Resources
Insights on building trusted, permissioned, and compliant data systems for the AI era.

Recent Articles
Permission Becomes Founding Member of Data Privacy Protocol Alliance (DPPA)
Permission is proud to announce that it is a founding member of the Data Privacy Protocol Alliance (DPPA) alongside BIGtoken, CasperLabs, Own Your Data Foundation, SQream, First Rate, Tapmydata, and more.
The DPPA is a group of organizations that have banded together to build a new decentralized data ecosystem that puts consumers in control of their data and competes against the entrenched data monopolies.
Ownership of our personal data will be a fundamental cornerstone of a future where data is owned by the individual and data monetization is possible. Together, we are collaborating to define universal standards of data usage, privacy and implement a decentralized data privacy blockchain that can ensure adherence to the policies set.
“Our data is still held captive and by an oligopoly of tech giants that rule over the data economy,” expressed Charlie Silver, CEO of Permission.io. “Partnering together with other companies that believe in the same values is the best way to return Data Ownership to the individual and move into the Web3 era.”
The entire Permission team is thankful to the leaders at BIGtoken and CasperLabs for spearheading this effort, which has allowed our like-minded companies to rally around a single cause. We believe that when individuals are given tools that empower them to individually choose how their data is shared and monetized, data privacy becomes a non-issue and justice prevails.
For more information, please visit the Data Privacy Protocol Alliance (DPPA) website.
Third Party Data: What Is It and Should You Use It?
Mismatches between advertisements and the people receiving them have been the bane of existence for both advertisers and consumers since — well, advertising became commonplace. And even the best-matched advertisements can fall flat due to poor timing, bad execution, ad fatigue, and numerous other reasons.
Fixing interruptive, ineffective ads once and for all while protecting user data privacy is what we’re doing right now, but in the meantime, where does third party data fit into the ad ecosystem? Third party data is both an attempt to solve personalization issues and also a creator of them.
But, before we go too far into the world of third party data and how businesses should approach it, let’s take a second to define the other three major types of data businesses use:
- Zero party data is any user data that is given up voluntarily by a consumer to a business or entity in return for some sort of benefit.
- First party data is user data collected by companies directly from their own customers like email addresses, phone numbers, and purchase behavior data.
- Second party data is first party data sold or given to another business.
What Is Third Party Data?
Third party data is any data collected and used by companies who have no direct connection to the users whatsoever. Examples include past purchases and demographic identifiers which are packaged and sold to businesses through various data marketplaces.
Third party data is collected from a wide variety of sources, refined into sellable segments by publishers or data management companies, and then used by advertisers to combine with their own first party data to reach and learn about new audiences at scale.
Third party data is packaged by these data managers into customer personas or other simple identifiers. If you’ve been to sites that allow you to target “college students” or “real estate agents,” then these sets are likely some form of third party data.
Data Sets Built From Our Digital Footprints
While third party data can include offline data like offline purchase behavior and store visits, third party data became the mammoth it is today after the invention of the internet, and more specifically, the invention of website cookies and mobile advertising IDs.
Every user performing almost any action online is leaving footprints — sort of like little cookie trails. If you think of these cookies as lego pieces, then third party data aggregators collect as many of these blocks from as many viable sources as possible and build them into customer segments, profiles, and opportunities for advertisers to use.
These lego structures (collections of cookies and data) can be sold in private or public marketplaces, where publishers (the people providing ad space) and advertisers can place restrictions and quality control measures to ensure their data isn’t being stolen and is compliant with new privacy laws like GDPR, the CCPA, and the CPRA.
There are many ways businesses use third party data, but two of the most common ways are bolstering their own first party data profiles and exploring new audiences.
Who Uses Third Party Data?
Any business who wants to improve their existing advertising targeting or discover more about their target market for any reason you can imagine. This effort is usually spearheaded by marketing, sales, and data departments.
How Does Third Party Data Work in Practice?
So how does the third party data ecosystem function? At its core, there are few major players:
- Demand-side platforms (DSPs)
- Data management platforms (DMPs)
- Supply-side platforms (SSPs)
Demand-side platforms like Google Ads let advertisers purchase ad space, supply-side platforms allow publishers (like websites) to sell ad space to advertisers, and data management platforms organize, collect, and package the data that DSPs and SSPs use.
Third party data is threaded through all of these platforms, but they are all aimed at doing the same thing: facilitating efficient advertising from companies to potential consumers. This is made possible by integrations and partnerships between these platforms, the providers of that data, and the aggregators of that data. Some platforms prioritize publishers, others prioritize advertisers, etc.
In the first wave of digital advertising, DSPs were where most third party data lived, but SSPs have been picking up more of the share in recent years due to ad inventory being more transparent.
A Real-World Use of Third Party Data
Let’s look at an actual use case for third party data.
Let’s say you (the user) went to Zillow.com and checked out houses and then went to 4-5 different blogs about home ownership and home buying. Based on this information, you may be tagged and placed into a data set called “potential home buyers,” which then a company like Rocket Mortgage could buy.
Rocket Mortgage could take that data and combine it with their internal data sets. They may have had a tag on you showing that you had read one of their blogs, but perhaps they didn’t know that you were also between 35-44 and married.
They can take that info, create a more complete picture of you, and then use that as a creative starting point to make more specific advertisements to you and others like you via social ads, TV placements, or any other ad channels made available by the data set.
The accuracy of that data will depend on the purity of the ad sets Rocket Mortgage purchased, and that’s what makes the entire ecosystem even more complicated. There are layers of private and public platforms from which to purchase third party data that have varying degrees of quality control and audiences available.
The Power of Third Party Data: How Businesses Use It
There’s no end to the ways businesses can use third party data, but generally speaking, third party data allows them:
1. To Deliver Personalized Ads at Scale
The more accurate a segment is, the more personalized advertising can be. This is the key appeal for all data in the marketer’s mind — the chance to say something to the right person at the right time to spur action.
Third party data and its large and dense data sets, in effect, hand what is unique about individuals to marketers en masse. Advertisers then take these insights and use them to educate their campaigns.
2. To Mine for New Audiences
Third party data is also useful for mimicking existing audiences — i.e. create a lookalike. If you know that your top customers are 18-24 and play college baseball, what could you do with the chance to reach 100,000 more of them?
3. To Enrich Existing Customer Profiles and Segments
Third party data is most effective when used in tandem with first party data. The combination of data you can trust with larger sets is one of the best paths to personalization.
4. To Optimize Product Experiences
Third party data can be useful when examining user behavior at scale. If you discover that your target demographic prefers video content to text, then that can change your entire marketing approach to that segment.
Third party data also helps companies understand how their potential and existing customers behave, which they can then use to shape their core offerings and services. For example, data scientists could mine third party data to understand how best to build an app’s UI (user interface).
The Most Popular Third Party Data Sources and Providers
Third party data is used all over the advertising world on different platforms. Some are DSPs, some are SSPs, and your choice in platform will depend on the data they have available, what advertising opportunities are made available, and the type of business you are.
Here are a few major examples of third party marketplaces or platforms that use third party data:
- Nielsen
- Lotame
- Social platforms like Facebook, Google, Pinterest, and TikTok
- Public government survey data
- Acxiom
- Mobilewalla
- Adobe
The Downsides of Third Party Data
While third party data can sound exciting to advertisers and publishers, there are many issues to be aware of. Here’s what to keep in mind when approaching third party data:
You could be using data that isn’t compliant with GDPR, CCPA, or CPRA.
