an hour in advance.
How to be a Loyalty Program Pro
Here are some tricks of the trade from loyalty program pros.
Make sure the annual fees make sense for your spending.
If you aren’t going to earn more in points than the annual fee, don’t go for it. That would just mean more unnecessary bills. It’s easiest to get hit by unnecessary annual fees when you have a lot of cards, so make sure whichever ones you have you’re actually using!
Note many credit card companies will cancel or reduce your fee if you call them to cancel shortly after noticing an annual fee charge.
Ditch the cash.
The more you spend on your card, the more points you earn. Cash should become a last resort — it’s a pointless transaction!
Maximize your earnings by choosing which card to spend with on particular categories.
Some cards earn you more on food. Other more on flights. Know which cards are best spent where so you can maximize your earnings.
Choose loyalty programs that fit into your existing habits
The point of loyalty programs is to get you to spend more, but you can outwit them by only choosing cards that complement your existing spending habits. If you already fly multiple times a year, there’s no reason not to earn from them, but if you don’t already shop at Nordstrom, maybe you don’t need their card.
Get your credit score to above 720
Most loyalty programs and good credit cards with rewards require decent credit. If you aren’t above 720 yet, put the time and work in to get there before going down the loyalty program rabbit hole.
Do not go into debt over points
No points are worth suffering from the atrocious interest rates on credit cards. Whatever you do, do NOT carry a balance! This excludes particular people with good handles on leverage, but anytime you rack up interest you are cutting right back into your point profits and likely going in the red.
Take advantage of welcome bonuses
Welcome bonuses are critical to earning from rewards programs. Line up your big purchases with a new card to earn big.
Stack points
Use your best food-to-points credit card to plug into your Chick-fil-A rewards program. Use your favorite flight card for Regal Unlimited — find as many ways as you can to stack your favorite cards and programs.
Avoid opening a bunch of credit lines before big purchases
Credit card churning and loyalty programs can mean opening up more lines of credit, which can negatively affect your score. If you’re going to buy a house or car in the near future, you may want to hold off.
Respect the 5/24 rule
While not official, many credit card companies begin to be more cautious with users who open up more than 5 cards in two years (or 24 months), so it’s best practice to stay at or under this split.
Amazing Resources for Credit Card Churning
When you join multiple programs, things can get a bit confusing. Here are some tools and resources that will help you make the most of your programs.
- NerdWallet — one of the best rewards blogs out there
- AwardWallet — track all of your programs and points in one place
- ThePointsGuy — amazing blog for travel point optimization
The Best Loyalty Program is a Universal Loyalty Program
The new era of loyalty programs has arrived
Imagine an internet where every single online transaction, across any brand, in any store, earns you a single type of reward currency that you can spend on more products, or trade for other global currencies (including dollars).
That is the future of loyalty programs. A world where the myriad of points, miles, cashback dollars, and rewards dissolves into a single reward currency that everyone is familiar with. One wallet, one currency, across an unlimited number of brands.
Brands will still be able to create their own unique incentives founded in this currency. And users can earn more whenever they want by engaging in specific actions encouraged by brands, like voluntarily engaging with ads or giving a company more information about themselves.
So if you’re a user who wants to get paid for your data, or a brand looking to add in the ASK cryptocurrency to your incentives, now is the time.
Earn Cryptocurrency Watching Videos (5 Legit Ways)
The world of cryptocurrency is a bit like the Wild West. There are rumors, a lot happening underground, and occasional but increasing government interest. People are looking for gold, and companies are looking to sell the shovels.
The result is a regulatory haze and technical fog that hangs over crypto, making it a bit difficult to figure out how to earn crypto easily and reliably. We get it, and that’s why we’ve taken the time to compile a list of sound ways to earn crypto by watching videos. Those videos are usually ads, but there are some interesting projects that go beyond advertising as well.
What makes a good cryptocurrency earning app?
Here’s what we were thinking through when making our choices.
- Reliable payouts
- Good UX/UI
- Good earning potential
Crypto is a rapidly evolving space, and new opportunities appear all of the time. So while we do stand by this list, it’s a good idea to keep a pulse on the crypto world through the news and social media to identify new opportunities as they arise.
And here are the most legitimate ways we’ve found to earn cryptocurrency by watching videos:
Coinbase Learning Center
Coinbase is one of crypto’s most widely used and trusted crypto exchanges. One aspect of their onboarding is the opportunity to earn crypto by learning about individual crypto currencies through their course videos. You get paid in the relevant cryptocurrency and can have it deposited directly into your coinbase wallet, at which point you can transfer or do whatever you want with it.
Their video courses cover a variety of cryptocurrencies including:
- Clover Finance
- The Graph
- BarnBridge
- AMP
- Stellar Lumens
- Compound
- Balancer
- Ampleforth Governance Token
And many more.
You can earn more than $50+ in various cryptocurrencies, so the payout is really good, but it’s ultimately a finite source. There are only so many videos, so you take a few hours, get your crypto, and get out.
If you’re new to crypto, the education is worth watching either way. It’s a complicated sector, and starting slowly and with an education-first mindset is the best way to prevent poor investments.
Coinmarket Cap Learning Center
Another option that functions in a similar way to Coinbase is the Coinmarket Cap Learning Center. Coinmarketcap has different videos and requires you to take a short quiz afterward, but the payouts and educational value are also high.
Here are some of the courses they offer:
- Toko Token
- IoTex
- SushiSwap
- Polkastarter
- Plasma Finance
As you’re going through these, try and see which tokens you think have the most potential. These courses are essentially ads and pitches, after all. If one seems particularly promising, you could bankall of the coins you earn from these courses and trade them for the one or few cryptocurrencies you think are most promising.
Try CoinmarketCap Learning Center
Odysee
Odysee is positioned as an answer to Youtube’s and other major information platforms’ censorship and aims to be a decentralized educational and content resource.
Creators can post their videos on Odysee without any fear of censorship, and users can earn LBRY, their token, by watching and interacting with videos. When you watch a video on Odysee, both you and the creator earn crypto. This rewards you for your data and engagement while encouraging creators to continue to release videos on Odysee.
Whether or not earning cryptocurrency on Odysee is worth your time partly depends on if you believe in the LBRY crypto itself.
This is their mission:
First and foremost, LBRY is a new protocol that allows anyone to build apps that interact with digital content on the LBRY network. Apps built using the protocol allow creators to upload their work to the LBRY network of hosts (like BitTorrent), to set a price per stream or download (like iTunes) or give it away for free (like YouTube without ads). The work you publish could be videos, audio files, documents, or any other type of file.
If you think something like LBRY could compete with (or work alongside) a service like Spotify to enable artists to earn more from their music, this could be an interesting choice.
Permission
Permission.’s mission is to give data ownership back to the people. Broadly speaking, this means rewarding you with crypto for any online interaction that involves your data. It’s your data, after all, and if companies want to use it, they should pay you for it.
We’re just getting started with our Web 3.0 revolution, but one example of our mission in practice is our Permission.io browser extension.
The Permission.io browser extension helps you earn cryptocurrency as you surf the web. After you install the extension on Chrome, if you search for something and a relevant video ad is available, we notify you of the option to earn for interacting with that video.
For example, if you were into skateboarding and typed “new skateboards,” and a rewarded ad featuring a skateboarding apparel or board company is available, you could be notified with a video ad that essentially says, “Hey we make skateboards. Wanna check it out?” And then if you do, you earn $ASK crypto for watching the video and even more if you end up buying the board from them.
And the best part? You don’t have to change any of your existing habits. They’re non-intrusive, opt-in ads.
PlayNano Online
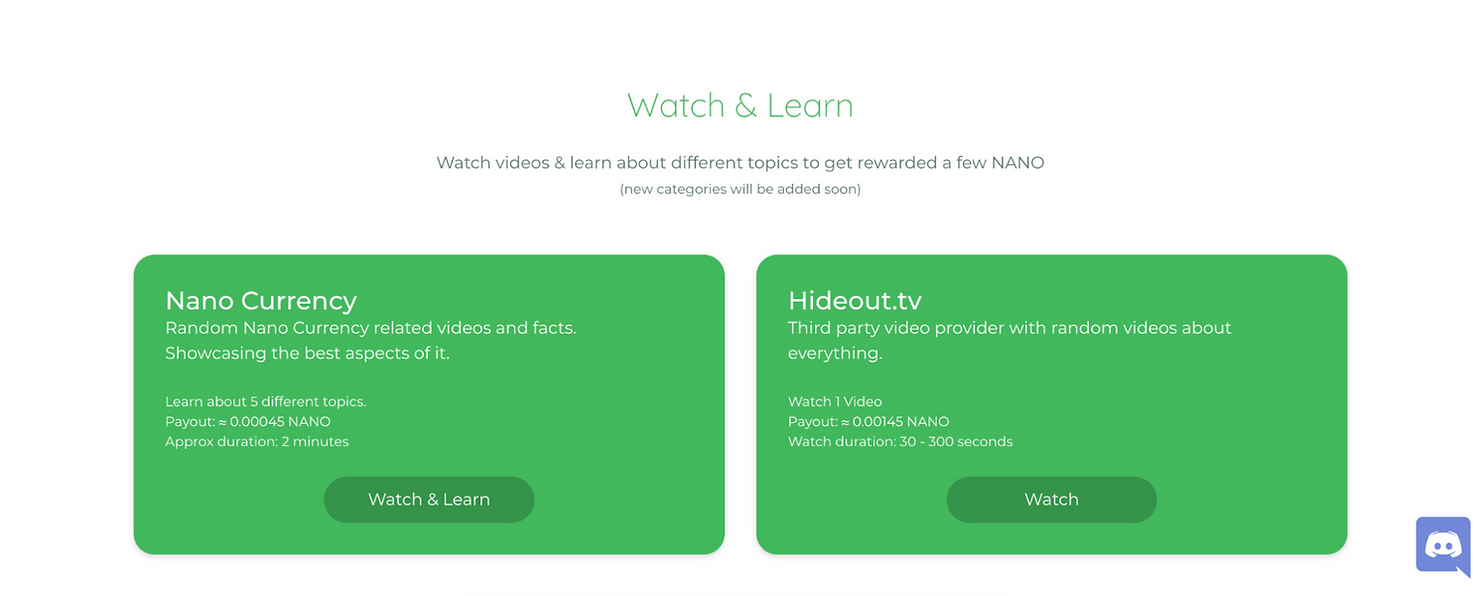
While somewhat polarizing due to its price and relationship to the BitGrail $195 Million hack, the Nano community is vibrant, enthusiastic, and has created many ways to earn Nano.
Nano is aimed at being a decentralized currency and hopes to eliminate middlemen that charge transaction fees and tack on other hidden costs. Imagine instant wire transfers between countries for free — that’s the type of world Nano is aiming to build.
PlayNano, specifically, is a project that lets you earn Nano by watching videos, playing games, completing surveys, and other activities.
Like the other options here, it depends on how much you believe in Nano, but if you do, then this is definitely a good option.
The bottom line on earning cryptocurrency by watching videos
With the exclusion of a few companies like the online exchange courses and Permission.io browser extension, earning cryptocurrency by watching videos isn’t a smooth landscape yet. Most of the payouts are very low, and you are still subject to the whims of the crypto market.
These are the best options we know of, but you should still do your research, see which cryptocurrencies you think have the best chance of succeeding, and spend your time watching videos that let you earn those currencies.
The 5 Best Bitcoin Earning Apps of 2021
BTC is the most popular cryptocurrency in the world, and while you won’t earn a ton from these apps, if you find some that fit into your existing habits and the price of bitcoin continues to rise, then they may be worth your time.
What Makes a Good Bitcoin Earning App?
When thinking through what makes the ideal bitcoin earning app, we focused on these criteria:
- Trustworthy and transparent. There’s a lot of fraud and abuse in the crypto space, so knowing that there is a legitimate business behind the app is important.
- Low payout floors. You don’t want to have to wait forever for a payout, so the lower the floor to cash out, the better.
- Good UX and UI. Apps like these need to be easy to use and enjoyable. The payouts are so low that there’s no room for frustration or wasted time.
- Reliable payouts. Nothing matters if you can’t actually get paid after you’ve put the time in. All of these apps have reliable cash-out options.
- Active community. An active community plays into trust and ensures that the company will continue to be incentivized to improve the app and accompanying services.
With that in mind, here’s a shortlist of our favorites separated by category, and we have longer explanations farther down.
The Best Bitcoin Earning Apps
- StormX for shopping
- FeaturePoints for surveys
- Alien Run for getting addicted to earning
- Bling’s Bitcoin Games for general gaming
- BitforTip for answering questions
And here’s a bit more detail on each of these apps. Each of these are available on iOS and Android, and as you go through this list, try and see which ones you can fit into your existing habits.
1. StormX: Best Bitcoin Earning App for Shopping
StormX takes the familiar online cashback model where brands give the referral company cuts of the sales and then that company gives you (the buyer) some of that split and augments it with cryptocurrency payouts.
With StormX, you can earn by shopping on their 750+ partner store, getting anywhere from 0.5% to 87.5% back in crypto. They work with legitimate stores as well, including Lego, Sega, Doordash, Samsung, Microsoft, and more.
You can also earn more crypto by HODLing your crypto in their membership program, playing games, and filling out surveys. Then, you can cash out with Bitcoin, Ethereum, or STorm.
StormX is best for people who already do a good amount of online shopping. For example, if you have kids who love LEGOs and games, you could do all of your Christmas shopping through StormX and get a free crypto kickback.
2. FeaturePoints: Best Bitcoin Earning App for Surveys
FeaturePoints pitches itself as the solution to earning from your downtime. A.k.a. those minutes when you’re stuck in line or bored at the doctor’s office. While surveys are the main way people earn on this app, you can also shop with partners, download free apps, and watch videos — all of which can be turned into cashback via PayPal, gift cards at specific retailers, or turned into Bitcoin.
They also have a cool referral program where you earn from every friend that signs up and continue earning every time they earn — for life.
If you find yourself running a lot of errands or don’t mind filling out a quick survey when pinged by a notification, then FeaturePoints could be good for you. I wouldn’t set aside specific hours to invest into FeaturePoints since the payouts are so low, but if you casually answer questions every few months or so you may be able to cash out a few bucks into Bitcoin.
3. Alien Run: Best Bitcoin Earning App for Addictive Gaming
If you like to game and wouldn’t mind a small amount of Bitcoin to go with that time, then check out Alien Run. It’s a genuinely fun game with a good mix of easy and difficult levels, and new missions are released daily.
The app has a lot of ads, though, and the payouts, like all of these apps, are low. So if you already game and genuinely enjoy Alien Run, then sure, why not, but if you’re downloading Alien Run only to earn Bitcoin, then you have better options.
4. Bling Games: Best Bitcoin App for General Gaming
Bling is a game developer that has a variety of simple games you can play to earn Bitcoin including Bitcoin Blast, Bitcoin Blocks, Bitcoin Food Fight, and more. You create one central account that is linked to all of their games and collectively earn while playing. The games are well-built and have fun multiplayer options, but you have to watch an ad after every game and the payouts are low.
Our advice is similar to Alien Run. If you already play games like solitaire, Candy Crush, or 2048, then you’ll probably enjoy these Bitcoin games, and swapping your play time to one that earns you a small amount of Bitcoin could be worth it.
5. Bitfortip: Best Bitcoin App for Being Helpful
Bitfortip definitely needs work and is hit by a lot of spammers, but we’re including it because there’s still an active community and it’s an interesting idea. You can think of BitforTip like Quora but you’re paid for your answers with small amounts of BitCoin.
For example, you may hop on the site and see that someone asked: “How easy is it to replace spark plugs in a Honda Civic?” along with an attached BTC reward amount. If you have mechanical expertise and could answer it, you can “win” the associated BTC tip for that question.
Bonus: The “Earn While Your Browse” App
Permission’s Browser Extension helps you earn $ASK crypto for browsing and engaging with relevant brands online.
For example, let’s say you’re into building gaming computers, and you’re looking for a new solid-state drive. If you search for a SSD and one of our partners has one they think you would like, your extension will ping you with the option to watch a relevant ad. If you choose to do that, then you’ll instantly earn the displayed amount of $ASK. And then, if you dig the SSD and buy it, you’ll get an even larger $ASK payout. Plus, if you’d prefer to own BTC instead of $ASK, you can choose to trade it for bitcoin on an exchange.
And this browser extension is just the beginning. Permission’s browser extension is part of our mission to take back data ownership from the internet barons and help users all over the world start earning from the data. If you think you should earn for the data you’re already giving away for free, then you should join us and start earning $ASK.
What You Need to Know About Bitcoin Earning Apps
The unfortunate truth to bitcoin earning apps is that the payouts are extremely low.
With the exception of the Permission browser extension, all of the apps we found pay such small amounts, often amounting to fractions of a cent or minuscule amounts of Bitcoin (typically Satoshi), that the time you spend on these apps can almost always be better spent doing something else that would allow you to buy even more bitcoin.
For example, instead of spending 5 hours a week getting pennies on the dollar on these apps, you could teach a skill online, collect recyclables, sell baked goods, or do any other number of small side hustles that you could directly invest into Bitcoin instead. If saving or investing is your goal, this would be a much more effective route.
Your best bet is to fit these apps into your existing life instead of spending what feels like “extra time” on them. Gaming when you’re stuck in line, completing surveys in doctor’s offices, and answering questions when you’re bored are good examples of this.
Then, every few months or so you’ll have a few bucks you can put toward your BTC balance.
Earn Crypto Without Changing Your Habits
Why aren’t you already earning for the data you’re giving away with every move you make online?