Data privacy laws like GDPR hold businesses responsible for their entire data apparatus — not just what they have direct control over. In other words, businesses can be held responsible for data violations that occur via any partnerships or integrations.
If you plan on using third party data, you need to ensure that the data you purchase was gathered with express consent for the purpose it is being used and that the company you are working with isn’t violating any existing laws.
Cookies are on the way out, and this will hamstring a lot of third party data collection efforts.
Google, Safari, and Firefox have all vowed or already started to leave cookies in the past[*]. While this won’t destroy third party data — there are still a wide variety of ways you can collect and sell it, it will (at least temporarily) affect data availability and integrity.
Companies like Google do have other solutions in the works that are less invasive than cookies but still allow for effective targeting[*].
Juggling a lot of data sources can be difficult.
Third party data, especially at scale, requires consistent technical labor to utilize efficiently. While the marketplace is making it easier and easier for businesses to take advantage of third party data, there is almost always technical work involved when combining data sets.
Accuracy is often overestimated and ill-defined.
Not all third party data is gathered equally, which is another reason why taking the time to vet your provider is important.
For example, if you were a wedding website company, and you bought a packaged audience of people who are newly engaged or in long-term relationships, poor data management could mean that people in that audience are stale and have already gotten married, making your advertising irrelevant and a waste of money.
Your competitors could be using the same data.
Since third party data is packaged and sold, there is no guarantee that your competitors aren’t using the same data to target customers.
That doesn’t mean you can’t do a better job with messaging and product-market fit, but it is something to keep in mind.
Third Party Data: An Advertising Practice in Decline
While third party data is still a widely used and important resource for businesses, especially at the enterprise level, it is clear that many forces at work will diminish its effectiveness — and for good reason.
User data should be owned by the users themselves, not the companies they interact with online.
If we accept this, then the existing ecosystem that promotes company welfare over user privacy is fundamentally broken, and products that exist due to the exploitation of user data (like many third party data marketplaces and products), need to be sacrificed and adjusted to create a better, safer, and more democratized internet.
In other words, we need to discard the old internet advertising model and give users back ownership of their data while setting up opt-in advertising mechanisms that compensate users for their data. If this sounds impossible, it isn’t.
By using the capabilities blockchain makes available to us, we can reward users for interactions they have with advertisers of their choice. This approach will revolutionize the data-dependent advertising marketplace by prioritizing zero party data, which gives businesses better targeting/ROI and enables consumers to receive compensation for their data and engagement and receive ads that are more relevant
Think that sort of advertising model isn’t possible? Think again.
See how Permission is building that world right now.
What Is IDFA and Why Did Marketing Just Get More Difficult?
If you work with Facebook advertising or mobile apps in any capacity, chances are you’ve been sent a litany of updates about the infamous iOS 14.5 update. The marketing and advertising world is panicking, and it’s hard to argue that they’re overreacting.
The changes iOS 14.5 will make to the ad ecosystem and IDFA tracking is significant. They will hamstring conversion tracking, especially while everyone adjusts, and set the stage for even more restrictions on digital advertising moving forward.
We’re going to give you a brief overview of what IDFA is and how it’s been used in the past, and then we’ll dive into the topic of the day: how iOS 14.5 is changing the value of IDFAs and what you can do to keep your marketing ROI as high as possible.
What Is IDFA?
IDFA stands for IDentifiers For Advertisers, and they’re the equivalent of browser cookies for mobile phones.
Every single Apple phone ever made has a unique code attached to that device. No two are the same, and Apple, app developers, and the advertising world use these unique identifiers to track behavior within apps and pass that information on to different sources. Google also has their own version of this, known as GPS ADIDs.
To put it in context, if you serve up a Facebook app install ad to a new audience and 50 of them click through and download the app, Facebook uses the relevant IDFAs to match that click-through on their platform to the install event in the app.
This type of tracking has been digital advertising’s bedrock. IDFAs are used in everything: user tracking, measuring ROI, attribution, ad targeting, monetization, device graphs and insights, effective retargeting, programmatic advertising on DSPs and SSPs — you name it.
So when a company like Apple starts poking at that foundation, it makes sense why people are nervous.
Let’s talk about what Apple is up to.
The Current Buzz Over iOS 14.5 and IDFA
Last summer, Apple dropped a bombshell: their upcoming operating system update, iOS 14, would make the user default to allow companies to use a device’s IDFA to opt-in instead of opt-out.
This means any time a user downloads a new app, the developer must ask for consent before collecting any IDFA information. This is what that looks like:
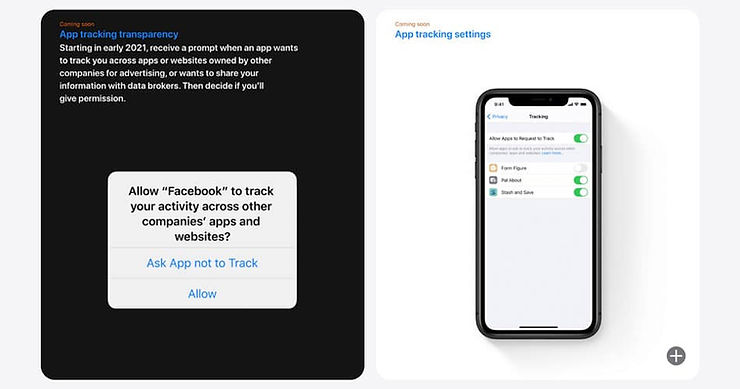
If everyone clicked “Allow”, then advertising would continue like normal, but that’s not what people do. 31.5% of iOS users before this update were already limiting ad tracking[*], and while we don’t have numbers yet, there is no doubt that the percent of people who opt out will significantly increase.
So for every person who opts out, that’s another user who is more difficult to track, meaning advertisers will be working with less accurate data than before.
(Want to opt-out of IDFA tracking? On your iPhone or iPad go to Settings > Privacy > Advertising and then turn “Limit Ad Tracking” on).
Why Would Apple Make These Changes?
If things like Apple advertising and the mobile app ecosystem are important to Apple’s bottom line, why would Apple do this?
There are two main reasons:
- The public cares more about data privacy than ever before, so being proactive about digital privacy is a marketing differentiator.
- Laws like the European Union’s GDPR and California’s CPRA are redefining consent around data in the digital era, and Apple is adapting accordingly.
To be clear: this is a good thing. Users have more control over who is using their data, when, and why, which is something that has been abused for decades by internet companies.
So while the growing pains will be difficult, this will pave the way for new advertising technologies and formats that incentivize users to proactively volunteer their data in return for value (e.g. opt-in value exchange ads).
The iOS 14.5 Timeline — What To Expect and When
Even though the data opt-in changes were announced in June 2020, Apple decided to delay that change to give advertisers a chance to get ahead.
As of this writing, iOS 14.5, the version that will incorporate these IDFA changes, is currently available in beta to developers, and the mass consumer rollout is expected sometime this month or next month.
This means that all of the fears and predictions of what this will do to the market will be tested shortly.