Surf the web like normal and earn crypto along the way. With Permission’s Browser Extension, earning from your data is finally easy.
Apps Like Honey: 6 Honey Alternatives To Try In 2021
Shopping online has come a long way, and when it comes to saving money online, you’ve got plenty of options. Honey is one of the most popular coupon browser extensions on the internet, but it is far from the only one. There are tons of services you can try, each with their own spin.
To save you some time figuring out which one is best for you, we’ve compiled a list of 6 other money-saving apps like Honey, along with some ideas on how to make the most of these apps.
We’ll start with a reminder of what Honey does and then get into our favorite alternatives.
What Is Honey?
Honey is a plugin for all major browsers that helps users save money while online shopping by automatically searching and applying any relevant coupon codes when checking out.
When you have the extension installed, you receive notifications during the checkout phase on any eligible store. If you hit accept, Honey will automatically search their massive database of online coupons and apply the best one. They also have coupon codes and exclusive deals that can be used to earn “Honey Gold,” which are points you accrue over time and can be redeemed for gift cards.
To be clear: Honey is a great extension, but people have reported bugs and sometimes take issue with the data it collects (which is something probably all of these extensions do), so having other options means you can either use a combination and/or find one that is better suited to your needs.
How to Choose the Best Coupon Browser Extension
Once you dig into the world of cost-saving extensions and apps, one thing becomes clear: most of these apps function and behave very similarly.
With that in mind, the best choice is actually a combination. Because these extensions and apps cover different retailers and strike timed deals with stores, the best deals can change at any point. For example, some may be better for finding deals on clothing than on software or for getting more back-to-school deals in August, etc.
That being said, if you’re prioritizing cashback opportunities, it may be best to invest more in a single platform instead of spreading out your earnings across multiple services. Diversifying too much can increase the amount of work it takes to earn & may hold you back from crossing different redemption thresholds (some apps won’t let you cash out until you earn a certain amount).
And finally, if you’re using these extensions as an exercise in budgeting, remember that these apps exist to get you to buy more. It may seem like you’re saving cash, but if you just end up shopping more than you used to, then it’s a net negative. If you aren’t concerned with that and are comfortable building them into your existing shopping habits, then they can be fantastic.
1. Capital One Shopping (formerly WikiBuy)
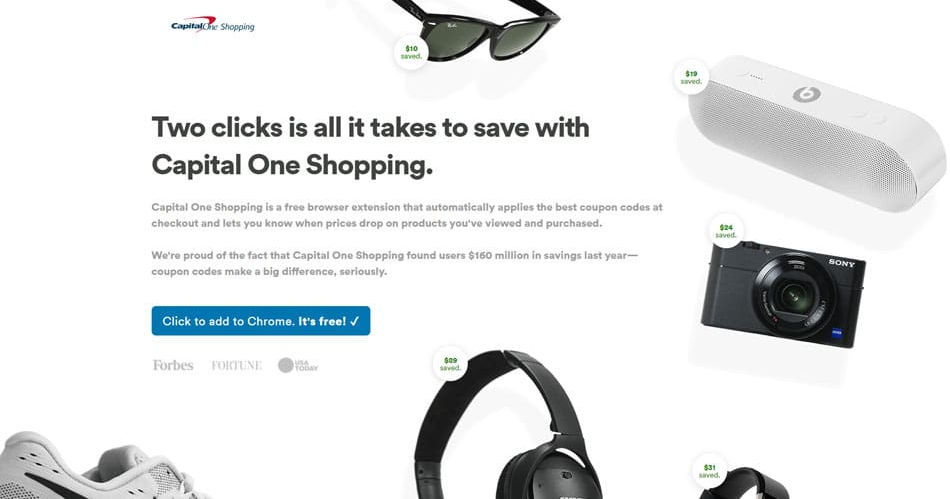
Capital One Shopping, which used to be Wikibuy, is the most direct competitor to Honey. They provide almost the same experience, with automatically applied coupon codes, price alerts, and more.
How Capital One Shopping Works
Capital One Shopping helps you shop online, which in turn lets Capital One get more transaction fees and collect useful data about you. Anytime you’re looking at products online, the extension will search thousands of other retailers to see if there are any other places you could buy it for cheaper and/or if a coupon code is applicable.
You’ve got options with Capital One Shopping, too. You can download the browser extension and get a lot of value from it, but you can go even deeper by picking up the mobile app as well. This lets you get mobile alerts on shopping deals and check if there are deals on in-store items as well.
Pros of Capital One Shopping
- Free
- Easy-to-use browser extension
- Trending deals and featured offers
- Shopping credit for shopping like normal
- Price drop alerts on products you want
- Mobile app can check in-store items as well
- Automatically applies coupon codes during checkout like Honey
- Backed by an active and large company, which usually means faster bug fixes and more deals.
Cons of Capital One Shopping
- Mobile app user experience isn’t great but is improving.
- They collect a lot of private information about you.
Where to Download
Download Capital One Shopping here.
2. Rakuten

Rakuten is incredibly popular, and it’s no surprise why. This one-stop-shop service works with retailers to bring you exclusive cashback deals, negotiates coupon deals for its members, and has partnerships with thousands of retailers from Amazon to Target.
How it Rakuten Works
Rakuten gets a kickback for every purchasing user they send to retailers, and then they share that kickback with you. You become eligible for these cashbacks by clicking from Rakuten into whatever retailer you’re shopping from.
The typical user experience with Rakuten involves seeing an extension notification and clicking through it to earn from it OR getting in the habit of going directly to Rakuten’s site to see if there are deals on items you’re thinking about buying. For example, if you know you’re looking to grab a Nintendo Switch for your nephew this Christmas, you could go to Rakuten with that in mind to see if there are any relevant kickbacks.
Pros of Rakuten
- Free
- Earn anywhere from 1-40% cashback on almost anything purchased through Rakuten.
- Thousands of retailers
- Get paid out in cash
- In-store earning opportunities
- Easy browser extension
- Mobile app
Cons of Rakuten
- Quarterly payouts
- Sometimes the best products at retailers aren’t eligible for cashback.
- Have to get in the habit of going from their site or extension to a retailer.
Where to Download
Download Rakuten here.
3. Karma (formerly Shoptagr)
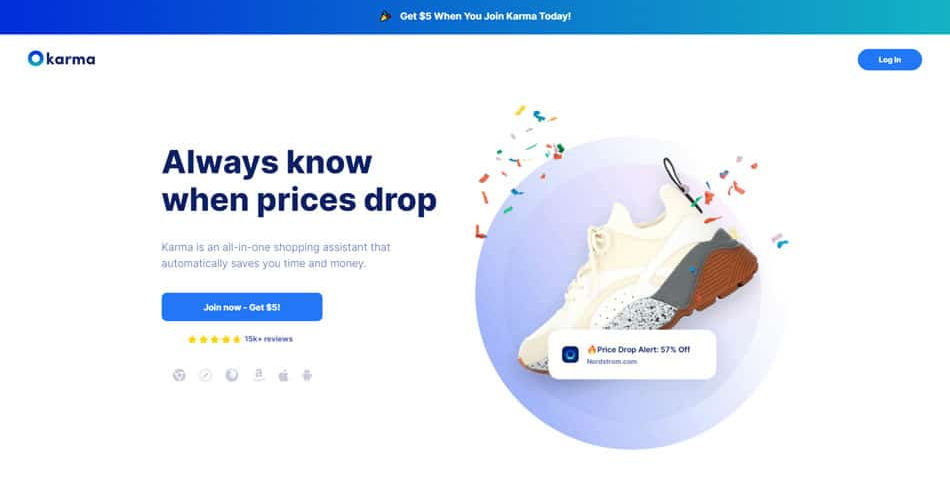
Karma is another extension and app you can use to get price drop alerts, automatically apply coupons, make wishlists, and organize future purchases.
How Karma Works
The secret to Karma’s success is in their tech — their predictive analytics bot helps consumers make better shopping decisions prior to purchase, whether by opting for a better price, applying coupons, or letting you know to wait until the price drops even more[*].
The best way to use Karma is to set up what you know you’d like to buy in advance and then wait as price drop alerts roll in. For any of you out there who like to start shopping for actual Christmas after Christmas in July, then this is right up your alley. You can set up your wishlist, organize your future purchases by category, and wait for that ping. Then you’ll know it’s the best time to pick it up!
Pro Tip: combine these alerts with CamelCamelCamel’s Amazon price history (alternative #6 in this list) to see if the deal is as good as Karma is saying it is.
Pros of Karma
- Free
- Wishlist for out-of-stock items
- Price drop alerts
- Organize future purchases by category
- Coupons automatically applied
- Extension works on Chrome, Mozilla, and Safari
- Pays out in PayPal
- Mobile app
Cons of Karma
- Not as many stores as other options
- App and extension can be a bit buggy.
- Sometimes the best products at retailers aren’t eligible for cashback.
Where to Download
Download Karma here.
4. Piggy

Piggy focuses exclusively on cashback opportunities from partner retailers. While it doesn’t have the resources and depth some of the other options listed have, it can still be useful to have in your cashback mix.
How Piggy Works
By acting as a highway hub for shopping traffic, piggy can cash in on affiliate relationships and pass some of that cash back to you. All you have to do is download the extension and wait to get pinged as you shop. If you do, then you have the option of buying through Piggy and earning cash back.
Pros of Piggy
- Free
- Convenient browser extension
- Automatic coupons
- Get paid via check.
Cons of Piggy
- $25 cash out floor.
- Not as many retailers as other options.
- Not well designed.
Where to Download
Download Piggy here.
5. RetailMeNot
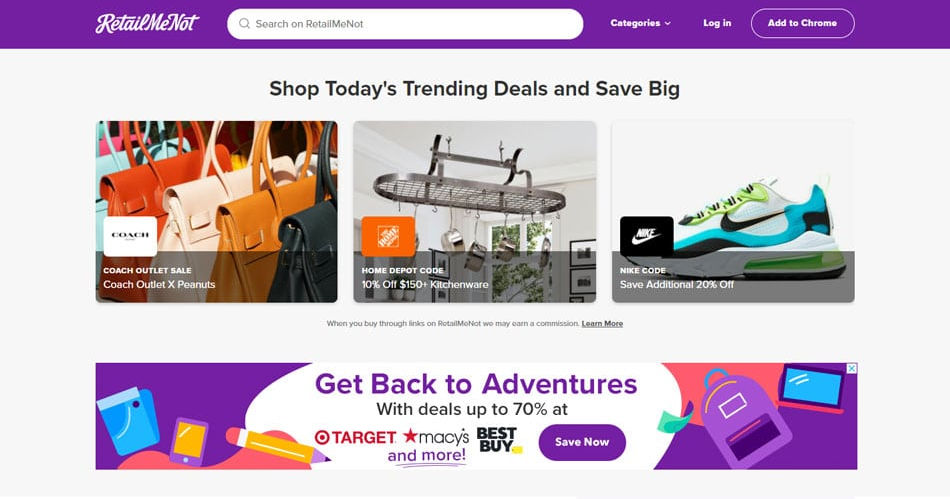
While RetailMeNot doesn’t have as many retailers as Capital One or Rakuten, they get their own exclusive deals and opportunities that are definitely worth keeping an eye on. They also release their own buying guides and offer advice on how to get the most out of your experience.
How RetailMeNot Works
Similar to Rakuten, RetailMeNot is best to use with a plan in mind. Apart from the extension, your best bet is to subscribe to RetailMeNot’s newsletter and check their website out periodically for any exclusive offers.
Once you see something that’s on your “dream” or “to-buy” list, you can snatch it up while the offer is good. Alternatively, you can just go to RetailMeNot to see if anything on sale catches your eye!
Pros of RetailMeNot
- Free
- Automatically applied coupons
- Exclusive deals
- Mobile app
Cons of RetailMeNot
- Only supported on Chrome
- Not as many retailers as some other options
- Site design isn’t as sharp
Where to Download
Download RetailMeNot here.
6. The Camelizer

The Camelizer is the browser extension for long-time Amazon price tracker CamelCamelCamel, and it’s a fantastic resource for seeing just how good that new “sale” is. For example, if you’re shopping a Summer sale in July, you can see if last year’s prices in the Fall were better than what you’re seeing now.
How The Camelizer Works
CamelCamelCamel is free for any user, and it’s best to use alongside the other options above. Consider CamelCamelCamel your coupon “hype manager.” In other words, it’s the voice of reason when an extension pings you with another AMAZING deal.
Because you can see just how good the deal is by comparing previous prices (assuming it was sold on Amazon), you can know if this is the sale to buy on or if you should wait for the next one. You can get all of that info by just clicking into the Camelizer on any Amazon listing. You can also set up specific price drop alerts on any items you know you want to buy as well.
Pros of The Camelizer
- Free
- Top price drops for best Amazon deals
- Awesome price history graphs
- Good for seeing how good a sale really is
- Works on Chrome, Firefox, Edge, Opera, and Safari
Cons of The Camelizer
- Design isn’t super friendly
- Is exclusive to Amazon
- No cashback or earning potential
Where to Download
Download The Camelizer here.
The Bottom Line on Apps Like Honey
Many of these apps function similarly, and each of them has different exclusive deals and events. So again, the ideal solution is actually a combination. Download a few of these extensions and compare them whenever you’re shopping to see what the lowest price is.
The best thing you can do when using these apps is get in the habit of checking these out before you actually order. In other words, once you know you’re going to buy something, take another 5 minutes and see if you can save some cash through these sites and apps! If you make this a buying habit, you’ll definitely save some dough.
What Is an Ad Blocker: Everything You Need to Know
Wherever you go, you will get bombarded with tons of ads on the internet.
While many of them provide value, the massive amount of advertisements can easily become disturbing for users as they try to enjoy their favorite activities in the digital world.
In fact, some publishers place so many ads in their apps and websites that it prevents users from enjoying the actual content.
Fortunately, using an ad blocker is an excellent way to remain (nearly) advertisement-free on the web.
In this article, we will explore what an ad blocker is, how ad blocking works, its benefits and downsides, as well as the actual methods to prevent advertisers from ruining your online experience.
The Problem With the Current Online Advertising Landscape
Before we dive into our topic, let’s first take a look at the problem ad blockers are meant to solve: the disturbing and intrusive nature of the current online advertising landscape.
Before the age of the internet, people encountered ads mostly in newspapers, on TV, radio, and billboards.
While the average person was exposed to between 500 advertisements a day during the 1970s, this number surged to a daily 5,000 by 2007.
With the rise of digital advertising, we now see an estimated 4,000-10,000 advertisements every day, which can be quite overwhelming.
And it’s no surprise.
It’s super easy for businesses to create, place, and show an ad to internet users by utilizing the advertising platforms of tech giants like Facebook and Google, which dominate the digital ad space.
Interestingly, even though the pandemic caused a huge hit to the online advertising industry, online ad spend still managed to grow by 1.7% in the US in 2020. In fact, Statista predicts worldwide digital advertising revenues to surge from 2019’s $333.8 billion to $491.1 billion by 2025 with a 5.67% Compound Annual Growth Rate (CAGR).
Due to the current nature of the online advertising landscape, consumers have developed strategies and mechanisms to cope with the massive amount of ads they encounter.
Much to the chagrin of advertisers, consumers are interacting with less and less ads, decreasing the return on investment (“ROI”) for advertisers, i.e., making advertising dollars spent less profitable for advertisers.
Consumers can hardly be blamed for wanting to distance themselves from online ads; indeed, they face numerous issues with the current state of digital advertising, including:
- Disturbing user experience: Imagine being bombarded by ads while reading this article with banners placed on the sides, the top, and the bottom of the page, as well as after every second or third paragraph. And, to make it extra annoying, imagine having to avoid the dreaded pop-up, which websites increasingly use despite the fact that pop-ups irritate about 73% of internet users, according to a HubSpot survey.
- Interrupting primary activities: In addition to being annoying, some ads even interrupt internet users’ primary activities. Take YouTube ads before videos or promotions in smartphone games as examples, which keep consumers waiting before they can access the publishers’ content.
- Slowdowns and battery drainage: While trackers and banners are being loaded, large numbers of unoptimized ads can appear and take their toll on applications’ and websites’ performance. According to an Opera study, a website is 51% slower on average when ads are displayed than with blocked advertisements. In addition to performance issues, the firm revealed that ads can also drain the battery life of devices by nearly 13%.
- Security concerns: In the past few years, malvertising has become a real issue for internet users. Malvertising refers to spreading malware and viruses via online advertising and was responsible for roughly 1% of the ad impressions in May 2019. In addition to infecting user devices, cybercriminals also use digital advertising to attract victims with fraudulent schemes.
- Lack of privacy: Have you ever visited an ecommerce store without making a purchase just to later encounter the same business’ ads on social media? Besides advertisements, most websites and platforms on the internet use web trackers to collect, store, and share data about the visitors’ online activities. As a result of exchanging user information with third parties, advertising networks know everything about you, diminishing your privacy on the web.
What Is an Ad Blocker?
An ad blocker is a software solution capable of preventing advertisements from showing for the user while browsing the web or utilizing an application.
Contrary to their name, most ad blockers do not actually block advertisements. Instead, they stop ads from downloading on your browser by disabling requests that include advertising-related content.
As a result, users can enjoy a mostly ad-free experience with enhanced security, privacy, and device performance without being exposed to intrusive content.
How Do Ad Blockers Work?
Ad blocking software solutions use simple filter lists containing URLs to identify and block advertisement-related content on websites and applications.
In web browsers, ad blockers work in the following way:
- Upon visiting a website, the ad blocker checks its filter list to see whether the site is included.
- If the search returns positive results, the ad blocking software blocks requests to external content, which prevents the advertisement from getting downloaded and shown on the page.
Instead of completely disabling the request, other ad blocking services replace the advertising content with something else after identifying it.
No matter the method used to disable advertisements, filter lists play a key role in the ad blocking process.
For that reason, filter lists are regularly maintained and updated by both the creators and third-party communities independent of the developers.
Most ad blockers allow users to whitelist the ads of different websites, services, and applications. By doing so, they can support the creators, prevent possible ad blocking-related page issues, or unlock the content of publishers that use ad block walls.
Many ad blockers provide protection against all kinds of intrusive content, such as advertisements, malware, and web trackers, across many applications, web browsers, and devices.
At the same time, some ad blocking software solutions can only disable unwanted content in specific apps and devices.
How Do Ad Blockers Make Money?
Not all ad blockers are created equal, as some are more effective in providing a distraction-free experience to users than others.
An excellent way to determine an ad blocking solution’s efficiency is by examining the service provider’s business model.
Ad blockers can make money in multiple ways, with the most popular methods including:
- Free: Some ad blockers function as open-source apps that are available to users for free. While they are maintained by the community, free solutions often finance their development via donations. A good example of this business model is uBlock Origin. However, strangely enough, the project’s creator doesn’t accept any donations. Instead, the developer decided not to create a dedicated website or a forum for the ad blocker in order to cut the maintenance costs.
- Paid service: Instead of resorting to the community’s help and donations, many ad blocking software solutions offer services in exchange for an upfront payment or a subscription fee.
- Freemium: Freemium is a popular business model among software solutions, and multiple ad blockers use it. Here, users can utilize only a part of the features for free. Optionally, they can pay a one-time or monthly subscription fee to access more powerful ad blocking functions.
- Whitelisting some of the ads: Certain ad blockers use a rather controversial business model. While they offer their services for free to users, the creators whitelist a share of ads that allegedly follow “acceptable” advertising practices. However, some ad blockers offer whitelisting services for advertisers in exchange for a payment or a cut from their ad revenue.
Why Do You Need an Ad Blocker and What Benefits Does it Offer?
An ad blocker is a must-have for those who want to enjoy an advertisement-free experience in the digital space.
Ad blockers offer the following benefits to users:
- Improved user experience: Users can achieve a distraction-and intrusion-free experience on the internet by using an ad blocker to eliminate advertisements. As a result, they can conveniently browse the web or use their favorite apps without worrying about getting bombarded by advertisers’ offers.
- Enhanced security and privacy: Most ad blockers have built-in features to detect, spot, and block malicious and fraudulent ads on the internet. In addition to eliminating malvertising, users can also enjoy increased privacy by disabling web trackers. Furthermore, ad blocking is an excellent way to protect children from inappropriate advertisements on the web.
- Faster page load times: Ad blockers can improve browsing speed and application performance by getting rid of bloated and unoptimized ads. While users have access to a more seamless experience, businesses can also benefit from the lower bounce rates achieved via faster page load times.
- Optimized battery life and mobile data usage: As ads take a heavy toll on device batteries, preventing them from loading can save energy and achieve better runtimes. The lack of ads can also reduce the mobile data usage of consumers.
- Potential savings on impulse shopping: By eliminating ads, the number of offers internet users encounter will significantly decrease. They can take advantage of this to reduce their unnecessary expenses, refrain from impulse purchases, increase their savings, and limit their chances of getting targeted by fraudulent companies.
What Are the Possible Downsides and Limitations of Ad Blocking?
As with every software, ad blockers have some limitations and downsides, such as:
- Broken content: Since ad blockers disable all advertising and tracking-related content of a website, it can lead to an unwanted experience on some occasions. When the app blocks an important request, the site may display broken content to the user.
- Inability to access content: As some publishers still utilize ad block walls, refusing to disable ad blocking software can prevent users from accessing certain apps and websites.
- Can’t block all ads: Unfortunately, although they can block most advertisements, ad blockers can’t provide a fully ad-free experience to users. Furthermore, the number of unblocked advertisements increases for ad blockers that adopt the whitelisting business model.
- Lack of support for content creators: Some content creators use digital advertising exclusively to monetize their solutions. Using an ad blocker without whitelisting them could reduce their revenue and limit their growth.
How Does Ad Blocking Impact Publishers and Advertisers?
According to Statista, ad blocking penetration was expected to surge from 2014’s 15.7% to 27% by 2021 in the United States.
In fact, ad blocking solutions were adopted much faster, with the technology’s penetration reaching 27% by February 2018 among US users.
Since many users are blocking ads on their devices, it has a major impact on advertising networks and businesses.
The good news for advertisers is that they don’t have to pay a dime for advertisements targeting ad block users (as they don’t get shown at all).
However, as a significant share of consumers have opted out of receiving ads from advertisers on the internet, this also means that businesses have a smaller audience to target.
At the same time, publishers are hit harder by ad blocking tech as a part of their visitors won’t interact with the ads displayed on their platforms, causing a revenue loss for the firms.
However, ad blocking impacts giant digital advertising networks (e.g., Facebook Ads, Google Ads) the most.
The more users install ad blockers, the fewer impressions and interactions advertisements get, decreasing the revenue networks make by connecting publishers and advertisers.
Countermeasures From Publishers
As ad blocking means a significant threat to the digital advertising industry’s current state, many publishers and networks have decided to take steps against ad blocker solutions.
One of the most popular ways publishers have used to reclaim their lost revenue is automatically detecting ad blockers upon user website visits.
When an ad blocker is detected, a publisher may decide to display a message to the user to convince him to disable the software.
However, others have taken a more harsh stance by installing an ad block wall that denies access to the site’s content until the user disables its ad blocking software.
While the latter method seemed to work initially, researchers discovered that 74% of users would leave a website with an ad block wall set up.
Due to these methods’ lack of success, businesses have joined initiatives like Acceptable Ads and the Coalition for Better Ads that require both publishers and advertisers to apply a variety of pro-consumer and user-friendly digital advertising standards.
By showing only heavily optimized ads to users, publishers of these initiatives can get their advertisements whitelisted as ad blockers participating in the programs.
What Are the Best Methods to Block Ads?
In this section, we have collected the best methods you can use to block ads in the digital world.
Let’s see them!
1. Browser Extensions
Examples: uBlock Origin, Adblock Plus, AdBlock
One of the most popular ways to block ads is by installing the software via a browser extension.
Here, the user visits its browser’s add-on store and sets up the ad blocker as a free extension.
Upon successful installation, the ad block browser extension will screen content for trackers, advertisements, and malware. After applying the filter lists, the ad blocker tells the browser whether to allow or disable an element.
Based on the rules the solution uses, it can leave whitespace where the ad would be normally displayed, replace it with other content, or just simply hide the element.
As a result, users can get rid of most ads while surfing the web via the browser where the ad blocker extension is installed.
On the other hand, since it’s a browser extension, the ad blocker doesn’t have access and can’t block unwanted content in other apps installed on the device.
2. Ad Block Browsers
Examples: Opera, Brave, Firefox Focus
Ad block browsers are internet browsers with built-in ad blocking capabilities.
They work very similarly to ad block browser extensions as they can effectively disable advertisements on the web.
While users don’t have to worry much about installing an extension to eliminate ads, browsers with built-in ad blocking features are often well-optimized and feature better performance than extensions.
It’s also important to mention privacy browsers. Instead of blocking ads, these solutions disable web trackers to ensure a high privacy level for users.
3. Mobile Ad Blockers
Examples: Wipr, 1Blocker, Blokada, AdAway
According to Statcounter, mobile devices have accounted for 55% of the internet traffic compared to desktop’s 45% in April 2023.
With smartphone devices taking the lead, it shouldn’t come as a surprise that mobile ad blocking has become popular among users.
In fact, while desktop was standing at 236 million, active mobile ad block users grew to 527 million by Q4 2019, according to PageFair’s 2020 AdBlock Report.
In addition to the web, mobile users encounter many ads within the apps they have installed on their devices.
For that reason, they can install an ad blocker for iOS or Android to disable ads both on the web and in applications.
As a side note, since browsers do not support extensions on some mobile devices, ad block browsers have become increasingly popular on smartphones.
If you want to learn more about mobile ad blocking, we recommend taking a look at the following Permission.io articles where we compared the best iOS and Android ad blockers.
4. Cross-Device Ad Blockers
Some ad blocking solutions offer protection against advertisements across multiple devices.
As a result, users can access apps and browser extensions on desktops, tablets, and smartphones to get rid of unwanted content with a single solution.
With a package of apps and browser extensions, cross-device ad blockers utilize various methods to eliminate advertisements.
On the flip side, cross-device ad blocking support is often a paid service without the option to access the service for free.
5. DNS Filtering
Examples: AdGuard DNS, DNSCloak
An effective method to block advertisements is via DNS filtering.
DNS stands for the Domain Name System that is responsible for matching domain names with IP addresses, allowing users to access content on the web without remembering the technical details and a confusing list of numbers.
The process works similarly to calling a friend. Instead of memorizing his number every time, you have it saved in your smartphone contacts so you can call him with a single tap. This is the exact reason why the DNS is often referred to as the “address book” of the internet.
With DNS filtering, the user connects to a DNS server configured to block access to either IP addresses or domain names seeking to display ads to the user. In addition to advertisements, DNS filtering also protects users from web trackers and malicious content.
When an app or a website sends an unwanted request, the modified DNS server refuses to reply with an IP address and instead sends a null response.
Similarly to browser extension-based ad blockers, the DNS filtering method also uses blocklists to identify and disable undesirable content. For that reason, the service provider must update the filter lists often to prevent advertisers from bypassing the DNS server.
Since DNS filtering blocks all unwanted requests coming from the web, this method can effectively provide system-wide protection against ads to internet users.
6. VPN
Virtual Private Networks (VPNs) are popular tools that allow users to disguise their online identity and encrypt their internet traffic.
To achieve that, the network redirects the user’s IP address through a configured remote server operated by a VPN host.
As a result, the VPN server becomes the source of the user’s data, helping to hide the data he or she sends or receives online from Internet Service Providers (ISPs) and other third-parties.
Since VPNs allow users to connect to servers in numerous countries and locations, they can use such solutions to bypass geo-blocks and access regional content on the web.
In addition to all the above, multiple VPN solutions feature built-in ad blocking to eliminate malware, trackers, and online advertisements.
While this method works similarly to DNS filtering, VPN ad blockers offer a one-stop solution to eliminating unwanted content and in apps across all devices connected to the user’s network.
However, for ad blocking to work, the user’s devices have to be continuously connected to the VPN network.
For that reason, it’s essential to test the performance of the VPN solution to avoid traffic-related issues and ensure a seamless user experience.
7. Hardware Devices
Examples: Pi-Hole
In the above sections, we have introduced software-based solutions to block advertisements on the web and in applications.
Now let’s examine a method that uses a hardware device for the same purpose.
Currently, the only viable hardware ad blocker on the market is called the Pi-Hole, which uses a Raspberry Pi to block advertisements on the network level.
For that, users have to configure the Raspberry Pi as a Pi-Hole, setting up a local DNS server that filters all content coming through the network and disables requests related to malware, advertisements, or web tracking.
Interestingly, the Pi-Hole replaces any pre-existing DNS server (including the ISP’s) on the user’s network with its own, allowing the device to block ads on devices like smart TVs that software-based ad blockers normally can’t reach.
While Pi-Hole is a free and open-source ad blocking solution, users have to purchase the necessary kit (e.g., a Raspberry Pi or another compatible device) to protect their networks against advertisements.
Also, as users have to manually configure the device to set up a Pi Hole, they have to possess at least minimal technical knowledge.
In terms of ad blocking, Pi Hole’s protection against unwanted content only works when the user is connected to his home private network (or the location where the device is installed to block ads).
Ad Blocking: The Key to a Distraction-Free Internet
Ad blocking is an excellent way to disable annoying advertisements, intrusive trackers, and malicious content. As a result of ad blocking, you can have a seamless, distraction-free experience while browsing the web or using your favorite apps on your device.
Additionally, ad blockers also improve your device’s performance, enhance your privacy and security, as well as limit your data and battery usage.
With that said, consider supporting your favorite content creators by whitelisting their advertisements via such an ad blocking solution.
An Alternative Solution to Preserving Privacy and Security
Meet Permission, the next-generation, blockchain-powered advertising platform that allows users to decide whether and how businesses can interact with their data and target them with ads.
In exchange for consenting to view an ad (which involves volunteering their time and data), users get rewarded in ASK cryptocurrency for engaging with advertisers and participating in their campaigns on Permission.
Users are free to hold, transfer, exchange, or spend their ASK rewards directly at Permission.io’s REDEEM store. Instead of forcing people to view their offers, advertisers on the Permission.io platform display relevant, personalized content exclusively to users who have given their permission to do so.
As a result, advertisers will experience increased engagement and ROI while building fruitful, long-term relationships with a loyal customer base.
Create an account at Permission!
Bitcoin Faucet List: 5 Best BTC Faucets of 2021
Are you looking to earn crypto without spending money to get some?
If yes, then you are in the perfect place.
In this article, we will explore Bitcoin faucets, one of the oldest and easiest ways to earn BTC for free.
After you learn what it is, we will discuss how to pick a great one, as well as provide you with a list in which we have collected the best Bitcoin faucets to get some free satoshi in 2021.
Let’s dive in!
What Is a Bitcoin Faucet?
A Bitcoin faucet is a website or an application that gives away small amounts of BTC in exchange for completing small, easy tasks.
Such tasks can range from completing surveys, solving captcha, viewing advertisements, playing games, or watching promotional videos about products or services.
Crypto enthusiasts coined the “faucet” name for such solutions, as the BTC rewards users can claim are so small that they can be characterized as tiny drops of water leaking from a faucet.
This is the reason why the Bitcoin rewards distributed via faucets are measured in satoshi, the smallest unit of the cryptocurrency equaling 0.000000001 BTC ($0.000036 at the current Bitcoin price).
Since the rewards are small for every Bitcoin faucet, you shouldn’t expect to get rich with such solutions.
As the popular phrase goes: “there ain’t no such thing as a free lunch.” This is especially true for the cryptocurrency industry.
While it’s possible to earn Bitcoin with faucets or other ways without investing funds, you still have to give something in exchange to get crypto.
In terms of BTC faucets, in most cases, you have to dedicate time to complete the small tasks given by the service provider. And, as another popular saying goes: “time is money.”
So, before jumping right into getting some free sats with a crypto faucet, it’s important to keep this in mind.
Interestingly, the history of Bitcoin faucets dates back to 2010, when early adopter and software developer Gavin Andresen decided to give away free BTC to kickstart the adoption of the cryptocurrency.
Until it was operating, Andresen gave away 19,700 BTC (worth $709 million right now) to spread awareness about crypto and blockchain technology.
While Andresen required users to solve a captcha only, it’s not a sustainable business model for most Bitcoin faucets (Andresen’s faucet has been defunct since early 2013).
For that reason, the BTC faucets operating today usually rely on third-party advertisements, affiliate marketing, and other sources of channels to remain profitable.
And this is the exact reason why most of them require you to do small tasks.
What Makes a Great Bitcoin Faucet?
Now that you know what a Bitcoin faucet is, let’s see what factors you should take into account when choosing one to use.
Before you jump right into earning some free BTC, you should consider the following:
- Claim amount: One of the most important factors when looking to make money is the actual sum you can earn. Each time you use a BTC faucet, you should check the claim amount to estimate your potential earnings. As a rule of thumb, the more complex a task is, the more satoshi you can get.
- Timer: Each Bitcoin faucet features its own timer that refreshes in certain periods, which can range from a few minutes to several days.
- Withdrawal method: Bitcoin faucets usually distribute rewards via standard BTC wallets (they keep your funds in micro wallets until reaching a certain threshold).
- Minimum withdrawal: Since service providers have to pay transaction fees after each crypto payment, they set minimum withdrawal amounts to save money on transfer costs.
- Referral fee: Many Bitcoin faucets feature their own referral programs that allow you to earn a commission in exchange for inviting other users to the platform.
- Reputation: While there are many legitimate Bitcoin faucets on the market, some are operated by fraudsters. For that reason, it’s crucial to choose a reputable provider that NEVER asks you to provide sensitive personal data or deposit cryptocurrency in order to earn money.
Next, you will find a list of the 5 best Bitcoin faucets currently on the market.
Let’s see ’em!
1. Cointiply: The Best Overall Bitcoin Faucet
Average claim amount: 200 satoshis per hour
Cointiply is among the most popular Bitcoin faucets on the market.
Founded in 2018, Cointiply is a feature-rich platform that offers one of the highest rewards, with average claims ranging around 200 satoshis per hour.
Featuring partnerships with numerous advertisers, Cointiply allows users to earn free BTC by completing tasks, such as participating in surveys, watching videos, playing browser games, and clicking on ads.
As soon as you reach 35,000 satoshis, you can hold your BTC in your micro wallet to earn 5% interest on your coins (you can even deposit more to increase your returns).
In addition to getting loyalty bonuses for logging into your account each day, you can earn reward points after “leveling up” by completing a certain number of tasks.
Furthermore, as its name suggests, Cointiply allows users to try their luck to increase their rewards by up to 61 times via a sci-fi-themed multiplier game.
Also, Cointiply pays a 25% commission after your referrals’ faucet rolls, while you can claim 10% of their earnings from offers and 0.25% of the coins they utilized to play the multiplier game.
The minimum amount is 50,000 satoshi to withdraw BTC directly to your wallet on the platform.