How iOS 14.5 and IDFA Will Affect Your Marketing Strategy
The main impact of iOS 14.5 is that conversion tracking will be less accurate, and the granularity of your attribution will suffer.
Without getting too technical, the solution provided by Apple to mitigate the damage of these IDFA changes is to port over to what’s known as the SKAdNetwork, which is an API solution for app activity tracking that is completely user anonymous.
Here’s the difference between that, which will be advertising’s new normal, and what IDFA used to give us.
Here’s what you can still expect to have in a post-iOS 14.5 world[*]:
- Click-through attribution for ads displayed in mobile apps.
- Publisher ID of the publishing app.
- Campaign ID which can be used to code information IDs such as campaign, creative, and placement.
- First time install vs. redownload information.
- Conversion values that allow basic post-install tracking. This helps with analyzing user quality.
- Apple’s cryptographic, unforgeable verification of the attribution and parameters – meaning anyone can verify that an install really happened while still respecting user privacy.
- Still generally accurate and fraud-free attribution.
And here’s what we’ve lost:
- No more view-through attribution. Everything will have to be triggered by a click.
- No more click-through attribution for ads displayed in browser, email campaigns, or any other medium apart from native ads.
- Real-time data. Everything will be set to a 24-48 hour delay to protect privacy.
- No user-level data.
- No more small campaign and publisher data. You must exceed a threshold before Apple reports some conversion information.
- No deep linking and populated long-term cohort statistics like customer lifetime value (LTV).
With that in mind, here are some thoughts and strategies you can use to keep your advertising effective in 2021 and beyond.
How Can Marketers Mitigate the Impact of iOS 14.5?
It’s not all doom and gloom for advertisers. Yes, things will be a bit different from now on, but that doesn’t mean effective digital advertising is gone for good. Start here to stay on top of the changes:
1. Update your SDK to support the SKAdNetwork.
If you haven’t already, get your developers to update your SDK to support Apple’s new SKAdNetwork solution and then verify your attribution across each channel.
For example, take the week after your SDK was updated and verify that the number of installs reported from your Facebook Ads match up to the number of installs you’re seeing being reported in the App Store developer console or your preferred analytics provider.
This gets more complicated the more channels you’re on, but the point is to systematically verify all of your advertising channels’ reporting.
2. Customize the “opt-in” prompt text on your app.
Instead of using cold language like, “Allow Facebook to track your activity across other companies’ apps and websites?”, you could say something like, “Help keep our app free by allowing better ads to be delivered to you with data tracking” or something similar.
3. Ask for IDFA consent after the install.
As long as you ask before you start tracking IDFAs, you don’t have to do it before the install.
Asking before the install could reduce conversion rates, so getting your developers to delay the prompt is a worthwhile A/B test. This also gives you more time in the app to explain how that data will be used.
4. Prioritize first party data.
The more user privacy is championed, the more old-fashioned advertising data’s value will increase — at least until a new type of internet is created.
Email addresses, phone numbers, and other forms of first party data that you can rely on to reach customers directly will become more important as interruptive advertising gets more difficult.
To mitigate the damage of iOS 14.5, try shifting your budgets to use more permission marketing to gather FPD instead of leaning more heavily on interruptive strategies.
5. Tie big-picture data back to individual ad channels.
Take the time to develop the most accurate estimates of “revenue per install”, “customer lifetime value”, and other big-picture metrics, and then use that as a rough estimation of your channels’ effectiveness.
For example, if you know you get around $2 in revenue per install on Apple Search, then you can use that as your floor cost per install when advertising.
6. Accept that things won’t be as accurate, and that’s okay.
You’re not alone in the scramble. Take everything one step and one channel at a time, and reevaluate each step of the way.
As time goes on, technology will get better, so just ride this wave for now!
The Future of IDFA and the Modern Digital Advertising Ecosystem
It’s clear that as sweeping user privacy laws continue to emerge, data privacy products gain market share, and breaches become more common, the protection of user privacy in the zeitgeist is here to stay, and that’s fantastic news.
Yes, it will make advertising more difficult, but that is only temporary. Today’s advertising ecosystem is broken, anyway. Click fraud is rampant, users are served ill-matched ads, and ad blockers are more popular than ever. Plus, attribution has never been flawless.
All of this begs the questions: what if there was an alternative way to approach advertising altogether? Is the system we have the best solution?
A whole new internet.
It turns out, no. There is a much better way to structure the entire digital advertising ecosystem, and we’re building it.
By compensating users directly for opting in to share their data and engage with advertisers, we can incentivize users to share their data in a transparent way, which ultimately builds brand trust and loyalty.
Moreover, advertisers improve conversion rates because the users they reach will be opting in and demonstrating genuine interest in the ads they deliver.
The next generation of the web will usher in this new form of “win-win” advertising. Instead of a zero-sum game, an evolved advertising model will emerge, whereby users can derive financial value from the enormous asset that is their personal data, and advertisers can build long-term relationships.
See how we’re revolutionizing the advertising ecosystem.
California Privacy Rights Act (CPRA) Explained
Most of us don’t think about it often, but data is constantly working behind the scenes. Every video we watch, website we view, and article we read is collecting numerous points of data on our behavior and reporting it to its owners.
Any free service you use is packaging up, sharing, or selling your data to a variety of sources, and most of the time we haven’t the slightest idea what data is being sold and to whom it’s being sold to.
Plus, any personal information like credit card numbers, addresses, and phone numbers we enter online is being stored somewhere in the cloud — at risk of being compromised in the next inevitable breach.
After a mostly unburdened twenty years of corporate internet domination, consumers and their elected officials are starting to push back against the existing internet’s ecosystem and its abuse of privacy. The EU’s GDPR represented the first major piece of modern consumer privacy law, and countries and states around the world have started to look to it as a model for their own rights.
In the United States, California has been leading the charge, previously passing the California Consumer Privacy Act (CCPA) and now the California Privacy Rights Act (CPRA), also known as CCPA 2.0, in November of 2020.
The CCPA was a landmark piece of data privacy legislation that went into effect in 2020, and the CPRA is seen as an extension and bolstering of that law. It was widely disputed but seen as a victory by privacy advocates such as Consumer Watchdog and Andrew Yang.
So what is the CPRA and why is it important?
Let’s figure that out.
What Is the California Privacy Rights Act (CPRA)?
The CPRA refers to the California Privacy Rights Act, a data privacy law passed with 56.2% of the vote in November 2020. You can view the entire text here.
Known as “CCPA 2.0,” the CPRA strengthens, extends, and alters the CCPA. The CCPA was criticized for a litany of reasons, including having vague expectations, inadequate enforcement, and not providing enough rights, and the CPRA was designed to speak to each of those issues and more.
Specifically, the CPRA introduces new consumer privacy rights, alters some key definitions in the CCPA, puts tougher fines in place for minorities, establishes an official enforcement agency, and much more.
When Does the CPRA Go Into Effect?
Now that the CPRA has officially passed, everything is in motion. Here are the key dates you need to know:
- January 1, 2021 – The CPRA went live, which in effect stopped any conflicting privacy legislation.
- January 1, 2022 – The 12-month “lookback” for any collected data begins. In other words, this is the beginning of when businesses can be held accountable for violating the CPRA.
- January 1, 2023 – CPRA goes live and all exemptions expire — opening up everyone to full regulation.