2. Bitcoin Aliens: The Best High-Paying Bitcoin Faucet
Average claim amount: 4,000 satoshis per hour
With the average claim amount being at 4,000 satoshis every hour, Bitcoin Aliens is among the highest-paying crypto faucets out there.
In addition to paying high sums, Bitcoin Aliens also offers a fun experience for users.
Instead of clicking on ads or answering surveys, Bitcoin Aliens rewards users in Bitcoin, Litecoin (LTC), and Bitcoin Cash (BCH) for playing games.
Most of Bitcoin Aliens’ games are available exclusively on Android, with the Temple Run-style Alien Run game being the only exception, which is available on both the App Store and Google Play.
However, you should keep in mind that Bitcoin Aliens makes money by collecting data while playing games on your smartphone.
According to the project, they have given away 1,090 BTC (worth around $40 million) since 2014 while featuring over 2.5 million users.
The minimum withdrawal amount for a direct transfer to your wallet is 30,000 satoshis for BTC, 10,000 satoshis for BCH, and 100,000 litoshis for LTC.
3. Bitcoinker: The Best Bitcoin Faucet for Sats Stacking
Average claim amount: 7 satoshis every 5 minutes (up to 100,000 satoshis)
With a long-standing history, Bitcoinker is a BTC faucet that offers users the easiest way to earn free coins by simply completing a captcha.
While the average payout is very small, Bitcoinker has a 5-minute timer, which means that you can use it to stack sats up to 12 times an hour.
Furthermore, Bitcoinker simulates a dice roll each time you solve a captcha with the potential to win 100,000 satoshis in every five minutes (although there’s a very low chance to achieve that).
While Bitcoinker offers a 10% commission after your referrals’ claims, the platform rewards you for being active with the option to receive up to a 30% bonus on your payouts if you maintain your seniority status for over 151 days.
The minimum withdrawal amount is 20,000 satoshi, which the platform automatically transfers to your BTC wallet on the first day of every month (when you are eligible).
4. BTC Clicks: The Best Bitcoin Faucet for Affiliates
Average claim amount: 1 satoshi per ad click (every 20 seconds)
BTC Clicks is also among the oldest crypto faucets on the market.
Similar to Cointiply, BTC Clicks also generates revenue via advertising. For that reason, you have to click on ads to claim free coins.
While each ad click rewards users only 1 satoshi, you can double your earnings by paying a subscription fee to become a premium user.
One of the best features of BTC Clicks is the platform’s high affiliate commission rate, which allows users to earn up to 160% (80% for standard users) of their referrals’ payouts.
The minimum withdrawal amount on BTC Clicks is 10,000 satoshi, which is sent instantly to your Bitcoin wallet after reaching the threshold.
5. Satoshi Quiz: The Best Bitcoin Faucet for Quiz Takers
Average claim amount: Up to 10 satoshis per minute
For those who love taking quizzes while stacking some sats, Satoshi Quiz is a no-brainer.
The platform displays a quiz every minute, which you have to answer correctly to have a chance at getting some BTC.
However, you not only have to answer it correctly, but you also have to be fast, as Satoshi Quiz distributes rewards to the first three users solving the quiz successfully (60% goes to the first, 30% to the second, and 10% to the third).
There are also daily, weekly, and monthly awards where users can win 100, 250, and 1,000 satoshis, respectively, with the prizes being distributed among the top 10 quiz takers.
On Satoshi Quiz, you get 10 lives every hour, from which you will lose one each time you answer a question incorrectly. If you run out of lives, you can either wait for the next hour to start or send a tweet to the project to get an additional five lives.
In addition to the main game, you can also participate in solo challenges where you have to answer 10 questions correctly to win 100 satoshis. However, unlike with standard quizzes, you need to pay a participation fee here.
The minimum payout on the platform is 11,000 satoshi. At the same time, Satoshi Quiz offers an affiliate commission of 20% for one year after a user invited by you registers a new account on the site.
Frequently Asked Questions (FAQ)
1. How do bitcoin faucets work?
Bitcoin faucets make money via advertising, affiliate marketing, and product promotions.
For that reason, most BTC faucets require users to complete small tasks, ranging from something as simple as solving a captcha to visiting certain links and watching promotional videos.
Before completing a task, most crypto faucet services require you to register an account and provide your wallet address.
After that, you can solve a small task to claim BTC, which will be transferred to a micro wallet until you accumulate the minimum amount of satoshi required to withdraw it to your wallet.
When that happens, the Bitcoin faucet will (either manually or automatically) transfer your earned BTC to your standard, third-party wallet.
It’s important to note that each Bitcoin faucet features a time-lock that restricts coin claims to certain periods (e.g., every five minutes).
2. Are bitcoin faucets worth it?
If you are looking for a get-rich-quick scheme or a ludicrous money-making opportunity, then Bitcoin faucets are not worth your time due to the limited amounts of BTC you can earn.
However, for those of you seeking to stack some sats or try cryptocurrencies for the first time, Bitcoin faucets could be a good choice.
That said, you should keep in mind that while you don’t have to spend money to get some BTC via faucets, you still have to dedicate time to complete tasks to earn crypto.
3. Are crypto faucets safe?
In general, reputable crypto faucets are considered safe as they operate via a viable business model through advertising and affiliate marketing.
On the other hand, there are also BTC faucets operated by fraudsters seeking to acquire your personal data or cryptocurrency funds via various schemes.
For that reason, it’s crucial to do your own due diligence before using a crypto faucet to choose a legitimate service and ensure your funds’ safety.
4. What is the highest paying bitcoin faucet?
Among reputable Bitcoin faucets, the highest paying solutions include Bitcoin Aliens and Cointiply, where the average claims are 4,000 satoshis and 200 satoshis per hour, respectively.
If you are lucky and hit the jackpot with your dice roll, you can earn as much as 100,000 satoshis on Bitcoinker.
Also, if you are an excellent (and super fast) quiz taker, then you have the potential to increase your BTC earnings on Satoshi Quiz.
Finally, if you have the time and patience, you can earn up to 180 satoshis per hour by clicking on ads every 20 seconds on BTC Clicks.
Bitcoin Faucets: An Easy Way to Stack Sats
With their history dating back to 2010, Bitcoin faucets provide an excellent opportunity for users to earn some free coins.
However, since the rewards are very small, you shouldn’t expect crypto faucets to provide a viable income. Instead, you will find BTC faucets most useful if you’re looking to dabble in crypto or stack some sats without spending any funds.
In any case, due to the fraud that often targets those in the crypto industry, we highly recommend doing your own due diligence to stay safe and pick a reputable service provider to earn free Bitcoin with a faucet.
Public vs. Private Blockchain: What’s the Difference?
When Bitcoin launched as the first implementation of the blockchain in 2009, distributed ledger technology (DLT) disrupted multiple industries.
From finance and banking to supply chain management and healthcare, organizations have been leveraging blockchain technology’s benefits to innovate, create more efficient services, as well as provide viable solutions to long-known issues.
That said, if you hear the phrase “blockchain,” probably the first thing that comes to your mind is a highly decentralized, open, community-governed DLT network like Ethereum or Bitcoin.
However, in addition to public blockchains, there is another form of the technology called private blockchains tailored for enterprise usage.
But what is the difference between public and private blockchains, how do they work, and what are their core features?
Let’s find out in this article!
What Blockchain Types Are Out There?
The blockchain refers to a digital ledger that is duplicated and distributed across the devices of all participants in the network in a way that everyone stores the same records and sees related changes in real-time.
But, did you know that there are four types of blockchain networks currently available?
That’s right.
Below, you can find all DLT variations with a small description for each:
- Public blockchains: Appeared with the launch of Bitcoin, public blockchains are open for anyone to join and use solutions within the network. Since DLT networks are transparent in nature, everyone can audit and monitor records on public blockchains. For this blockchain type, the read access is open.
- Private blockchains: Unlike their public counterparts, private blockchains restrict access for users, only allowing those within a specific organization or who have passed Know Your Customer (KYC) checks and have been approved by the system administrator into the network. For this blockchain type, the read access is closed.
- Permissionless blockchains: In a permissionless blockchain, anyone can participate in the consensus mechanism to validate blocks and transactions. Since there are no access controls in place for validators, the write access is open for this blockchain type.
- Permissioned blockchains: To achieve higher throughput and tailor DLT networks for enterprise usage, permissioned blockchains limit the number of validators while having access controls in place to select who can participate in the consensus mechanism. For that reason, the write access is closed for this blockchain type.
Since they are similar concepts, the terms private and permissioned, as well as public and permissionless, are often used interchangeably in the cryptocurrency industry.
However, they don’t exactly refer to the same thing.
While the public and private terms focus on whether a DLT network restricts read access for standard users, permissioned and permissionless refer to the presence of access controls for validators (write access).
Generally, all permissionless blockchains are public (open read and write access), and all private blockchains are permissioned (closed read and write access).
On the other hand, not all public blockchains are permissionless, as there are permissioned public DLT networks out there that allow anyone to join and audit the data on the chain but that restrict who can validate blocks.
In the next sections, we will focus on the differences between public and private blockchain networks.
Public vs. Private Blockchains: What Is the Difference Between the Two?
Both public and private blockchains leverage the benefits of DLT technology.
However, the core difference between the two is how they manage user access and whether they control who can validate blocks within the network.
What Is a Public Blockchain?
Examples: Bitcoin, Ethereum, Litecoin,
Most of the blockchain networks on the market are public, meaning that anyone with a working internet connection and a compatible device can access them along with the products, services, and apps in the ecosystem.
At the same time – since everyone keeps the same records on their devices and all modifications are transparently recorded on the digital ledger, users can inspect the data recorded on the public blockchain, trace transactions, and view other information.
Also, as there are no controls in place to restrict access for standard users (thus, no need for KYC), a higher degree of privacy can be achieved in the network.
When a public blockchain is also permissionless, it means that the network is not only free to access for standard users, but it lacks restrictions for validators as well.
As a result, everyone can participate in the consensus mechanism by operating a full node or mining or staking the platform’s native cryptocurrency.
Since the number of validators is high and there’s no central authority that selects them in public DLT networks, it allows for a great level of decentralization.
At the same time, this architecture provides enhanced security against attackers as they would need to take over the majority of the network to succeed.
What Are the Most Important Features of Public Blockchains?
Now that you know what public blockchains are, let’s see their most important features.
- Decentralization: In public blockchains, every user is equal without anyone having more authority than others. For that reason, and since nodes and validators are scattered all over the world, this DLT type is highly decentralized. Also, instead of a centralized company, most public blockchains are governed by the community who uses the chains’ native tokens to vote on upgrades and other important matters related to the network’s future.
- Privacy: In public blockchains, no KYC or any other forms of identity checks are needed to enter the network and use solutions within the ecosystem. As a result, users can achieve a higher level of privacy.
- Transparency: Since anyone can view and audit data on the blockchain, public DLT networks operate transparently. For that reason, it’s much easier to spot malicious, dishonest, and illicit activities in the ecosystem.
- Immutability: Due to the nature of the blockchain, once a transaction is recorded on the ledger, it can’t be altered in any way unless the majority of the validators agree to do so. Since public blockchains feature a massive number of validators, it’s almost impossible to tamper with data recorded on the ledger, making public DLT networks immutable.
- Censorship-resistance: DLT networks operated by centralized companies are often subject to regulations in some jurisdictions that could lead to some forms of censorship within the ecosystem. On the other hand, public blockchains leverage the power of decentralization to become entirely resistant to censorship.
- High Security: In addition to eliminating all risks of a single point of failure, the large-scale participation in the consensus mechanism makes it hard for attackers to take over the network. For example, they have to acquire 51% of the hash rate (the total computing power of devices connected to the network) to gain control of chains using the Proof-of-Work (PoW) consensus algorithm. However, if many miners are maintaining the network, it could effectively prevent such scenarios due to the potential costs of the attack. To achieve such against Bitcoin, an attacker would need to purchase 1.75 million of a popular mining rig that is priced at $10,000 each and feature a hash power of 100 TH/s (the current BTC hash rate is around 175 million TH/s). As a result, malicious parties would have to spend a whopping $17.5 billion to buy the hardware capable of taking over 51% of the network (and we didn’t even take electricity fees into account).
What Is a Private Blockchain?
Examples: Hyperledger Fabric, ConsenSys Quorum
While public DLT networks are meant to be used by the general public for all kinds of purposes, private blockchains are instead tailored for enterprise usage.
For that reason, private DLT solutions have access controls in place both for writing and reading.
This means only users authorized by the system admin can enter the network while the enterprise managing the ecosystem selects the validators that can participate in the consensus mechanism.
As a result, the organization can leverage the benefits of DLT technology while effectively safeguarding sensitive data recorded on the ledger.
To achieve that, everyone seeking to join the network must confirm their identities by submitting to KYC checks.
Upon the approval of the documents, the system administrator will assign different roles with various levels of access to participants in the ecosystem.
For example, while the enterprise may allow all its employees to view standard records, it may give only executives and top managers authorization to access sensitive data.As a result, the enterprise could keep everything under control by setting its own rules in the network.
Furthermore, enterprises not only choose who can validate blocks but also limit the number of validators that can generate blocks and verify transactions.
This gives private blockchains a significant advantage over their public counterparts in terms of scalability and throughput.
While it comes with increased centralization, the fewer the participants are present in the consensus process, the more efficient the network becomes, and the quicker transactions can be processed.
What Are the Most Important Features of Private Blockchains?
- Enhanced Scalability: By centralizing the consensus process, private blockchains limit the number of validators, making the network more efficient. As a result, high scalability and transaction throughput can be achieved at much better speeds than with public DLT solutions.
- The Ability to Prevent Unauthorized Access: Since only authorized users can use the network with different roles assigned to every participant, sensitive data recorded on private blockchains can be effectively safeguarded by restricting access for the general public, competitors, and malicious parties. Also, with an effective KYC process, enterprises can significantly minimize (or completely eliminate) the presence of illicit activities within the ecosystem.
- Cost-Efficiency: As the number of nodes is significantly limited (e.g., 20-30 vs. 10,000+ for public chains), it substantially reduces the costs of maintaining the network.
- Regulatory Compliance: Since most private blockchains are operated by businesses, they have to comply with regulations in multiple jurisdictions. While it may be hard to achieve that in a public DLT network, a private blockchain allows the enterprise to set and enforce rules according to regulators’ laws, frameworks, and policies.
- Enterprise Customizability: Since they have increased control over the network, enterprises can easily customize private blockchains to fit their needs.
Public vs. Private Blockchains: The Verdict
Both public and private blockchains have an important role in the industry.
While public DLT networks are more suited to fulfill the needs of the general public, private chains are tailored for enterprise usage.
Via an open, decentralized, transparent, and community-governed network, participants of public blockchains can benefit from increased privacy, censorship resistance, and enhanced security.
On the other hand, this DLT type lacks the level of customization for enterprises while suffering limited scalability and network efficiency.
Private blockchains seek to solve these issues by sacrificing decentralization and privacy to achieve better throughput at lower fees by limiting the number of validators.
At the same time, by performing KYC checks and setting their own rules and policies, enterprises can easily customize private chains to fit their preferences, comply with regulations, and prevent unauthorized access.
—
Frequently Asked Questions (FAQ)
1. Is Bitcoin a public or private blockchain network?
Bitcoin is a public blockchain that allows anyone to access the network as well as solutions within the ecosystem without any restrictions. Furthermore, you can also audit transactions, addresses, and other data recorded on the distributed ledger.
All you need is a compatible device and a working internet connection to do so.
In addition to being public, Bitcoin’s blockchain is also permissionless, which means that everyone is free to participate in the consensus process by running a full node or mining BTC.
2. Is a private blockchain centralized?
Since private blockchains have access controls in place for both validators and standard users – who have to be approved by the system administrator (a centralized authority) based on KYC documents –, private blockchains are increasingly centralized.
3. What is the use-case of private blockchains?
Private blockchains are tailored to fit the needs and preferences of enterprises, governments, non-profits, and other organizations.
Some example use-cases of private blockchains for businesses include supply chain management, digital identity, finance, B2B, healthcare, and food tracking solutions.
Permissioned vs. Permissionless Blockchains Explained
Bitcoin, the world’s oldest and largest decentralized cryptocurrency by market cap, utilizes the very first implementation of blockchain technology.
Along with most cryptocurrencies on the market, BTC features a permissionless blockchain network. Anyone with a working internet connection and a compatible device can access and maintain without restrictions.
In this way, BTC’s blockchain is different from permissioned blockchains, which are used mainly by businesses, governments, financial institutions, and consortiums.
Permissioned blockchains are distributed ledger technology (DLT) that sacrifice some degree of decentralization and anonymity to better suit business needs as well as achieve higher network speed and efficiency.
In this article, we will introduce permissionless and permissioned blockchains while exploring the core differences between the two DLT solutions.
What Is a Blockchain Network?
Before we dive deeper into our topic, let’s first revisit the basics of blockchain technology.
Pioneered with the launch of Bitcoin, a blockchain is a digital ledger that is duplicated and distributed across all participants’ devices in the network.
As a result, every change to the blockchain is recorded transparently in real-time on all participants’ ledgers. This means that everyone in the network sees an identical distributed ledger with the same records, allowing users to audit and trace back transactions.
Unlike in traditional networks where individual participants with the right access level can make changes to the server’s data, validators have to reach a consensus through a mechanism like Proof-of-Work (PoW) or Proof-of-Stake (PoS) to update the blockchain.
For that reason, once something is recorded on the distributed ledger, individual users can’t modify, delete, or tamper with the data, which makes the blockchain immutable by nature.