- July 1, 2023 – CPRA becomes fully enforceable by the CPPA (the organization created to enforce the CPRA).
Note: Even though the official enforcement date isn’t until July 1st, 2023, your data practices are open to scrutiny starting January 1st, 2022.
A Brief Summary of the CPRA’s 6 Biggest Changes
Here’s a rundown of the most important additions and changes the CPRA introduced to the CCPA:
1. Established the California Privacy Protection Agency (CPPA)
One of the biggest criticisms of the CCPA was how enforcement worked, and leaving the responsibility to the attorney general’s office was clearly not going to work. To fix this, the CPRA created an agency with the explicit purpose of regulating and enforcing the CCPA and CPRA. They will be handling the enforcement, fines, and communication with non-compliant businesses.
2. Created New and Modified Existing Consumer Rights
The CPRA added two new rights to the CCPA — the right to rectification (or correction) and the right to restriction. This means that consumers have the right to have false information fixed and that consumers have the right to restrict how business can use their sensitive data. It also expanded rights around data portability, data exclusivity, and many others.
3. Distinguished Personal Data Into Separate Classes — Standard and Sensitive
The CPRA stipulates that all data are not equal. Social security numbers are different from email addresses in terms of value, for example. With this distinction in mind, the CPRA created different rules and potential fines for each. These rules include stricter disclosure requirements and limitations on how the data can be used.
4. Made Violations Involving the Data of Kids and Minors a Lot More Severe
Parents didn’t feel like the CCPA addressed the privacy concerns of children enough, and the CPRA stepped up to address this by allowing the CPPA to 3x any fine that involves a minor’s data. The law also dictates how consent is managed and allows parents to have more control over their children’s personal information.
5. Forced Companies to Protect Employees — Regardless of Where They Live
In addition to protecting consumers living in California, the CPRA also expanded its protections to any employees and contractors who are working for California companies. This means that any of the rights in the CCPA and the CPRA are enforceable across state lines when they involve employees and contractors.
6. Changed What Kinds of Businesses Are Subject to Scrutiny
The CPRA expanded the law’s scope in some categories and relaxed it in others. For example, small and mid-sized businesses are now exempt when buying, selling, receiving, or sharing data up to 100K consumers or households (assuming they don’t qualify for other categories), but the CPRA made businesses who make at least 50% of their revenue from sharing data eligible — regardless of how much revenue they make.
Let’s look at that a bit more.
Who Does the CPRA Apply To?
The CPRA now applies to:
- Any business that has more than $25+ million in annual revenue.
- Any business that shares, sells, or buys the personal information of 100k+ consumers or households.
- Any business that gets at least 50% of its annual revenue from selling or sharing consumer personal information.
These categories apply to any company that does business within California. If you have users or sell products to California but are headquartered in Miami, you still have to comply.
Why Is the CPRA Important?
The impact of the CCPA and the CPRA will be felt for decades. California is the first major state to pass a set of data laws this comprehensive, and the successes and mistakes they make along the way will be watched carefully by other states across the country. The CPRA could also represent the second step in paving the way for federal consumer data regulation in the future.
The CPRA also forces other amendments to be consistent with the CPRA. In other words, if a county or city decides to pass a law that violates the CPRA, consumers, employees, and contractors could sue based on the CPRA’s protection. This further solidifies the CPRA in the world of law.
And more broadly, the CPRA is another major victory in the world of user privacy. Laws are rarely perfect, but it does represent the second step in a shift toward a more consumer-centric internet ecosystem.
Criticisms of the CPRA
There are common criticisms from larger businesses and corporations that you would expect — namely that the law will be too cumbersome on small businesses, cripple crucial data pipelines, and harm the overall consumer experience, but the more compelling criticisms come from privacy advocates.
The ACLU, for example, came out with a surprising attack against the CPRA labeling it as a missed opportunity [*]. Other critics point out that because the CPRA is fundamentally “opt-out” instead of “opt-in,” it opens the gate for companies to charge more for services that use less data — effectively creating an inequality where lower-income users will be forced to give up their data more often.
The CPRA has also been criticized for not allowing users to sue rule-breaking companies outside of special cases like breaches — only the CPPA has the authority to enforce fines. That being said, the CPRA did give the CPPA the authority to update the CPRA according to how the law handles itself in practice, so we can expect some adjustments that may speak to these issues later on.
What Are the Fines and Consequences of Violating the CPRA?
The CPRA is enforced via its new agency, the CPPA. It is the sole purpose of the agency to enforce the CPRA/CCPA and respond to complaints/hold non-compliant businesses accountable, and the CPRA can also be enforced via data breach lawsuits on behalf of consumers.
The fines for non-compliant businesses can vary widely in amount and are based on two main categories: fines that come into play when a consumer sues a company for a breach and when the CPPA fines a company directly.
For the first category, the fines are defined by these three criteria:
(A) To recover damages in an amount not less than one hundred dollars ($100) and not greater than seven hundred and fifty ($750) per consumer per incident or actual damages, whichever is greater.
(B) Injunctive or declaratory relief.
(C) Any other relief the court deems proper.
In other words, the fines will usually be stackable amounts of $100-$750. This can add up quickly when thousands of customers or incidents are involved.
For other fines, the agency has a lot of freedom:
(2) In assessing the amount of statutory damages, the court shall consider any one or more of the relevant circumstances presented by any of the parties to the case, including, but not limited to, the nature and seriousness of the misconduct, the number of violations, the persistence of the misconduct, the length of time over which the misconduct occurred, the willfulness of the defendant’s misconduct, and the defendant’s assets, liabilities, and net worth.
In other words, whatever the agency feels is appropriate based on the unique case. This is purposely broad.
How Do You Comply With CPRA?
Complying with the CPRA means continuing and expanding the efforts you are making to comply with the CCPA. This includes having clear ways for users to opt-out of data collection, making it easy for users to transfer or change their data, and being proactive about your approach to user privacy.
Similar to the world of PCI Compliance in payment processing, complying with CPRA isn’t a one-and-done deal. Regulators are looking for consistent effort — an internal focus on protecting user rights. This is something that must be a process within your business, and the more thorough you are with that process, the less likely you are to be fined, or in the case of a fine, the less severe it may be. Demonstrating authentic effort is important.
You can structure that effort across three broad categories, similar to how companies in the EU are approaching GDPR. Those categories are:
1. Data Minimization
Data minimization means collecting the bare minimum amount of data needed to fulfill your business’s needs. It’s an active effort against “data bloat,” which unnecessarily makes data breaches more harmful. “Only collect what you need” is the mantra here.
2. Purpose Limitation
Once you collect someone’s personal information, you can only use it to the extent to which the user agreed. If you have been using a particular data set collected with consent for a period of time and want to use it in a different capacity (such as sharing or selling), you must be able to show that users consented to that secondary use as well.
3. Response to Requests and Active Engagement With Privacy Concerns
At its heart, the CPRA is trying to protect user privacy by making data management easier and more transparent for consumers. Businesses should be building systems and processes to make opting in and out of data collection and use more simple.
Phrases like “Do not use my personal information” should be clearly represented on homepages, there should be customer service resources allocated to data management, and resources telling consumers exactly how and why you use what data should exist.