Furthermore, blockchains eliminate the single point of failure by maintaining the ecosystem via a vast network of computers.
Since thousands (or even millions) of devices scattered all over the world add new blocks to the chain and verify transactions, blockchains are more secure against cyberattacks, as hackers have to take over the majority of the network (instead of a single server) to gain control.
While all transactions are encrypted via public-key cryptography, blockchain networks operate continuously without third parties or middlemen.
What Is a Permissionless Blockchain?
Examples: Bitcoin, Ethereum, Litecoin
A permissionless blockchain is the type of DLT technology users in the crypto community are most familiar with.
And this shouldn’t come as a surprise.
Bitcoin, Ethereum, and the underlying blockchain networks of most cryptocurrencies use this form of distributed ledger.
In a permissionless blockchain network, anyone is allowed to participate and become a validator.
For example, if you have a compatible device and a working internet connection, you are free to create a Bitcoin wallet or even maintain the network by becoming a miner.
Permissionless blockchain networks completely lack access controls.
As a result, neither normal users nor validators have to verify their identities or submit Know Your Customer (KYC) documents to join. Instead, they can participate in the network while staying anonymous or pseudonymous.
What Are the Benefits of Permissionless Blockchains?
- Decentralization: Since there are no access controls or restrictions in place for validators, permissionless blockchain networks are truly decentralized. Every participant is equal, and no one can exercise increased authority over the others.
- Increased security: The lack of restrictions for validators incentivizes more participants to maintain the blockchain. For that reason, most permissionless ledgers feature an extensive number of validators, enhancing the network’s security.
- Privacy: As it’s not necessary for participants to provide any personal details or documents to join, permissionless blockchains feature increased privacy, allowing users to stay anonymous or pseudonymous while interacting with solutions in the network.
- Community governance: Instead of a company, government, or another centralized entity, most permissionless blockchains are governed by the project’s community.
- Censorship resistance: Due to the high level of decentralization and the extensive number of validators, permissionless blockchains are effectively resistant to censorship.
What Are the Downsides of Permissionless Blockchains?
- Limited speed and scalability: Since they feature a large number of validators who all need to reach consensus to process transfers and add new blocks to the chain, permissionless blockchains often face issues with limited scalability and transaction throughput.
- Risk of chain splits: In permissionless blockchain networks, the community must work closely together to maintain the ecosystem. However, heated debates and disagreements between miners can split the community and also the blockchain during hard forks (major upgrades that are not compatible with previous versions).
- Energy-efficiency issues: The Proof-of-Work (PoW) algorithm Bitcoin, Ethereum, and many other major blockchains deploy to reach consensus is highly energy-intensive as miners are required to operate physical equipment to solve complex mathematical puzzles. As a result, BTC mining consumes more energy than Sweden in a year. That said, many permissionless blockchains are upgrading their consensus mechanisms to more energy-efficient algorithms (e.g., Proof-of-Stake) to solve such issues.
- Risk of malicious activity: While most permissionless blockchains can effectively protect against hacker attacks, they can’t prevent cybercriminals from entering the network and targeting solutions in the ecosystem.
What Is a Permissioned Blockchain?
Examples: ConsenSys Quorum, Hyperledger Fabric, R3 Corda
Contrary to a permissionless network, a permissioned blockchain is a DLT solution with access controls in place for validators.
This could mean setting up a requirement to request KYC documents from all validators in the network.
Also, in most cases, the organization or the community managing the permissioned ledger chooses the users to validate blocks in the ecosystem.
Furthermore, permissioned blockchains limit the maximum number of validators in the network to increase efficiency as well as achieve higher throughput and scalability.
While some permissioned blockchains have access controls for standard users as well, others only restrict who can become validators (more on this later).
Unlike their permissionless counterparts that cater to the general public, permissioned blockchains are more suitable for enterprise usage as they can be more easily customized to fit individual business needs.
What Are the Benefits of Permissioned Blockchains?
- Enhanced scalability and speed: Permissioned blockchains feature only a small number of validators. As a result, they can reach consensus much faster than their permissionless counterparts while achieving high scalability and speed.
- Customizability: With access controls for validators, enterprises managing permissioned blockchains can set their own rules and customize the network to best fit their needs.
- Compliance: Permissioned ledgers provide enterprises increased control over the network infrastructure, which allows them to fulfill compliance requirements more efficiently.
- Limited malicious presence: With effective access controls for validators, permissioned blockchains can effectively eliminate (or at least limit) the presence of malicious parties in the ecosystem.
- Cost-efficiency: The small number of validators increases scalability and throughput and decreases the costs of operating the network.
What Are the Downsides of Permissioned Blockchains?
- Increased centralization: Chosen by the organization or the community managing the chain, only a limited number of validators can participate in permissioned networks. While the level of decentralization varies by the network, permissioned blockchains are more centralized than their permissionless counterparts.
- Less transparency: The transparency of permissioned blockchains is based on the organization itself managing it. While some enterprises may decide to maintain the same transparency as permissionless chains, others are reluctant to share information about their processes and procedures with participants.
- Lack of privacy: Since validators – and also standard users in some cases – have to go through KYC, permissioned blockchains feature limited privacy, making it nearly impossible for most participants to use the network pseudonymously.
- No resistance against censorship: As the network is managed by an organization that has to comply with regulations, permissioned blockchains could be subject to censorship in some jurisdictions.
- Potential security issues: With proper access controls, permissioned blockchains can maintain a high level of security in their networks. However, due to the small number of validators, a malicious party has an easier time infiltrating a permissioned blockchain than a permissionless ledger.
Permissioned vs. Permissionless Blockchains: What Are the Key Differences?
Now that you know the basics about permissioned and permissionless blockchains, let’s see the main differences between the two DLT solutions.
Access controls for validators
No. Everyone can become a validator in the network.Yes. The number of validators is limited, with the community or the organization managing the chain choosing who can validate blocks in the network.
Level of decentralization
High. Permissionless blockchains feature an extensive number of validators throughout the world.Limited. Due to the small number of validators, permissioned blockchains are increasingly centralized.
Governance
Governed and maintained by the communityGoverned by the members of an enterprise, government, consortium, or another organization
Security
High. The extensive number of validators eliminates the single point of failure while effectively securing the network from attackers.Varies based on the quality of access controls in the network. With proper management, a permissioned chain can achieve a high level of security.
Transparency
High. Every change is transparently recorded on the blockchain.Varies, based on the preferences of the organization managing the chain.
Censorship-resistance
High. Permissionless blockchains are unaffected by local regulations and can effectively resist censorship.Low. Enterprises managing permissioned blockchains have to comply with local regulations, which may involve requirements to censor specific network information in some jurisdictions.
Scalability and speed
Low. A large number of validators have to reach consensus, which decreases network speed and scalability.High. A small group of validators allows permissioned blockchains to function efficiently with enhanced scalability and speed.
Customizability
Low. It usually takes more time to push through major upgrades.High. Enterprises can easily set their own rules and customize chains to fit their needs.
Privacy
High. Users can freely join and participate in the network without passing KYC checks or confirming their identities.Low. Validators have to confirm their identities. Some permissioned blockchains have KYC requirements for standard users as well.Best suited forGeneral publicEnterprises, governments, consortiums, and financial institutions
Permissioned vs. Permissionless vs. Public vs. Private Blockchains
Public and permissionless, as well as private and permissioned, are concepts that are often used interchangeably for blockchain solutions in the crypto space.
However, there is a major difference between public and permissionless as well as private and permissioned blockchains.
Permissioned and permissionless are phrases used to describe whether a DLT network has access controls in place for validators. Simply put, these chain types have varying write rules.
While anyone can become a validator in a permissionless chain, users have to pass KYC checks and have to go through a voting process to validate blocks in permissioned networks.
However, the above two expressions do not cover whether a blockchain is open for standard users to participate.
When a blockchain is public, anyone can access the network and audit the data recorded on the distributed ledger. By nature, all permissionless chains are public.
On the other hand, private chains only allow select users into the network. In most cases, only those who have passed KYC checks and got approved by the administrator can join. Private DLT solutions restrict the read access for users.
Those without access can neither view data on the chain nor become validators in the network. For that reason, all private blockchains are permissioned as well.
On the other hand, there are public permissioned blockchains on the market that allow anyone to view records on the ledger and interact with solutions within the network but have measures in place to restrict who can validate blocks.
Both Permissionless and Permissioned Blockchains Play a Vital Role in the Industry
As the original implementation of DLT technology, permissionless blockchains feature a high level of decentralization, security, transparency, along with community governance.
On the other hand, permissioned ledgers sacrifice decentralization for higher speed, scalability, and customization. As they are increasingly centralized, many in the community argue that permissioned blockchains go against the core principles of crypto.
That said, like their permissionless counterparts that target the general public and serve a universal purpose, permissioned blockchains play an essential role in the industry by fulfilling the needs of enterprises that can customize them to better achieve their goals and objectives.
—
Frequently Asked Questions (FAQ)
1. Is Ethereum a permissioned blockchain?
Ethereum is a permissionless blockchain since it lacks access controls for validators.
Ethereum is also a public DLT solution since everyone with a working internet connection and a compatible device can join the ecosystem and interact with apps.
2. Is Hyperledger a permissioned blockchain?
While it is an open-source solution, Hyperledger is a permissioned blockchain that has been tailored for enterprise usage.
3. Is Bitcoin permissionless or permissioned?
Like Ethereum, Bitcoin is also a permissionless and public blockchain network, in which anyone can freely become a miner to maintain the ecosystem.
4. What is the biggest challenge of a permissionless blockchain?
While permissionless blockchains offer tremendous benefits to users, the biggest challenge they face is limited scalability.
Due to the extensive number of validators and the fact that all of them have to reach a consensus to verify transactions and add new blocks to the chain, permissionless blockchains are much slower than their permissioned counterparts.
With that said, many permissionless blockchains are working on fixing their speed-related issues by upgrading to more efficient consensus mechanisms and integrating off-chain scalability solutions.
5. What are the use-cases of permissioned blockchains?
Since they can operate at much higher speeds with enhanced scalability while sacrificing a level of decentralization, the main use-cases of permissioned blockchains are primarily for enterprises.
Examples of permissioned blockchain use-cases for businesses include farm-to-table food tracking, digital identity, supply chain management, and banking solutions.
What Is a Crypto Wallet? (2024 Edition)
Similar to how a bank account serves as your gateway to traditional finance, a cryptocurrency wallet is essential for managing and accessing digital assets in the blockchain ecosystem. In this updated guide, we’ll explore what crypto wallets are, how they work, and the latest advancements in their types and features. Whether you’re new to crypto or looking to expand your knowledge, this comprehensive overview will equip you with the information you need to navigate the world of crypto wallets in 2024.

What Is a Crypto Wallet?
A cryptocurrency wallet is a tool—usually software, sometimes paired with hardware—that allows you to interact with blockchain networks. It provides a secure way to:
- Send, receive, and store digital assets.
- Interact with decentralized applications (DApps).
At its core, a crypto wallet functions as your digital identity in the blockchain space, using cryptographic technology to secure your transactions and assets.
Public and Private Keys
Cryptocurrency wallets rely on public-key cryptography, which involves two key components:
- Public Key: This serves as your wallet address, akin to a bank account number. It’s safe to share with others for receiving funds.
- Private Key: This grants access to your wallet and allows you to sign transactions. Keep it secure and never share it.
For additional safety, wallets generate a seed phrase (a mnemonic recovery phrase) derived from the private key. This phrase is critical for wallet recovery and must be stored securely.
How Does a Cryptocurrency Wallet Work?
Wallets function by enabling secure interactions with blockchain networks. Here’s how a transaction works:
- Initiating a Transfer: Alice wants to send Bitcoin (BTC) to Bob. She inputs Bob’s public key (wallet address) and the amount.
- Signing the Transaction: Alice’s wallet uses her private key to create a digital signature.
- Broadcasting to the Blockchain: The transaction is transmitted to the network and validated by miners or validators.
- Confirmation: Once added to a block, the transfer is confirmed and completed.
Advancements in Wallet Security
Modern wallets have introduced features like:
- Multi-signature (Multisig) Wallets: Require multiple private keys to approve a transaction.
- Social Recovery: Designates trusted contacts to help recover your wallet.
- Multi-Party Computation (MPC): Splits private keys across multiple parties for enhanced security.
Types of Crypto Wallets
Hot Wallets
Hot wallets are connected to the internet and include:
- Desktop Wallets: Software installed on computers (e.g., Exodus, Electrum).
- Mobile Wallets: Apps for smartphones, often featuring QR code transactions (e.g., Trust Wallet, Guarda).
- Web Wallets: Accessed via browsers, offering convenience but lower security (e.g., MyEtherWallet).
Cold Wallets
Cold wallets are offline and provide maximum security:
- Hardware Wallets: Physical devices like Ledger and Trezor.
- Paper Wallets: Printed private and public keys (less recommended due to fragility).
DeFi Wallets
DeFi wallets enable interactions with decentralized finance platforms and Web3 applications. Examples include MetaMask and Argent.
Emerging Wallet Types
- NFT Wallets: Specialized for managing digital collectibles.
- Universal Wallets: Support multiple blockchains and assets in one platform.
What Are Crypto Wallets Used For?
Crypto wallets are versatile tools that enable:
- Storing Digital Assets: Safeguard cryptocurrencies securely.
- Transactions: Send and receive funds globally.
- DeFi Activities: Lend, borrow, stake, or yield farm.
- NFT Management: Buy, sell, and showcase digital collectibles.
- Payments: Use crypto for goods and services.
- Integrated Features: Access swaps, staking, and on-ramp services.
How to Choose the Best Crypto Wallet
When selecting a crypto wallet, consider the following factors:
- Security: Look for advanced features like 2FA, biometric authentication, and multisig options.
- Multi-Coin Support: Ensure the wallet supports all the cryptocurrencies you plan to hold.
- Ease of Use: Opt for user-friendly interfaces, especially if you’re a beginner.
- Integration with DApps: Check for compatibility with DeFi and Web3 platforms.
- Reputation: Choose wallets from well-established providers with positive reviews.

Security Tips for Crypto Wallets
- Backup Your Seed Phrase: Store it securely in multiple locations.
- Use Strong Passwords: Avoid common passwords and enable additional security layers.
- Keep Software Updated: Regular updates protect against vulnerabilities.
- Verify Addresses: Always double-check wallet addresses before transactions.
- Consider a Hardware Wallet: Ideal for long-term storage of significant funds.
How to Create a Crypto Wallet
For Custodial Wallets:
- Sign up on a trusted platform (e.g., Coinbase).
- Complete identity verification (KYC).
- Deposit funds to start using your wallet.
For Non-Custodial Wallets:
- Download the wallet app (e.g., MetaMask).
- Set up a new wallet and create a strong password.
- Save your seed phrase securely.
- Transfer crypto to your wallet.
Frequently Asked Questions (FAQs)
What Is the Safest Crypto Wallet?
Hardware wallets like Ledger and Trezor are considered the safest due to their offline nature and robust security measures.
Can I Use One Wallet for All Cryptocurrencies?
Yes, many wallets support multiple cryptocurrencies. However, ensure the wallet supports the specific coins you want to store.
Are Crypto Wallets Free?
Many software wallets are free, but hardware wallets require a one-time purchase.
Do Crypto Wallets Charge Transaction Fees?
Fees vary by wallet type. Non-custodial wallets charge network fees, while custodial wallets may have additional costs.
With this guide, you’re now equipped to choose, use, and secure your crypto wallet effectively. As the crypto landscape evolves, staying informed about wallet advancements will ensure you maximize the safety and utility of your digital assets.
NOTE: This article is updated from a previously published article on 4/27/2021.
Decentralized Finance: A Detailed Beginner’s Guide to DeFi
There has been quite some hype around DeFi in the crypto space.
And it’s no surprise.
While the total value locked in decentralized finance applications was standing at $671.3 million on January 1, 2020, the industry has grown to a $14.3 billion market by December 31. This represents a yearly surge of over 2,000%, which is over six times greater than Bitcoin’s 306% growth last year.
Since then, the decentralized finance market has continued its ambitious expansion, with users pouring $39.79 billion into DeFi apps by February 10, 2021.
But what is DeFi, how does it work, what benefits does it offer to users, and how did it manage to grow so big so fast?
Let’s explore the answers to the above questions together in this comprehensive guide about decentralized finance!
What Is DeFi?
Decentralized finance or DeFi refers to a movement in the cryptocurrency space in which alternative financial solutions are created using blockchain technology and digital assets.
With DeFi, anyone on the globe with an internet connection, a desktop or mobile device, and a compatible cryptocurrency wallet can access decentralized financial solutions.
DeFi apps allow users to manage their finances, get insurance, borrow, trade, and exchange digital assets or generate a passive income via various savings products while maintaining control over their funds.
DeFi solutions offer a great level of privacy to users, and most processes are automated and transparent.
Also, since DeFi apps lack intermediaries, they feature efficient networks with rapid transactions, reduced fees, and higher potential for profits.
What Is a DeFi Protocol?
A DeFi protocol or a DApp (decentralized application) refers to the actual solution that provides decentralized finance services to users.
Built on top of blockchain networks, DeFi protocols are operated using digital currencies and smart contracts. The latter refers to a self-executing and enforcing digital agreement between two or more parties.
While they are often used interchangeably, decentralized finance protocols shouldn’t be confused with DeFi platforms, which we will introduce in the next section.
What Is a DeFi Platform?
Unlike protocols, a DeFi platform refers to the blockchain network where the actual decentralized finance solution is deployed.
As decentralized finance applications are automated, smart contract support is mandatory for a blockchain network to become a platform for DeFi.
For that reason – and due to the massive activity on the blockchain –, Ethereum leads as the top DeFi platform with the vast majority (200) of decentralized finance solutions built on top of the project’s chain.
Interestingly, Bitcoin is the second most-used DeFi platform with 26 projects despite that its network doesn’t natively support smart contracts. However, with the Lightning Network’s introduction, it’s possible to run smart contracts and DeFi apps on BTC.
Coming next, the highly scalable smart contract platform EOS secures third place with 21 DeFi projects.
DeFi vs. Traditional Finance: How Does Decentralized Finance Work?
To understand our topic, it’s crucial to know how decentralized finance solutions work compared to traditional finance approaches.
Traditional Finance
Traditional finance products – such as loans, savings accounts, wealth management, banking, and insurance – operate on a centralized basis.
The service provider has full control over the ecosystem and the authority to set its own rules and terms. For that reason, the company has the right to provide or restrict the access of customers to its products and services.
For example, let’s see how a loan application process works in traditional finance.
- You make an appointment with your bank, visit the branch to answer several questions, and fill out the necessary forms.
- After that, you have to submit documents to the bank.
- The financial institution reviews the submitted papers along with your credit history and other data related to your financial background to determine your eligibility for the loan.
- If the bank finds everything okay, it issues you the loan and transfers the requested funds into your account, which you will have to pay back along with interest.
However, if the bank finds it too risky to lend you money, it will deny your application.
Denial can be due to many reasons, including bad credit history, insufficient collateral, low income, too many pending loans, or an unstable job. In other cases, the financial institution may reject your application for a cause they won’t inform you of.
As you can see, the whole process – which can take from a few days to several weeks – is definitely not transparent or democratic. The bank is in charge of everything, focusing on maximizing its profits while taking the least amount of risks.
While we can’t judge banks for doing so – as most companies follow the same practice to run a profitable business – banks deny access to traditional finance products for many people. And, sometimes, those who get rejected are the ones who need those services the most.
Also, some traditional finance products like lending are only accessible domestically due to regulations and the inability to determine an applicant’s credit score on an international basis.
DeFi
In the last section, we described an example of how a loan application is processed in traditional finance. Now let’s see how borrowing with DeFi works:
- A user connects a compatible cryptocurrency wallet to a DeFi lending platform to access the app.
- Upon successfully connecting the wallet, the user selects the digital asset and the amount of coins to use as collateral and deposits it into a smart contract on the lending platform.
- When the coins have arrived, the user selects the amount of stablecoins (e.g., DAI, USDT, USDC) to borrow as well as sets and agrees to the loan’s terms.
- After finalizing the process by tapping or clicking a button, the platform automatically locks the customer’s collateral and distributes the borrowed amount to the user from a lending pool.
- The user pays back the borrowed amount and the corresponding interest according to the terms agreed in the contract.
- Upon successful repayment, the lending platform automatically releases the borrower’s collateral.
- Contrary to traditional finance, the whole process in which the user applies for and gets the loan issued takes only a few seconds or minutes.
Furthermore, the process doesn’t involve any intermediaries, and everyone with the necessary digital asset collateral can receive a loan with flexible terms vis-a-vis DeFi solutions.
What Are the Benefits of DeFi?
DeFi solutions provide multiple benefits to users, including:
- Decentralization: DeFi solutions function as decentralized applications (DApps) that are deployed on blockchain networks. Unlike traditional systems, where data is stored on a central server or database, blockchains are maintained by a decentralized network of computers (the miners or validators).
- Transparency: Since DeFi solutions are blockchain-based, everyone maintains the same copy of the blockchain, storing all the data and recording changes to the distributed ledger in real-time. All this information is available for anyone on the public chain to verify, audit, and analyze transparently.
- Immutability: In blockchain networks, validators have to reach a consensus to verify transactions or add new blocks to the chain. As a result, once a record is added to the distributed ledger, it is immutable and can’t be modified.
- Open access: DeFi DApps are deployed on permissionless blockchains such as Ethereum. As a result, anyone with a compatible device, cryptocurrency wallet, and an internet connection can access DeFi solutions globally without geographical, financial, or other restrictions.
- Democratic governance: Instead of a company or a financial institution, most DeFi products are governed by the community. Here, holders can use their tokens to vote on future protocol upgrades, fixes, and other governance-related decisions. However, it’s important to mention that not all DeFi projects start as community-powered solutions. Instead, they initially use a centralized governance model (e.g., a developer or an organization is in charge). But later, the creator hands control over the project to the community by issuing and distributing native tokens to users.
- Interoperability: One of the most important features of DeFi is interoperability, which allows developers to build upon, integrate, or combine DApps with other decentralized finance solutions. This is the reason why DeFi protocols are often called “money legos” in the crypto space.
- Programmability: Developers can deploy smart contracts for DeFi solutions to automate processes and create new products.
- Non-custodial finance management: Traditional finance solutions – and even centralized exchanges – keep their customers’ funds in their custody while using their products (take savings or bank account as an example). On the other hand, most DeFi applications don’t hold user funds. Instead, they operate on a self-custodial basis where customers have to connect their wallets without depositing money to accounts managed by the service provider. For that reason, users have full control over their digital assets and personal data when they use DeFi apps.
- Privacy: Since DeFi solutions have no custody over customer funds, they don’t require users to register accounts, provide personal details, or submit Know Your Customer (KYC) and Anti-Money Laundering (AML) documents. For that reason, it’s possible to use decentralized finance services privately or (pseudo)-anonymously. However, that can change soon based on the outcome of future regulations.
What Are the Use-Cases for DeFi?
Empowering DeFi with numerous use cases, projects have been taking the lead to create decentralized alternatives to traditional finance solutions.
In this section, we have compiled the most important DeFi use cases along with example apps for each.
Let’s see them!
1. Lending and Borrowing
Examples: Aave, Compound.Finance, Oasis
One of the most popular DeFi activities is lending and borrowing.
And for a very good reason.
Earlier in this article, we have shown how borrowing works on DeFi platforms, and we can safely conclude that it’s a rapid, efficient, and automated process that lacks any middlemen and allows borrowers to access extra capital in stablecoins within a few minutes.
However, it’s important to mention that DeFi loans are overcollateralized, meaning that borrowers have to deposit more collateral than the amount of funds they can borrow.While this may seem counterproductive at first, over-collateralization protects lenders against non-paying borrowers (as the collateral is automatically transferred to the lenders upon non-payment).
On the other hand, crypto-backed loans in DeFi allow investors, traders, and businesses to access extra capital – which they are free to exchange for fiat currency any time (e.g., to pay rent, utility bills, business expenses) – without selling their digital assets.
DeFi platforms issue loans from lending pools in which users deposit their cryptocurrency holdings (usually stablecoins). In exchange for contributing coins to a pool, lenders can earn interest on their tokens.
Interestingly, one of the reasons why DeFi lending has become so popular is due to the fact that users have access to much higher interest rates (usually ranging between 5-15% annually) than with traditional finance products (e.g., government bonds, savings accounts).
2. Decentralized Exchanges (DEXs)
Examples: Uniswap, Bancor, Kyber Network
A decentralized exchange or DEX is a peer-to-peer (P2P) cryptocurrency service that allows buyers and sellers to connect without intermediaries and the requirement to hold user funds in custody.
Instead of relying on centralized elements, decentralized exchanges execute trades automatically using smart contracts.
While DEXs are not new, they only played a minor part in the crypto space until the recent DeFi boom, which helped them gain ground against centralized exchanges.
A reason why decentralized exchanges initially lagged in adoption in the crypto community is because of issues with liquidity.
However, since DeFi solutions introduced liquidity pools, incentivizing users to contribute their coins in exchange for an interest, DEXs now have access to significantly more liquidity than before.
Furthermore, many decentralized exchanges have started supporting atomic swaps, in which crypto users can conveniently and instantly switch a token to another coin.
3. Derivatives and Margin Trading
Examples: Kwenta, Hegic, dYdX, Fulcrum
Cryptocurrency derivatives and margin trading have become increasingly popular in the industry.
In short, a “derivative” is a financial instrument that derives its value from the performance of an underlying asset, which can be anything from stocks and bonds to Bitcoin and DeFi tokens.
“Margin trading” refers to the practice in which someone uses borrowed funds to trade an asset, allowing him to secure higher potential gains (that also comes with greater risks).
While such products were only available for the public with centralized providers in the past, DeFi creators have recently introduced decentralized derivatives and margin trading platforms where users can trade assets without KYC and custody requirements.
4. Stablecoins
Examples: USDT, DAI, USDC
Stablecoins are cryptocurrencies that have their values pegged to a single or a basket of other instruments.
Although the underlying instrument can be virtually anything (e.g., other digital assets or commodities like gold and silver), most stablecoins are based on major fiat currencies, such as USD and EUR.
As their name suggests, stablecoins provide a solution to cryptocurrencies’ volatility issues by pegging them to assets that aren’t subject to extreme price swings to stabilize their value.
While their value remains steady, stablecoins can be held, used, exchanged, and transferred via blockchain networks just like any other digital asset.
Stablecoins play a key role in DeFi as they are widely used across lending, payment, and yield farming solutions.
5. Staking
Examples: Staked, Stake Capital, P2P Validator
Staking refers to locking up a part of a user’s cryptocurrency holdings to validate blocks and get rewarded for supporting the blockchain network.
Staking has the same purpose as mining in Proof-of-Work (PoW) networks like Bitcoin, in which miners leverage their computational power via specialized hardware to verify transactions and add new blocks to the chain.
However, validators in Proof-of-Stake (PoS) networks and their variants use their tokens instead of their computational power to validate blocks.
Unlike cryptocurrency mining, where miners have to purchase expensive equipment to get started, staking has no upfront costs for validators. For that reason, it is more accessible to users, and it has gained increased popularity in the digital asset space.
As only selected validators are rewarded, individuals and companies have created staking solutions to maximize their profit chances. As a result, users can make a similar passive income as in DeFi lending.
Although, it’s important to mention that while lending involves mostly stablecoins, staking requires locking up a project’s (non-stablecoin) token. This increases the risks of volatility but also the chance for increased returns (in case a staked coin’s value moves in a favorable way while being locked up).
6. Yield Farming
Examples: Curve, Harvest Finance, SushiSwap
Yield farming is a DeFi-exclusive activity that is widely popular in the industry, especially among those with a higher risk appetite.
Yield farming, also called liquidity mining, refers to using complex strategies to lend and stake digital assets throughout multiple DeFi protocols to maximize gains.
In its basic form, farmers deposit (lend) their funds into liquidity pools to earn rewards. However, in many cases, the platform issues a token to the user representing the coins he has lent to the pool (e.g., for lending DAI on Compound, users are issued cDAI).
Since users are free to utilize these tokens in other DApps, many yield farmers move them to other DeFi solutions to make an additional profit. And they may continue to do so with the coins they get on the second protocol.
However, as the most profitable strategies involve multiple (non-stablecoin) cryptocurrencies, they pose much higher risks to users than, for example, DeFi lending or staking.
7. Wealth Management
Examples: Argent, Trust Wallet, DeFi Saver
Cryptocurrency wallets have been around since Bitcoin’s launch in 2009, allowing users to store, receive, and send digital assets.
However, the original crypto wallets are very different from the ones we have now.
With the rise of the DeFi space, many cryptocurrency wallets have added a functionality that allows users to interact with decentralized finance applications.
Many DeFi-compatible crypto wallets now function as one-stop wealth management solutions by integrating multiple apps under one platform.
In addition to the basic features, users can now utilize their wallets to trade, swap, stake, yield farm, or lend cryptocurrencies.
Furthermore, some decentralized finance projects have created specialized wealth management apps that can be connected with DeFi-compatible wallets.
8. Payments
Examples: Lightning Network, Matic, Whisp, Request
In addition to a store of value, one of the first use cases of cryptocurrencies was for payments.
Since blockchain networks operate continuously without intermediaries, they offer global access to faster and cost-efficient payments to crypto users.
However, due to blockchain networks’ decentralized architecture, digital assets often struggle with decreased scalability and congestion.
Multiple DeFi projects are working on Layer 2 scalability solutions to fix this issue, allowing transactions to be processed on side-chains or off the main blockchain. As a result, users can have access to cheaper and more rapid transfers.
In addition to scaling solutions, other DeFi projects have created payment applications to facilitate efficient digital transactions for individuals and businesses.
9. Asset Tokenization
Examples: Neufund, Securitize, Polymath
Asset tokenization refers to the practice in which the rights for real-world or traditional finance assets are converted into cryptocurrencies.
Theoretically, there are no limits for tokenizing instruments. From artwork, in-game items, to real estate and commodities, anything can be “moved” to the blockchain to be represented by a token.
However, asset tokenization creates the most value when hardly accessible or illiquid instruments are converted into cryptocurrency.
As a result, such assets can be exposed to a larger market, making it much easier for users to buy or sell them.
For example, tokenizing private companies’ shares can be used to create a secondary market in which participants can easily exchange them. Real estate is another good example of an illiquid asset that can be improved by tokenization.
10. Insurance
Examples: Nexus Mutual, Etherisc, Cover
Insurance is among the most interesting applications of DeFi solutions.
It was not common to hear about insurance products other than traditional finance before the DeFi boom.
As some decentralized finance products involve increased risks, projects have created insurance products to protect investors against potential losses.
However, DeFi insurance solutions are very different from the ones in traditional finance.
Instead of a single firm providing the service – with the involvement of several sales agents and other intermediaries – decentralized insurance products are managed and offered by the community.
Interestingly, in addition to crypto-related activities and services, DeFi insurance products have been created around other, more general areas like flight delays and hurricane protection.
Is DeFi Safe for Investors?
At this point, you know what DeFi is, how it works, as well as its benefits and use cases.
Now let’s talk a little about the safety of the industry.
Whether DeFi is safe for investors is based on the strategies and the actual decentralized finance solutions used to generate potential profits.
For example, lending a stablecoin on a major, reputable DeFi protocol poses relatively low risks to investors as the loans’ over-collateralization protects them against non-paying borrowers.
Also, as stablecoins are subject to minimal volatility – especially when we compare them to DeFi tokens with small market caps – investors don’t have to worry about potential price swings that could eat up their profits.
On the other hand, using a complex yield farming strategy that involves lending, staking, or trading 3-4 different non-stablecoin tokens can come with very high risks.
For that reason, DeFi is definitely risky for investors who don’t do their own due diligence before using an app.
However, DeFi can be a safe investment for those who know how different smart contracts and DApps manage their money, refrain from utilizing overly complex strategies, understand the risks beforehand, and engage with only reputable service providers.
With that said, we have collected for review some of the potential challenges and risks of DeFi:
- Smart contract bugs: As mentioned earlier, DeFi applications are powered by smart contracts, allowing both users and service providers to automate processes. However, everyone makes mistakes, including developers, especially in the case of complex smart contracts. Smart contract bugs are often hard to fix and can lead to potential exploits and investor losses.
- Hacks: Unfortunately, errors in smart contracts are still common among DeFi projects. For that reason, hackers are increasingly targeting the space, aiming to exploit the vulnerabilities of projects.
- Fraud: The DeFi space is yet to be regulated, and some projects are taking advantage of the current situation to scam investors with fraudulent schemes.
- Future compliance issues: Currently, there is no regulation around DeFi. However, since the industry is growing rapidly, it is realistic to expect multiple governments to regulate decentralized finance in the near future. While effective regulation is definitely good for the space, DeFi users may lose some of their abilities, such as using solutions without submitting KYC and AML documents.
- Impermanent loss: Impermanent loss is a unique term used in DeFi and applies to mostly yield farming activities. In short, an investor can face this risk while supplying liquidity to a pool. Impermanent loss occurs when a token in the pool grows in value and arbitrageurs step in and use the opportunity to make profits, reducing the liquidity provider’s gains. In such a case, an investor could have made a better profit by holding the tokens in the pool instead of supplying liquidity. If you want to learn more about impermanent loss, we recommend reading the following article.
How to Stay Safe in the Decentralized Finance Industry
Based on our findings in the previous section, we can conclude that the decentralized finance industry poses some risks to investors.
However, it’s definitely possible to stay safe while using DeFi services, and we have collected some handy tips to help you:
- Do your own research before using an app: While this may be obvious, many people forget to do their own due diligence before utilizing a solution or investing in something. This advice is especially crucial for DeFi apps, as they often use complex mechanisms and business models to operate. For that reason, make sure you understand the strategies and the decentralized solutions used for investing to know your opportunities and risks beforehand.
- Be cautious with solutions promising extraordinarily high rates: If something seems too good to be true, it probably is. For that reason, you should take DeFi projects promising excessively high returns (e.g.,1,000% gains in one week) with a grain of salt. When you find a new app, analyze how it works, do a background check on the developers, and see what others say to stay safe.
- Check smart contract audits: Since smart contract bugs pose a high risk to the industry, DeFi projects often hire third-party firms to audit their code to find and fix potential issues and vulnerabilities. As a rule of thumb, you should refrain from using DeFi services without audited smart contracts. To get increased insight into a project’s safety, we recommend going through all audit-related documents.
- Consider DeFi insurance products: Buying insurance for a DeFi product is a good way to protect your investment against possible cyber-attacks and smart contract failures.Stay away from projects with anonymous owners: While Bitcoin has proven itself a trustworthy project since its launch by the mysterious Satoshi Nakamoto, it doesn’t mean that you should blindly trust DeFi projects where core developers refuse to reveal their identities. On the contrary, you should be very careful as the risks of exit scams and other fraud is higher for solutions with anonymous dev teams.