If you work toward these three categories, then you’ll be well on your way.
For a more detailed rundown on how to begin preparing for CPRA’s January 1st, 2022 lookback period, go here.
The Bottom Line on CPRA
If you operate in California in any capacity and fall into one of the three categories mentioned above or plan on growing into one of those categories eventually, you need to be proactive about CPRA.
CPRA and its sister law the CCPA represent a fundamental shift in California’s approach to consumer data and will force businesses to take a hard look at how they collect, protect, and use consumer data.
The best plan is to have a plan, and business owners must demonstrate an active, early, and well-prepared approach to consumer privacy as defined by the CPRA and CCPA.
The World of Permissioned Data
The term zero-party data bubbled up over a year ago. It has the following meaning:
Zero-party data is personal data that a customer deliberately and proactively shares with a brand or a retailer.
Long before the term zero-party data was invented, we referred to such data as permissioned data at Permission. There’s also the term “declared data,” which may confuse the picture — that’s data acquired by such activity as consumer surveys. It is also permissioned data or zero-party data. But let’s not be confounded by the terminology; beneath it all lies an important development in the world of advertising and marketing.
Businesses are beginning to recognize that many individuals are aware that they own their personal data and they are eager to put it to good use. There are many reasons why this has come to pass: because of government regulation, because of outrage at the exploitation of personal data by some vendors, but most of all, it has become clear that personal data has significant value.
Just so we are clear about how this idea emerged, let us quickly describe first party data, second party data, and third party data.
- First Party Data. This is the data that a business gathers directly from its interactions with its audience, usually via its website, or possibly by emails, records of conversations, and any other direct interaction with either its customers or prospects. The important point to note is that until quite recently, first-party data was the highest quality data a business could collect concerning its customers and prospects. Unless it is regularly renewed, it gradually ages.
- Second Party Data. This is no more nor less than second-hand first-party data. It’s the data an organization collects from its audience that it sells directly to another company. Second-party data is likely to be of lower quality than first-party data because, by the time you get your hands on it, it has aged and because you will inevitably be less aware of its context than the company providing it.
- Third Party Data. This is data you can purchase from data brokers and data aggregators. The source companies did not originally collect the data (as first-party data) but aggregated it from multiple sources. Some of the data may be obtained from public sources, government records, social network profiles, and so on. Some of it may come from purchased first-party data. Some may even come from hacker data. Naturally, the quality of the data will vary according to the methods and diligence of the aggregator. In general, item for item, it is likely to be relatively low-quality data.
The Emergence of Permissioned Data
It was against the landscape of these three types of differently-sourced data that the term, zero-party data, first emerged. It was invented by the analyst company Forrester. In the wake of GDPR legislation in the EU, Forrester realized that there was another category of data that did not fit into the first, second, and third-party data categories. And it was important because it was high-quality data.
Because we at Permission had been pursuing a business model based on the productive use of personal data more than a year before GDPR came into force, we had our own ideas about personal data and our own term for it. We called it permissioned data. In our view, permissioned data is personal data that individuals are willing to share with other parties.
There can be a variety of reasons for wishing to share personal data. One obvious example is medical data. People will obviously want to share their personal health data with healthcare organizations. They may want to share their employment data and educational data with potential employers. They may want to share financial records with financial service companies.
And, of course, they may want to be able to share that data in contexts where they can be rewarded for its use. That’s what Permission.io is about and that’s also what Forrester was talking about with Zero-party data.
The Quality of Permissioned Data
Permissioned data is data that individuals own and manage and make available directly. It is high quality for several reasons:
1. It is likely to be up-to-date.
If permissioned data is well managed it will be more up-to-date than first, second, and third party data. Such data was always captured some time ago, possibly quite a while ago. Permissioned data is current data.
The reality of data is that it changes. Addresses change, qualifications change, jobs change, financial status changes, marital status changes, and preferences change. When you think about it, most data is akin to a photograph. Assuming it has not been corrupted, it gives you information that was true at a particular point in time and may no longer be true.
2. It is the prime source.
Regulations are making it increasingly costly to store personal data. You only need to study the EU’s GDPR to realize how onerous storing personal data can be. The data owner has:
- The right of consent
- The right to access the data
- The right to change data
- The right to complain
- The right to erasure
- The right to portability
The point is that if you’re going to store personal data, then you will need systems and software procedures that enable you to accommodate the rights of the data owner.
You will also need a Data Protection Officer. The reason is simple, the EU insists that you appoint one. And by the way, if you violate an EU citizen’s data rights, the fines are steep — up to 4% of your annual revenue (this is not a misprint).
Doesn’t it make a lot more sense to simply rent the personal data you’d like to use, by arrangement with its owner?
Now you may be thinking, “well I don’t deal with EU citizens.” And that may be the case, but if that’s what you think, make sure of it. Because if you hold the data of even one EU citizen, then these rules apply. And if you don’t, but one suddenly gets into your system, then these rules apply. And these rules apply to all organizations in the world, irrespective of jurisdiction.
And, also, you probably need to watch out for your local data regulations too, no matter where your company is based, because the global trend is for governments to increase the regulation of data. The smart move may be to evade those laws by letting the data owner put in all the effort.
3. It is accurate and comprehensive.
Permissioned data is likely to be more accurate. This is partly because it is the prime source and, hence, when you get hold of it, either it has never been copied (because you are using source data directly) or it has been copied just once, temporarily into your analytics system.
Permissioned data is likely to be more coherent in the sense that the data is organized and there is nothing ambiguous about its meaning. Because, at the moment, very few people directly manage their own data, the quality of permissioned personal data will improve over time. Indeed, once data owners get into the habit of curating their own data, they will have a growing incentive to make it as comprehensive as possible. In making this point we are, to a certain extent anticipating the way things will be, but we have little doubt where this trend is heading.
Bear in mind that there are different categories of data:
- Curated data: Information, including credential data, that the data owner naturally assembles from their activities.
- Declared data: Information knowingly provided by a user through surveys or online forms. Some of this will simply be user opinion and it is well known that user behavior does not necessarily align with stated user opinion. Nevertheless, what a user thinks is useful information and matters. Increasingly users will always retain such data.
- Aggregated data: Data aggregates in which user data may participate. For example a collection of the personal data of all the people who support a particular sports team.
- Inferred data: Data logically inferred from a user’s personal data. For example, certain user preferences can be known by employing correlation algorithms to user data.
- Behavior data: Data gleaned from tracking user activity in any context, particularly online, to determine preferences.
Permissioned data will be better in all these contexts. Not only is it likely to be more accurate, but it will also be more coherent — less likely to contain puzzling contradictions.
4. It will improve with time.
The final important point is that permissioned data will get better over time. On the one hand, once data owners get into the habit of permissioning their data, they will also cease to let their data be copied, legally or otherwise. And once they realize that it is possible to monetize their data most people will try to maximize its value, which will mean accumulating as much of it as they can.
The sources of first, second, and third party data will, at some point, begin to wither on the vine.
Data Evolution
Recent activity, by Apple in providing its iPhone and iPad users the ability to opt-out of sharing IDFAs (IDs for advertising) and by most of the browser software companies in sidelining third-party cookies to the point where they will become obsolete, has put marketers in an awkward position. You don’t need a weatherman to know which way the winds blow here. Third-party data is going to become harder to accumulate.