- Look for activity on GitHub: Since DeFi projects are open-source, their code and related developer activities are shared publicly on GitHub. For that reason, it’s possible to see the newest changes to the apps there. If a project hasn’t made any updates to the code in the past few months, it means that it has likely been abandoned by the team.
How to Get Started With DeFi
Now we have explored the industry’s essentials, let’s see how to get started with DeFi.
Step 1: Create a DeFi-Compatible Wallet
The first step to use a DeFi app is to create a compatible cryptocurrency wallet.
Argent and Trust Wallet are good examples that you can download as an app on your smartphone.
However, if you want to maximize your security, consider getting a hardware wallet from a reputable provider like Ledger or Trezor. Since hardware wallets are popular among crypto users, most DeFi applications support them.
After creating your wallet, you will be given a seed phrase. Since this crucial piece of information allows you to restore your account, it’s important never to share it with anyone.
Instead, you should write it down on a piece of paper and store it in a place you have exclusive access to. It’s also a good idea to keep it digitally on your computer’s hard drive in a secure location as well (never upload it to the cloud as it could compromise your security).
As a side note, some crypto wallets use their own security features for restoring accounts and may not offer seed phrase backups for customers. These solutions often use guardians (e.g., a hardware wallet, a trusted person, or a third-party service) to restore user wallets.
Step 2: Get Cryptocurrency
When your wallet is ready, it’s time to get some crypto to use for DeFi.
The easiest way is to purchase coins with fiat currency.
For that, we recommend using a trusted digital asset exchange (e.g., Coinbase, Kraken, Binance) where you have multiple options to purchase cryptocurrency with fiat.
The easiest and the fastest way to exchange fiat to crypto is via a credit or debit card, but this option is often more expensive than the others.
On the other hand, if you are comfortable waiting a few days until you can purchase crypto, bank transfers are a great option, especially when you can access domestic wire transactions.
It’s possible to get digital assets via other methods (even without spending a dime), such as by stacking sats.
For earning digital assets, we recommend checking out the next-generation, blockchain-based advertising platform Permission. In exchange for your data and time, you can earn native ASK cryptocurrency by engaging with advertisers’ ads.
Most importantly, you are the one in charge of whether and how advertisers can use your data on Permission.io.
You can spend your rewards for products listed in the Shop & Earn Store anytime to earn back up to 20% of your ASK purchases.
Oh, and we almost forgot: you can get 100 ASK for simply registering a new account at Permission!
Step 3: Connect to a DeFi App
When you have your coins ready in your wallet, it’s time to select a DeFi app to use.
On mobile, the connection between your wallet and the decentralized finance app is mostly established with WalletConnect, a service combining multiple wallet and DeFi solutions. Here, you have to scan a QR code with your smartphone’s camera to access the service or log into your account and authorize the DeFi app for desktop and web wallets.
The process is a bit more complex for hardware wallets as you have to plug your device into your computer and type in a security key for connecting to the DApp.
Don’t forget to confirm the connection in your wallet app to finalize the process.
Step 4: Deposit Funds
Once you have established the connection between your wallet and the DeFi service, you have to deposit funds to utilize it.
However, unlike with centralized exchanges, this deposit will go into a smart contract instead of the service provider’s accounts, which allows you to remain in custody and maintain control over your digital assets.
After initiating the deposit from the DeFi app, you will have to authorize it via your wallet.
Upon a successful deposit, you are ready to lend, exchange, borrow, stake, farm yield, or participate in other decentralized finance activities.
After ending your DeFi journey, don’t forget to withdraw your funds to your wallet.
DeFi Is Here to Stay
DeFi has empowered crypto with numerous new use-cases by providing a decentralized alternative to traditional finance products.
While there is significant demand for them, traditional finance services often operate inefficiently, lack transparency, need middlemen, and fail to provide access to many.
DeFi solves this issue by leveraging blockchain technology to provide a wide range of services, allowing users to manage their finances, access savings products with good rates, and borrow funds on their digital assets.
With such astonishing growth in recent months and new use cases and solutions appearing on the market every day, DeFi is definitely here to stay.
Notwithstanding their increasing popularity, DeFi solutions can come with high risks to investors. For that reason, we recommend everyone to do their own due diligence and follow the best practices to stay safe while taking advantage of decentralized finance’s benefits.
—
DeFi Frequently Asked Questions (FAQ)
1. How much money is in DeFi?
As of March 24, there is $40.82 billion of digital assets locked in DeFi apps.
2. What is decentralized technology?
Solutions using decentralized technology lack a central party (e.g., a company, institution, government body) from their networks that can exercise its authority over other users.
Instead, applications using decentralized tech are maintained by the community and governed democratically.
Blockchains and DeFi protocols are good examples of decentralized technology.
3. What is an example of a decentralized exchange?
Examples of decentralized exchanges include:
For more examples and to learn more about decentralized exchanges, we recommend reading the following article on the Permission blog.
4. Are banks centralized or decentralized?
Banks and the banking network operate on a centralized basis.
Financial institutions have full control over their governance, products, networks, services, as well as who can get access to their solutions.
While the DeFi industry is growing rapidly, decentralized banks are yet to appear on the market or gather widespread attention among users.
The Medium Is The Message – Ask Permission
Functionally speaking, what is Permission?
Permission is a medium. A medium that connects brands and consumers. That is all.
Permission is a new kind of medium, but there have been many other kinds of mediums before it. Long ago, books were one of the most common mediums. After that, radio, then TV, and finally the voluminous hosts of mediums that have popped up on the Internet, like blogs, Facebook, forums, YouTube, and much more. And Permission is now one of these mediums.
Yet it was once famously said by Marshall McLuhan, “The medium is the message.”
Don’t be afraid. This may seem like some deeply cryptic philosophizing at first, yet it is actually surprisingly simple to unpack. What McLuhan really means when he says this is that:
“The way that we send and receive information, is more important than the information itself.”
Let that sink in for a second.
Have you ever caught yourself endlessly scrolling through Instagram and simply lost track of time? When you eventually awake from your fugue state, you will likely have forgotten 99% of the content that you consumed. Yet you will invariably be left with the distinct feeling of “FOMO” impressed by the medium itself. That is what McLuhan means when he says, “The medium is the message.” The underlying messages of Instagram are: “You need to travel more. You need to be more popular. You need to be more beautiful. You need to have a more interesting and exciting life.”
And these mediums that we engage with actually change the way we behave. A person who spends their whole day on TikTok may be more likely to seek attention and immediate gratification than one that just listens to Podcasts, because those implied messages have burrowed their way into your subconscious. Take this in contrast to an older medium, like books. Books are a calm, understated medium that requires proficiency in linguistics. Books invite you to spend a great deal of time to fully digest the content therein. The underlying message of books is: “Dedicate yourself and be rewarded with deep understanding.”
As you could have guessed, each new medium which has caught on over the past several decades seems to have brought with it a more distressing and demanding message. Just as Radio was supplanted by TV, and TV by the Internet, we have grown slowly accustomed to being barraged with messages from others who seek to influence us. No matter which modern medium we turn to, we receive the messages that trust is elusive and that we are relatively worthless.
So, what then is the message of Pemission?
Practically speaking, it is a direct link between brands and consumers. Permission ditches the parasitic data harvesting model used by tech giants. Instead it gives you sovereignty over your own data and enables you to monetize it for your own benefit. It feeds you branded content, but rewards you in ASK and never intrudes without your consent.
Therefore, the messages of the Permission medium are:
- We respect you and your boundaries
- Your time and engagement are valued
- You are in control and choose who you interact with
- Spend a little time with us, but then move on to what you want to do
- By committing to transparency, our good intentions shine through
- We want to build trusting relationships with each other
- Over time, we can symbiotically help one another
In short, Permission is a desperately needed medium carrying a uniquely refreshing message – This is not the digital advertising that you know. This is digital advertising on your terms.
6 Easy Ways to Earn Free Bitcoin Right Now
Amid these uncertain times, people are increasingly looking for new ways to make money.
And, with the booming cryptocurrency market, you have more chances to earn Bitcoin than ever.
Fortunately, as the digital asset market’s infrastructure is rapidly developing, opportunities abound for you to earn bitcoin as a source of extra income.
However, it’s nearly impossible to make a considerable income from bitcoin without investing your funds or putting in the effort to achieve your goals.
While there are multiple ways to earn free Bitcoin, you have to be ready to spend the time to make a decent income.
In this article, we have collected the best ways to earn Bitcoin and other crypto for free, and methods that require you to invest some of your funds to make money.
How to Stay Safe While Earning Bitcoin
Before we take a look into the best ways to earn Bitcoin, it’s crucial to talk about staying safe while making an income with BTC.
As mentioned earlier, you have to dedicate either time or money to earn considerable amounts of cryptocurrency.
There is no way around this.
For the same reason, when you see people claiming that their “secret methods” allow you to earn over $1,000 in BTC every day without any effort, you can almost instantly tell that these posts are outright scams or they are not telling you the full truth.
Unfortunately, many scams and fraudulent schemes in the cryptocurrency industry exploit people who are looking to earn free Bitcoin.
Scammers often impersonate famous persons – such as Elon Musk – or prominent companies to advertise fraudulent “giveaways,” encouraging people to send BTC to their wallet, promising that they will send back double the amount.
Obviously, these addresses do not belong to Elon Musk or other famous persons, and you won’t get back any of your coins after sending them to the scammers’ wallets.
With that said, many people are falling victim to these scams.
To avoid getting scammed while earning free Bitcoin, it’s essential to do your due diligence before taking any risks. Below, we’ve included some tips to stay safe:
- Remember the golden rule: “If the opportunity seems too good to be true, it probably is.”
- Check external, independent sources for reviews, comments, and feedback from users.
- Do a background check on the company or person advertising the method for earning. Are you dealing with a registered company or a real person? Or is it a fake name made up by scammers?
- Sometimes, scammers are not (directly) after your money, but instead are looking for your data. You should never disclose sensitive personal information to anybody unless you are 100% sure that you can trust that person or company.
- To stay safe, you should always check the documents you sign and the terms you accept.
- Even if you find a genuine method to earn Bitcoin, you should analyze its risks and ensure that you never risk more money than what you can afford to lose.
The Top 6 Ways to Earn Free Bitcoin
Now, after ensuring you are protected against scammers and fraud, it’s time to take a look at the best ways to earn Bitcoin!
1. Bitcoin Faucets
Overview
Maybe the oldest way to earn free Bitcoin is to use a BTC faucet. A Bitcoin faucet is a website that regularly distributes small amounts of BTC, allowing visitors to earn cryptocurrency for free.
The concept of Bitcoin faucets originates from early cryptocurrency advocates who gave away a part of their digital asset holdings to facilitate the crypto industry’s adoption.
While there are still some faucets without requirements to earn free Bitcoin, most of these solutions now require certain conditions that you have to meet in order to claim your digital assets.
The requirements can vary from completing surveys and interacting with advertisements to downloading the creators’ applications.
Upon completing these tasks, you have to specify your BTC address, where the operators will send your free Bitcoin.
While some faucets limit earning opportunities to a single occasion, others allow you to generate free BTC on multiple occasions.
Risk
Unless a faucet requires users to provide sensitive personal information or download a malicious app, the risks for earning Bitcoin by this method are very low.
Effort Required
You don’t need to put in too much effort to earn Bitcoin with faucets. Even if you have to meet some conditions to claim free BTC, completing these requirements is quite easy.
Earning Potential
As they are extremely popular among crypto enthusiasts and operators only distribute small amounts of BTC, the earning potential of Bitcoin faucets remains very low even for those who are willing to spend significant time to claim their free coins.
Pros
- Free method to earn Bitcoin without investment.
- Good introduction for those who are new to cryptocurrencies.
- Minimal risks involved.
- Requires minimal effort to claim free BTC.
Cons
- Earning potential is very limited.
- Most BTC faucets require users to complete tasks to earn free Bitcoin.
Where to Get Started
- Cointiply: One of the most popular Bitcoin faucets where you complete tasks to earn BTC.
- Bitcoinker: Roll dice to earn Bitcoin every five minutes.
- BTC Clicks: Earn BTC by clicking on ads.
- Satoshi Quiz: Take quizzes to generate a crypto income.
2. Crypto Cashback
Overview
As we have discussed in our Stacking Sats guide, cryptocurrency cashback programs are an excellent way to earn Bitcoin.
Similar to rewards programs on the traditional market, multiple cryptocurrency projects have introduced solutions that allow users to earn cashback on their purchases in BTC.
Crypto cashback programs work in a simple way. First, you have to install the creator’s browser extension or app and register an account with the service. Then, you can start shopping at the creators’ partner stores where you can earn a percentage of your order back in cryptocurrency.
It’s important to mention that some crypto cards allow users to earn a cashback on all of their purchases. However, these projects often require users to stake, i.e., lock up a part of their coins for a certain period, the creators’ tokens.
Risk
Like with Bitcoin faucets, the risks are very low for earning crypto cashback rewards. However, we should emphasize that you have to spend money to earn BTC with this method.
Effort Required
You only have to dedicate time to installing the creators’ apps, selecting the stores where you spend your money, and earning Bitcoin cashback in return.
Earning Potential
As you gain only a small percentage of your purchase back as Bitcoin cashback, no matter how much you spend, the earning potential remains low for crypto rewards programs.
Pros
- A good way to earn crypto while spending at partner stores.
- Low risks involved.
- Minimal effort required.
Cons
- You need to spend money to earn BTC.
- Earning potential remains low even if you spend large sums at partner stores.
Where to Get Started
- Lolli: Install a browser extension and earn up to 30% Bitcoin cashback at partner stores.
- Fold: Use the creator’s app to get back up to 20% of your purchase as BTC cashback.
- MCO Visa Card: Stake CRO tokens to earn up to 5% crypto cashback on all your purchases.
3. Cryptocurrency Mining
Overview
Cryptocurrency mining is one of the oldest and most popular ways to earn Bitcoin.
To mine Bitcoin, you have to continuously operate specialized equipment, dedicating your computing power to maintain the blockchain network. In exchange for supporting the network, Bitcoin miners receive block rewards and a share of transaction fees.
While you only needed a simple desktop computer to become a miner during the early Bitcoin era, you have to source expensive, specialized hardware to maintain a profitable crypto mining business today.
Since cryptocurrency mining is a rather energy-intensive process, you have to also take electricity costs into account when calculating your profits.
Risk
As it requires an upfront investment and has ongoing costs to cover equipment, energy, and other expenses, crypto mining is certainly not a free way to earn Bitcoin.
Therefore, there are high risks involved, especially when bitcoin prices are falling (as you earn less in these periods).
Effort Required
In addition to higher risks, you need to dedicate time to learn the ropes of cryptocurrency mining, including setting up your equipment and operating your rig to earn BTC.
Alternatively, crypto enthusiasts can choose to purchase cloud mining contracts. In cloud mining, the service provider operates the mining equipment on behalf of the customer.
While cloud mining requires little effort, the earning potential is much lower than for standard cryptocurrency mining (as service providers often operate with high fees).
Also, as the industry is highly targeted by fraudsters, you need to be extra careful with cloud mining service providers.
Earning Potential
If you are willing to dedicate some time and take high risks, cryptocurrency mining can be a lucrative business.
Pros
- With the necessary skills, effort, and investment, cryptocurrency mining has good earning potential.
- You earn Bitcoin while supporting the network.
- Cloud mining requires limited effort from your side.
Cons
- You need to invest money into crypto mining before you can earn BTC.
- High risks, which are even higher for cloud mining contracts.
- You need to dedicate much of your time to learn the ropes and maintain the equipment.
Where to Get Started
- Bitcoin Mining Calculator: Calculate the expected income, expenses, and profit of your crypto mining business.
- Bitmain: The largest cryptocurrency mining equipment manufacturer.
- Genesis Mining: Popular Bitcoin cloud mining service.
4. DeFi Lending
Overview
Decentralized finance or DeFi has become one of the hottest topics in the cryptocurrency space. In short, DeFi refers to the movement where cryptocurrency projects create decentralized, blockchain-powered alternatives to traditional finance solutions in the form of DApps (decentralized applications).
Currently, you can choose from various DeFi products, ranging from borrowing and lending to insurance and decentralized exchange solutions. Nowadays, DeFi lending solutions are the most popular products on the market.
Instead of going through the tedious process of credit checks and submitting numerous documents to banks, DeFi lending solutions allow users to borrow funds against their cryptocurrency holdings in a near-instant way via smart contracts.
In exchange, lenders receive interest on their funds for contributing cryptocurrency (usually stablecoins like DAI) to the pool, often yielding higher returns than traditional finance solutions (e.g., savings accounts).
Risk
Most DeFi lending platforms operate in a completely decentralized way, meaning that the service provider has no custody over your funds.
Also, smart contracts are responsible for issuing loans to borrowers and providing interest to lenders.
While this eliminates the risk for human error, cryptocurrency loans are overcollateralized. This means that the borrower’s collateral value exceeds the value of the funds you lend to him.
Suppose the lender fails to pay back the interest or the value of his collateral decreases to a specific level. In that case, the smart contract will use the collateral to automatically repay you the sum the borrower owes you.
Unless you use non-stablecoin digital assets for lending (as you have to take volatility into account in that case), there are only small risks involved in the process.
Effort Required
Besides purchasing, exchanging, and transacting crypto to your wallet, you don’t need to put much effort into earning with DeFi lending.
Earning Potential
While interest rates vary, you can usually earn between 2-15% annually by lending your stablecoins to borrowers on DeFi platforms.