As this corner of the market runs into problems, at the other end of the spectrum the evolution of permissioned data has only just begun. The point is this: permissioned data is in its infancy.
Yes, of course, it will prove extremely useful to brands and retailers and it will soon drive a new and exciting advertising platform. Advertisers will enjoy higher quality data than they’ve ever previously known and the ROI on their advertising will improve, perhaps dramatically.
And by the way, did I mention that once you have direct interactions between consumers and advertisers, all of those bots which plague other advertising markets will be locked out? If we do this right, the hackers and the scammers will melt away like snow on the water.
We should see this for what it is, an evolution of the market for personal data. Once individuals control their data, innovators will naturally enter into the market with new ideas about how the data owners can profit most.
This is not the same data that has been collected in a fragmented way by those who deal in first, second, and third party data, this is a data resource assembled from an alliance of the data owners. It is higher quality, it is far more coherent, and it will prove to be far more useful, not just to advertisers and brands, but to all organizations that interact with individuals.
Robinhood: A Lesson In Transparency For Brands
We have all been enthralled by the stories coming out about GameStop, WallStreetBets, and Robinhood. This wild adventure offers a powerful lesson for all brands: Be transparent about the customer data you collect and how you use it.
Robinhood, a one time darling of the fintech world, is a company whose motives some are now questioning. And at the heart of it is a parable about data, transparency, and trust.
Brands can learn a lot from the Robinhood story, but first, let’s get our facts about the company straight.
Robinhood made big waves when it first came out because of its enticing offer of free trading. Competing brokers were charging $5 to $10 per trade. This quickly allowed Robinhood to capture millions of new customers nationwide and grow rapidly over the course of just a few years. They made laudable and bold claims such as, “we believe the financial system should be built to work for everyone.” Those claims would quickly be tested.
When people first heard of Robinhood’s no-fee model, they were sceptical, and rightly so. Everyone asked, “What’s the catch?”
That question came to a head in December of 2020 when the SEC fined Robinhood $65 million for “misleading customers about revenue sources and failing to satisfy duty of best execution.” They declared that Robinhood made misleading statements and omissions in customer communications about its largest revenue source when describing how it made money. And despite their previous claims, their customers’ orders were executed at prices that were inferior to other brokers. The Better Business Bureau gave the company a failing grade in matters of transparency and trustworthiness.
Robinhood achieved its no-fee trade model by utilising a practice known as PFOF (Payment For Order Flow). This means the company was selling its customers’ trade data to market makers and high-frequency traders, who then used that data to fill orders at unusually high prices. And this was Robinhood’s largest source of revenue, a fact that the company did not disclose on their FAQ page. Customers never got a clear view of what the best price for a trade was, whether their order was executed at that best price, or how much profit was captured by Robinhood and their market maker in the process.
Robinhood essentially sold overpriced stocks to their customers while selling the data of their customers to Wall Street for their own profit — and they failed to disclose that information to the public. The company placed itself in a conflict of interest as they attempted to simultaneously serve their customers and the Wall Street firms that pay them.
The SEC ruling was a setback for Robinhood, but it was one the company could have shaken off.But then came the Gamestop short squeeze.
Robinhood suddenly found itself in the middle of a war between retail investors and Wall Street. And just when the drama hit a fever pitch, they halted the trading of GameStop stock. Robinhood likely had legitimate operational reasons for this decision, and the facts seem to support that. But, it hardly matters.
Robinhood’s practice of selling customer trade data without informing the customer had already eroded some trust in the company – many assumed that they were siding with their Wall Street partners when they restricted trading of GME.
If Robinhood had originally been more transparent about how they used customer data, the public would have slowed their rush to judgment as the company halted the GameStop frenzy. When the company most needed the benefit of the doubt, many remained sceptical of their motives.
There is a lesson in all of this: Using and profiting from your customer’s data without their informed permission may still be a standard business practice, but it won’t be for long. The public is not going to accept it anymore.
If your company isn’t completely transparent about what customer data you use, take a moment to consider how that could backfire on you. If your brand isn’t specifically asking for permission to use all of the customer data that you currently use, it’s time to reconsider that approach.
Trust is paramount when it comes to relationships between brands and consumers, and transparency is key to that. Respect their data, respect their choices and always be upfront and honest with them.
You never know when your company’s ‘GameStop moment’ might come. If you haven’t fully earned your customers’ trust, they will be reluctant to give you the benefit of the doubt.
Don’t let your brand take a hit.Be transparent.Ask permission.Build trust.And if you need help with that, just ask us. It’s what we do best.
SMS Marketing: Uses, Examples, & Best Practices
Thinking about adding SMS marketing to your mix? You’re in the right place.
SMS or text message marketing is a powerful tool that can be a great addition to your funnel, but you need to be careful with how you use it. Bombarding people with messages on their personal devices is a sure way to sour your customer relationships.
We’re going to give you an overview of what SMS marketing is, talk about some of the best ways to start using SMS marketing and give you a few recommendations on how to get started.
By the end of this blog, you’ll have everything you need to know to add SMS marketing to your marketing mix.
Onward and upward.
What Is SMS Marketing?
SMS or text message marketing is when companies and brands use phone numbers supplied by customers to reach out with product, sales, and content messages.
Anytime a customer offers a phone number and “opts-in” to receive text messages, they and the brand are participating in SMS marketing. SMS marketing is a popular way to deliver appointment-based messages, run contest giveaways, and offer automatic transactional messages.
Is SMS Marketing Effective?
Like most marketing tools, oftentimes it’s not the medium or channel that is or isn’t effective, it’s how good you are at matching your product and message to your customer’s needs or desires. SMS marketing can be incredibly effective, but it can also turn off your customers — the same way a good TV ad can make or break your business.
What SMS marketing is known for is its open rate — almost everyone reads every text that comes to their phone, with some reports estimating that 98% of all texts get read.
That’s what makes this such a powerful tool, but that power can swing both ways. People have less patience for ads in such a personal space, so you have to be timely and relevant or risk being blocked or unsubscribed from.
When to Use SMS Marketing
The way a restaurant chain uses SMS marketing will be different compared to how a SaaS company or entertainment company uses SMS marketing. Its capabilities and uses are broad, but here are a few common ways people use SMS marketing to get the ball rolling:
- Contests or giveaways. SMS marketing is a great way to drop links and pull customers into exciting contests.
- Flash sales. It’s awesome for limited or rotating inventory businesses, both offline and online.
- Booking confirmations. Any appointment or consultation-based businesses can benefit from auto-confirmations and reminders.
- Customer order/delivery updates. Most of us are familiar with Amazon’s SMS marketing letting us know when our order has arrived or if it’s delayed. How can you emulate this information-based tactic in your own business?
- Internal messaging at large companies. SMS marketing isn’t only about external communication. When a company is large enough, sometimes email isn’t fast or thorough enough. If the office is closed or a big announcement needs to be made, texting everyone can be the best route to ensure they see it.
- Content updates. This works best for companies who make their money through content, but you could announce a new video, podcast, or blog through text if the audience is devoted enough and is looking forward to hearing from you, e.g. a podcast that releases every two weeks and lets listeners know that a new episode is up.