The more funds you lend, the better your revenue will be.
Pros
- You can usually earn better interest on your funds with DeFi solutions than with traditional savings accounts.
- Only limited risks involved when lending stablecoins (e.g., DAI, USDT).
- Smart contracts eliminate human error while overcollateralized loans solve the issue of non-paying borrowers.
- No custody of your funds.
Cons
- You need to make an investment to earn Bitcoin with DeFi products.
- Risks are higher for using standard, non-stablecoin cryptocurrencies (e.g., BTC, ETH, LTC) for lending.
Where to Get Started
- Maker DAO: Decentralized organization and ecosystem featuring leading DeFi lending solution.
- Compound: Earn interest on your stablecoins by lending them to the decentralized finance ecosystem.
- Aave: Open-source and non-custodial money market protocol where you can earn interest on various cryptocurrencies.
5. Staking Crypto
Overview
Cryptocurrency staking is also a good way to earn Bitcoin. And with the rise of the DeFi industry, there are more options to stake crypto than ever.
The concept of staking is very similar to cryptocurrency mining. In blockchain networks based on the Proof-of-Stake (PoS) consensus algorithm, validators confirm transactions and maintain the ecosystem by staking cryptocurrency.
In practice, staking means that you lock up some of your coins for a specific time, and the network will choose between you and other stakeholders to verify the next block. If selected, you will earn rewards for validating blocks.
To maximize their chances, users have created staking pools where stakeholders lock up their funds in the pool together, sharing the rewards among participants upon successful block validation.
Risk
While staking is similar to DeFi lending, the risks are a bit higher for the former.
Usually, projects require you to stake standard, non-stablecoin cryptocurrencies. This means that your staked coins could be subject to excessive price movements while locked up in your wallet.
And, as you need to lock them up for a specific period, you won’t be able to sell them (or interact with them in another way) to avoid losses.
Also, some service providers require users to utilize their own wallets for staking digital assets, which can involve higher risks if those wallets lack the necessary security features.
Effort Required
Most staking pools do not require much effort from the stakeholders’ side as you only have to transfer your coins into a wallet and lock them up for a specific time.
Earning Potential
Your staking rewards are based on the coin you choose to lock up and the pool you use for staking.
Pros
- You can earn a passive income on your cryptocurrency.
- No need to interact with your coins once they are locked up in your wallet.
- Based on the service provider and the coin you stake, the earning potential can be high.
Cons
- High risks involved mainly due to market volatility.
- Keeping coins at dedicated staking wallets involves higher risks.
Where to Get Started
- Trust Wallet: Crypto exchange Binance’s official wallet that allows you to stake different digital assets.
- Coinbase: Leading digital asset exchange that also features a staking service.
- Staked: Non-custodial staking service supporting a wide variety of cryptocurrencies.
- Everstake: Staking service platform where you can earn a 5-20% annual interest on your coins.
Beyond Bitcoin: ASK, a New Crypto You Can Earn While Engaging with Advertisers
Most people see traditional advertising as annoying rather than as an opportunity to earn rewards, and for a valid reason.
Ads running through the advertising networks of tech giants – such as Google and Facebook – continuously bomb consumers with offers while they are trying to enjoy their favorite online activities.
In this traditional model, consumers don’t get anything in return while advertising networks use consumers’ data to increase their profits.
To solve this issue, Permission.io has created a blockchain-based advertising platform where consumers are in charge of their data. In exchange for providing permission to receive targeted offers and engage with advertisers, consumers are rewarded in Permission.io’s ASK cryptocurrency.
To get started, simply create an account or add the Permission Browser Extension to Chrome to begin passively earning crypto as you surf the web.” In exchange for providing permission to receive targeted offers and engage with advertisers, consumers are rewarded in Permission.io’s ASK cryptocurrency.
Permission.io users can use the digital assets they earn to shop at the Permission.io Store and eventually other 3rd-party eCommerce sites.
While users can earn 100 ASK for registering an account at Permission.io, they are also rewarded in cryptocurrency for referring friends.
If you are interested in earning ASK by sharing your time and data, we recommend checking out the official Permission website.
It’s Time to Earn Free Crypto
From mining cryptocurrency and lending your coins to engaging with advertisers, it’s easier now to earn Bitcoin and other cryptocurrencies than ever.
However, as we have mentioned earlier, it’s crucial to stay safe as scammers and fraudulent projects are actively targeting the cryptocurrency space.
It’s also important to remember that you can only earn BTC by dedicating your funds, time, or both.
And usually, the more effort you put into a method, the higher your potential will be to earn.
Disclaimer: The content of this blog is for general informational purposes only and is not intended to provide specific advice or recommendations for any individual or on any investment product. It is only intended to provide education about the cryptocurrency industry. Nothing in this post constitutes investment advice or any recommendation that any cryptocurrency or investment strategy is suitable for any specific person. Further, there is no guarantee that any cryptocurrency discussed in this article will have any value at any given time. Do your own research thoroughly before making any investments of any kind.
8+ Ways to Make Money Playing Video Games
It’s probably not the career path your mother would have chosen for you, but maybe it’s time for her to reevaluate.
Video games have become a titan in the entertainment industry over the last few decades, with the market peaking at $35.4 billion in 2019 revenue. For context, that’s more than three times the revenue made by the music industry and 83% of the money made by the movie industry in the same year[*].
You’re probably familiar with some of the ways you can make cash playing video games, with major streamers like Ninja making serious cash and eSports being aired on ESPN, but did you know there are ways you can take your favorite hobby and play video games for cash — even outside of a professional context?
While pursuing a professional career is an option, you don’t have to be a major league gamer to pad your savings account while you’re waiting for your next doctor’s appointment or when standing in line at the DMV.
There are so many ways to make money playing video games, but most of them aren’t worth it. We’ve done our research and pulled out the options that are worth considering. We tell you the honest truth — what you choose to do with it is your decision.
Some of these have the chance to be lucrative, most do not. Some follow more traditional career paths, others involve an entrepreneurial spirit. Some pay you immediately, others require content and time investment.
Take a close read through to figure out which option is best for you.
1. User Test Video Games for Large Video Game Developers
It’s not surprising once you stop and think about it, but every game ever released needs to be tested. Think of it like writing a book, except that the sentences aren’t linear. Someone has to playtest every aspect of a game before its release, and companies like Blizzard, EA, and Ubisoft all employ full-time and contracted video game testers.
The money can be better than you think. Video game testers can easily earn $50,000+ a year, but keep in mind this is a demanding, full-time position. You aren’t just lazily playing video games. Here’s an idea of what you would be doing:
- Carefully performing “matrix” tests to “break” a game – e.g. exploiting balancing strengths and weaknesses in a MOAB game.
- Writing down articulate and meticulous thoughts around new versions and the issues you encountered. You can’t say, “The game was choppy”. You’d have to say something more along the lines of, “Version 1.32’s load time between cutscenes clocked in at 12 seconds, which is much longer than the 4-second benchmark we established”.
- Attend meetings and relate your findings to the developer team.
- Staying on top of bug fixes and reminding the team to resolve them.
Another common complaint is the lack of upward mobility. Where do you go from being a user tester? Well, the answer is nowhere concrete.
How to Get Started
Check out some job boards and see if any positions are available.
Here are some companies that offer user-testing positions:
- Nintendo: How cool would this be? The only catch is you have to live in Redmond, Washington since it’s where their American headquarters is.
- Blizzard: User-testing jobs at Blizzard are hard to find, but you may be able to snag one if you keep a close eye on it.
- Rockstar: Same idea here. These jobs don’t come up often at Rockstar but you may be able to pick one up if you’re lucky. And remember these are legitimate jobs and should be treated seriously.
2. User Test Video Games via Smaller Third-Party Testing Sites
There are also generalized video game sites where you can sign up to test all sorts of games. Some of these require you to take voice and video recordings as you play them, others don’t. It’s essentially a product testing platform and the jobs depend on the various video game designers’ needs.
How to Get Started
Start enrolling and checking out gigs on a few user-testing sites.
Here are few third-party user testing sites to get you started:
- Beta Testing: Beta Testing was previously known as Erli Bird, and it’s a general platform for businesses to hire users to test their apps, games, and software.
- UserTesting: Similar to Beta Testing, this site has a broad set of user testing opportunities but video game gigs do show up from time to time.
- PlaytestCloud: This is a mobile app testing site, so you can find mobile games to test here. On their site, they mention that pay varies, but they give an example of a $9 test for 15 minutes of playtime.
3. Use Mistplay or Other Mobile Apps
There are a couple of mobile gaming apps that make their cash through ads and user data while paying users for their time. You’ll have to play what they want you to, but if you aren’t too picky then these apps could be good for you. You won’t make more than a few bucks a month, but it’s not a bad way to spend downtime.
How to Get Started
Download a few mobile gaming apps and see which one you enjoy the most.
Here are a few mobile gaming app options:
- Mistplay: Play games and earn cash. This is best for mobile gamers who don’t mind opting in to play random games. You won’t get more than a couple of bucks a month, though.
- Bananatic: Online platform where you play for points that you can redeem for gift cards and other offers.
- AppNana: A mobile reward app that gives you rewards for completing small tasks and playing games. You can then redeem them for Xbox gift cards and other prizes.
4. Use Sites Like Swagbucks or InboxDollars
If you aren’t picky about the video games you play and are interested in a generalized approach to spending downtime, then Swagbucks and InboxDollars are two of the “make money online” juggernauts to consider.
Both services are pretty similar. Basically, you create an account, fill out some basic information about yourself, and then there are a wide variety of ways you can collect “bucks” or “cash”. These options include taking surveys, watching ads, playing games, and much more.
You won’t make anywhere near a liveable income from these sites, but they are good options to have around if you’re bored and looking for ways to gamify your discretionary spending.
How to Get Started
Fill out an account on either Swagbucks or InboxDollars and start playing some games!
Here are few links to “make money online” sites:
- Swagbucks: The biggest player in the “make money online” space. You can do everything from play games to watch movie trailers to fill out surveys and turn earned points into cash.
- InboxDollars: This service is very similar to Swagbucks, and many people mix and match between the two. Take a look at the video game options on both sites and see which ones are more fun.
5. Make a Youtube Channel or Twitch Stream
This is the most popular way to make money with video games at the moment. Just like your last Los Angeles Uber driver, you could consider starting your own Youtube Channel or Twitch Stream.
Isn’t that extremely difficult? Well, yes. Of course. Being successful as an online video gamer and streamer requires at least one of these three of these skills, if not all:
- A particularly good knack for video games.
- A charismatic personality.
- A unique spin and/or special attention to production value.
Just opening up a streaming account and starting isn’t enough to get people to stick around. You need a hook. That can either be your ability to play, the way you have fun while you play, the way you present the material, or any of the above.
How to Get Started
Take some time to think critically about how to approach your Youtube or Twitch channel by using the advice below:
Take a close look at existing streamers. What could you do differently? How can you make video games entertaining outside of just playing them? What about you can become your unique value proposition? Think carefully before investing your time here, most people don’t make it.
Here are some major streaming sites to think about starting on:
- Twitch: The ultimate video gaming streaming site. The competition here is difficult, but you won’t find a platform with a wider potential audience.
- YouTube Gaming: YouTube’s live streaming is good but not as robust as Twitch’s, but it also allows you to post compilation/other types of video game content and ultimately build a broader channel than Twitch.
- Dlive: A newer blockchain streaming service that focuses on audience building and community rewards. This one is bound to be less saturated than the others.
6. Enter Tournaments
One skill-based opportunity is playing in tournaments. Large games like Overwatch, Apex Legends and Fortnite regularly host tournaments.
If you are aiming (wordplay intended), for a skill-based entry into the video game market, then you need to prove to others (and yourself), that you have what it takes to win. Start training and start competing. If you don’t see meaningful progress and aren’t seeing results after a period of pursuit, consider moving on.
My advice on this is two-fold:
- Choose a game with longevity to invest in. Considering how long StarCraft II has been around, there is a decent chance StarCraft II will fizzle out over the next few years. That means it’s probably not the best time to start skilling up.
- Choose a game that has existing hype or the potential for growth. Ideally, you will catch a wave like Ninja did with Fortnite.
How to Get Started
Find an upcoming tournament with players you know are around your level, start practicing, and get to work.
Here are a few video game tournament sites:
- Battlefy: BattleFy hosts a bunch of Rocket League, League of Legends, and Hearthstone tournaments, but it also has a lot of depth with the types of tournaments you can enter in. The competition is tough but the prizes are high!
- Gfinity Esports: Gfinity tournaments are extremely competitive and run by a well-respected company within the gaming world.
- WorldGaming: WorldGaming is a huge network of tournaments that has a variety of smaller and big tournaments you can compete in. If you want to get your feet wet, this is a good choice.
7. Consider Becoming a Video Game Coach
If you have some sort of professional record in the video games space, have an entrepreneurial spirit, don’t mind selling yourself, and are a good teacher, then you could look into becoming a video game coach.
The niche is small but growing, and if you can position yourself around certain video games and also build in essential networking and life-skills training apart from the pure “wins” results, then you may have a business opportunity on your hands.
How to Get Started
Take a hard look at your credentials and see if this path makes sense and if you want to give it a shot. Then, start thinking like an entrepreneur using the advice below.
Your best bet from a marketing perspective is either wealthy college kids or upper-income parents with kids interested in pursuing this full-time. Your approach will need to change according to the demographic you’re pursuing, and always remember whose pocketbook will be paying you.
I’d also pick up some Business 101 books to make sure you understand exactly what you’re getting into.
Here are a few sites you can use to start finding clients:
- Gamer Sensei: You have to apply to be a Sensei and give a bit of your cut to this site, but they will provide you with students if you get accepted.
- Fiverr: Fiverr is a general freelancing site that you can bid for contracts on. Set up your profile and start bidding for jobs!
- Facebook Gaming Groups: After you’ve set up your online site and portfolio via LinkedIn etc., you could join gaming groups, get involved in those communities, and then start making connections with aspiring players.
8. Write Video Game Articles or Reviews
This is more of a long play to build an audience, but if you love writing and reviewing games, then you should consider publicizing and monetizing your work. You can do this via two main ways:
- By pitching to existing gaming publications.
- By building up your own channel/brand specifically built around video game reviews.
Each option comes with its own challenges. If you are pitching to publications, you need to send ideas, articles, etc. that are an exact fit for their brand. Remember, people are lazy — the key to networking is to reduce the friction required for anyone to do what you want them to do. If you can pitch an article at the right time that’s perfectly on brand, then you may open some doors and get paid for your article.
To get an idea of how to cold-email journalism sites and land gigs, check out Toby Howell’s incredible cold email sequence, which he used to land a job at one of the most prominent email newsletters out today, Morning Brew. It’s brilliant and well worth the read if you plan on pitching articles to anyone anytime soon.
If you’re looking to build your own channel or audience, whether it’s directly or adjacently related to video games, then there are a few ways to think about it. You either need to:
- Approach video game reviews in a style that feels “fresh” or new. This can involve a certain ploy or brand feature (e.g., always including a video game developer on your reviews) or by having your own video production style.
- Use an approach that’s popular but do it better. This is very difficult to do and requires a lot of expertise or time developing that expertise.
In reality, it’s very difficult to make a significant income writing video game reviews and articles, so your best bet is to look at it as a passionate side hustle.
How to Get Started
Start writing and reviewing video games publicly and either use them to pitch to existing publications or post them directly on your own platform.
Here are a few publications to pitch to and reviewers to emulate:
- IGN: IGN is a powerhouse player in video games journalism. Remember to make your pitch as specific and actionable as possible. Good luck!
- Polygon: Polygon is an entertainment review and news company that is always up to hear good pitches from freelancers. Use this link to review their submission guidelines.
- Mandalore Gaming: Mandalore Gaming is a great example of a one-person shop for video game reviews. Check out how well they review games and conduct audience building.
- Gameranx: Gameranx is an even bigger Youtube operation than Mandalore Gaming, and they specialize in compilation and “tips and tricks” videos. Take a look through their top videos to get some inspiration for your own channel.
Bonus: Expand Your Definition of “Getting Paid to Play Video Games”
What about avenues that don’t directly involve playing video games? As we mentioned, the video games industry is massive, so if you enjoy video games, I encourage you to look beyond strictly playing video games for money.
You could:
- Become a video game story writer
- Edit scripts for video game dialogue
- Conduct research for a team
- Market video games
- Become a video game developer
There are tons of options once you open this angle up. Yes, this doesn’t involve pwning noobs for $100k/year, but on the other hand, the world is your… kirby?
Plus, working alongside your passion instead of in it is often a good way to preserve your joy and love for it. It’s easy to get burned out on something you love once it’s your actual job — just ask any musician after a long touring leg!
The Bottom Line on Getting Paid to Play Video Games
If you’re looking to make a few extra bucks in your downtime, then there are definitely options for you to make money playing video games. Check out sites like Swagbucks and Mistplay and use them to pick up some extra cash in time you’d normally be wasting anyway.
Heck, you could even use the money you earn from those to buy major releases you’re really looking forward to playing.
And if you’re looking to make it big in video games, that’s fine to pursue — just make sure you’re strategic about it and recognize that most people aren’t able to make a living playing video games. Fortunately, there are all sorts of fun and interesting ways to build video games into your life
Permission is changing the internet as we know it by paying users for sharing their data while browsing the web instead of allowing advertising companies to use it for free. Check out their Browser Extension which lets you passively earn crypto as you use the internet.
See how we’re giving the power of data ownership back to the people.
Eyebrow Text Here
Don't miss anything
Join our newsletter for the latest news and product updates