- For meet-and-greets. A clever SMS marketing tactic is to use texting for meet-ups or VIP events. This allows you to capture the phone number for future marketing and offers a simple experience for customers. For example, if you were playing a show or hosting a conference, you could have a “text this number” to a free meet and greet giveaway after the show. You could also use this functionality to message details to VIP purchasers and follow up with them with photos or extra content after the event.
Benefits of SMS Marketing
The benefits you can get from SMS marketing will depend entirely on your industry and how you choose to build it into your funnel, but here are some of the ways businesses benefit from implementing SMS marketing.
1. Can Decrease Appointment No-Shows
Appointment confirmations and reminders via text will increase the number of people who show up on time to your appointments.
2. Can Increase Local Foot Traffic to Businesses
SMS marketing works really well with localized and timely discounts. An easy example of this is a holiday announcement. Say you were a local donut shop and had a limited release donut for Father’s Day. Let’s say it’s a yellow and pink Simpsons donut called the Homer. You could send a text out to everyone who lives nearby with something that says:
Happy Father’s Day from What’s Up Dough! We are celebrating with a ONE DAY limited Homer Simpson Donut — key-lime pink icing with sweet cream. YUM. Drop by now! We usually sell out by 12! Much love.
A marketing move like that is bound to increase foot traffic in your business, and data backs up that assumption: Dynmark quoted that 29 percent of SMS marketing recipients click on links in SMS messages they receive, and 47 percent of those go on to make a purchase. That’s a conversion rate worth paying attention to.
3. Gives Incentives to Loyal Customers
Similarly, you could segment your customers by loyalty, customer longevity, etc., and reward those customers. You can make this fun by saying something like:
Don’t let anyone say you aren’t consistent — did you know that you are part of an elite group of coffee lovers who have ordered the exact same drink: cold brew with oat milk for the last 2 years? Wow. To reward that dedication, we’re giving you a free one — on the house! Just drop by and show this text!
This is a great example of how to make these texts more personal and interesting.
4. Gives an Outlet to Send Critical Information
You need to be careful not to overuse texting, but if your hours have changed significantly or if you’ve had another substantial update like a new product, service, or location, then SMS text messages are a perfect channel to deliver that information.
5. Provides Direct Service to Customers
If you set up your phone line to be two-way, you can also use texting as a direct support line and enable your customer service professionals to be even more hands-on.
How to Start Using SMS or Text Message Marketing
There is no shortage of SMS marketing software, and SMS marketing generally falls into two camps: text message marketing campaigns and transactional auto-responders.
Most official SMS marketing services give you the option to do both, but some shopping SaaS companies allow you to send auto-text confirmations, etc. but don’t allow you to be more granular. Look at your existing stack and see if a service you’re already using allows you to do SMS marketing.
If not, then consider the following options.
1. Twilio
Twilio has been at the top of the pack for multi-channel messaging for years, and their integrations, developer community, and customization features are the real deal.
Key Features
- Interest-based texting and communication
- Works hand-in-hand with other messaging platforms like Facebook Messenger
- Serves as an all-in-one solution for customer communication
Ideal for
Enterprise or established businesses with complex interest messaging and channel needs.
Pricing
They bill entirely off of messaging — whether that’s phone calls, texts, video chats, etc. The rates change for each, and they also offer bulk pricing.
2. EZ Texting
EZ Texting has been a power player in SMS marketing since 2004. Their partnerships, integrations, and resources make it worth looking over.
Key Features
- Keyword-based texting lists
- Drip campaigns
- Recurring messages
- Sign-up forms
- Reminders
- Picture capabilities
- 1-on-1 chat functionality
- Link shorteners
- Personalization
Ideal for
Companies that already have a CRM, customer database, etc., and are solely looking to add text messaging marketing to their business.
Pricing
Starts at $19/month but scales up according to reach and frequency of messages. Rates average out to around $0.04 per message after you exceed your plan’s message ceiling.
3. ActiveCampaign
ActiveCampaign is one of my favorite CRMs and is always releasing new features around email marketing, SMS marketing, and contact database management.
Key Features
- Text-based automation
- Appointment Reminders
- Builds seamlessly into the CRM and email marketing platforms
- Can easily combine SMS automation with email automation and trigger based on behavior
- Fantastic service and onboarding
Ideal for
Companies that haven’t settled on a CRM and want to centralize all of their marketing software. Or, for companies who want to have a lot of freedom over how they build their automation across multiple channels.
Pricing
SMS Marketing starts at a base of $49/month and scales up with the number of contacts and messages you send out.
4. Sendinblue
Sendinblue is another complete marketing SaaS service with email marketing at its heart. If you’re looking for an email marketing service and want text capabilities included, then they could be for you. If you’re already happy with your email marketing system, then I’d go elsewhere.
Key Features
- Interacts directly with their CRM
- Time and behavior-based text messaging
- Personalization
- Reporting and Analytics
- Transactional Emails
Ideal for
Similar to ActiveCampaign, Sendinblue is an all-in-one marketing software aimed at consolidating your contact management and marketing automation. It’s not nearly as complex as something like Twilio and is a better fit for smaller businesses. Take a look at each platform’s integrations to see what the best fit is for you.
Pricing
Their automation features start at around $65/month and scale up according to email and text volume.
—
Most of these companies have a litany of integrations that your existing marketing stack can plug into, so make sure that whatever company you choose will play nicely with your stack, otherwise, you will have a harder time using it to its full potential.
It’s also worth noting that most of these companies offer free trials, so it’s a good idea to hop in and see which one you like working in.
Best Practices for SMS Marketing
While SMS marketing is fairly broad, there are definitely ways to do it poorly and even illegally. Here are few best practices to make sure you start off on the right foot.
1. Never send a text to someone who hasn’t explicitly opted in.
Collecting and texting people without their permission is against the law. For the safest and best practice, always have the texting system be opt-in and confirm their subscription in the first text. More on this in the next point.
2. Be aware of text opt-in laws.
According to the Telephone Consumer Protection Act, you have to follow anti-spam policies when conducting SMS marketing. This includes guidelines that say you should:
- Always make it permission-based
- Always provide information on how to opt-out in each exchange
- Always mention your company name
- Disclose any carrier costs
- Never message about sex, hate, alcohol, firearms, or tobacco
3. Only use it in highly specific situations.
Again, texting people is a tool that should not be considered lightly. There is no quicker way to annoy someone than by overloading them with texts. Be smart, timely, and always think about your customer’s perception and experience when using text message marketing.
4. Use personalization and be human.
This is especially important for small businesses. Call your customers by their names, write as if they were coming from someone they know, and try to be as relevant as possible. Relevancy can be related to time (e.g., not sending a coupon about caffeine after 5 PM), being aware of where they are in their customer lifecycle with you, what they purchased last, holidays, etc.
In short, always try to tie each text to as much data as possible.
5. Remember time zones and don’t send during weird hours.
A classic SMS marketing mistake is to send out a slew of texts at 8 AM EST… which would be 5 AM PST. Always make sure you are sending at the appropriate time across time zones.
6. Use geography and event-based thinking.
SMS is really great when you use location and timing to your advantage. For example, if you’re a hot dog stand company with dozens of stands around a football stadium, you could time a text to all of the tipsy fans on your list leaving the stadium and give them a $1 off coupon for a dog.
7. Plug it into your existing funnel.
Look at SMS marketing as another piece of your marketing machine. I like to sketch out my entire funnels from the top down using software like Funnelytics to get the big picture. You want to make sure that each channel you’re using is working with each other, otherwise, you risk annoying your customers with too many messages or with repeat messages and causing damage to your customer experience and reputation.
8. Make each text actionable.
People don’t like to be interrupted for no reason. Make sure there is a clear and obvious benefit to be found within the text you send, and tie that directly to your call-to-action.
The Bottom Line on SMS Text Message Marketing
With the right strategy and preparation, SMS marketing can be a great tool for your business. My advice is to analyze your existing marketing funnel and identify some specific places where you could add SMS marketing in. Once you’ve identified those places, sign up for a service that is most friendly toward your existing and/or ideal tech stack and begin building out your initial campaigns.
Remember. Strategy first — always.
Good luck.
Permission.io is revolutionizing the internet as we know it — we’re handing data ownership back to the people and rewarding individuals for their permission to engage… we want you to be a part of it.
Second Party Data: Definition, Benefits, & Use Cases
In the world of modern marketing, second party data can feel obscure. You may have heard how great it is for audience expansion or new marketing campaigns, but it often feels like there’s a barrier to entry that’s much higher than collecting pixel data on your website (i.e. first-party data) or using databases that allow you to drill down by approximate demographic and psychographic (oftentimes third-party) data.
We’re going to demystify second party data for you and talk through actionable ways you can use and find it for your own company. It’s not for everyone, but if you’re working for a company that is actively scaling or is realizing its existing audiences are going stale, then second party data may be the ticket to your next success.
Before we go into the details on second party data and how to best use it, let’s briefly talk through the three other data types businesses use:
- Zero party data is any consumer-owned data that is given up voluntarily by a consumer to a company in return for some benefit.
- First party data is proprietary data collected by companies directly from their customers.
- Third party data are large data collections gathered by companies who are not the original collectors of that data.
What Is Second Party Data?
Second party data is data collected directly from users by one company and then sold or given to another business. It is often sold in private deals, exchanges, and used by social media and advertising platforms to improve targeting.
Put another way, second party data is first-party data that has been packaged and sold to another business.
Common examples of second party data include purchase behavior data, age and other demographic identifiers gathered from surveys, website cookie information, emails, device data, and user behavior data like login frequency and engagement.
Second party data is most often collected and sold in what are known as second party data marketplaces — if you hear words like data stream, data marketplaces, and private data exchange, those are businesses likely dealing with second party data.
Examples of Second Party Data Exchanges
A few of the more well-established exchanges include:
Second party data has exploded in popularity after GDPR‘s introduction and subsequent hamstringing of third-party data, and without more government intervention there’s no sign of it slowing down.
Modern second party data is reaching a point of sophistication where marketing leaders can effectively clone their existing profitable audiences at scale, and that’s a powerful driver for growth and continued innovation — plus selling data is still the primary revenue channel for most free apps.
Who Uses Second Party Data?
Anyone who has an interest in expanding their customer data information or in selling user information uses second party data. This could be anyone from data engineers, to marketing executives and consultants, to data scientists, to product management teams scoping out a potential market for a new idea.
Is Facebook Considered 2nd Party Data?
Facebook’s pixel, analytics, and demographic tools encompass all four types of data, from zero all the way to third. For example, if you’re using a pixel on your site, then that would be considered first-party data because your unique business is collecting information about your unique customers.
If you created an agreement outside of Facebook to share audiences with another business, and then they shared a custom audience with you that they directly collected, then that would be considered second party data.
The Power of Second Party Data: How Businesses Use It
One of the hardest parts of using second party data is narrowing down your choices — the extent of its capabilities is astounding. Businesses use it for everything from improving their own audience datasets to foster omnichannel marketing to mining interesting datasets for new products.
We’ll cover the broad umbrellas under which many businesses use second party data, but know that this is the shallow end of a very deep pool.
1. To Refine Existing Customer Profiles
The more channels and ways you can reach your customers and prospects, the more fragmented that marketing ecosystem tends to become. Just imagine the number of channels a modern eCommerce business that sells nationally could use:
- Facebook, Instagram, TikTok, Pinterest, LinkedIn, and others
- Google Ads
- Email Lists
- Shopify
- Specific Trade Publications
- OTT Marketing
- Traditional Print Ads
- Traditional TV Advertising
- Retargeting Sites like Adroll
Now imagine trying to coordinate a marketing effort between those channels. It gets complicated quickly — especially if you can’t tell if the audience you’re emailing is the same audience that’s getting your display ads on Google, or if the print ads are also reaching the geo-targeted email lists you have. Multiply that by country, state, and city, and you can see how the variables just spiral out of control.
Think of second party data as the flashlight that can illuminate and mend those blind spots — allowing your business to close the data gap and make sure you’re reaching the right platforms at the right time without wasting money by targeting the same customer twice or not efficiently moving them from one segmentation bucket into another.
Second party data marketplaces allow you to upload your own first-party data and combine it with other data sources to “round out” your customer profiles. For example, it could point out that 15,000 of your customers actually use Android devices and aren’t getting your Apple App install ads. Or maybe you realize that 5,000 of your users use a particular fitness app that you aren’t advertising on.
In short, if there’s data you wish you had on your customers, second party data may be the route to get it.
2. To Mine for New Audiences
Another use of second party data is finding new audiences to market to. Let’s say you ran marketing for a national music brand that sold pianos, and you wanted to find more people who would like your product. Wouldn’t it be useful to create an audience of everyone who has ever downloaded an app related to pianos and then use that to create a new remarketing audience? You could create that opportunity by purchasing that data directly from the app owner.
3. To Boost Analytics and Insights
Second party data can be useful for understanding how your existing and potential customers behave. For example, by being able to see what other customer lists similar to yours are paying for a type of product on an annual basis, you can better refine your customer lifetime value and get an idea of how much of the market share you and your competitors are taking.
4. To Generate and Test New Product Ideas
Let’s say you owned a clothing store and were thinking about building an app designed to connect personal stylists with your users for custom outfits. It would be useful to understand what types of people are using similar apps. By purchasing that app data, you could create your buyer personas and build your marketing plan from hard data instead of just guessing.
5. To Improve Segmentation Targeting
Tying in other data sources to your existing stream can dramatically increase your ability to segment your audience. Instead of only typical demographic and channel breakdowns, you could add in additional identifiers like shopping habits (e.g., night shoppers), app users, purchase behaviors, and more.
When employed correctly, this specificity will boost conversion rates, reduce ad waste, and help you scale in a profitable fashion.
6. To Sell Your FPD to Other Companies
Again, any first-party data that is sold or given becomes second party data, and some companies make all of their money this way. Social media companies do this most famously, but anytime you’ve heard of email lists being sold or purchase behavior information being given to complementary businesses, that’s an example of second party data.
Some second party data platforms let you upload your data to their stream, organize your bid prices, and manage your customer relationships all within a convenient dashboard.
7. To Create Lookalike Audiences
A simple way to take advantage of second party data is to work with a data provider to share Lookalike Audiences to your Facebook Advertising Profile. There are rules, but if you’re building a new product or looking for new audiences to reach out to — buying second party data from a relevant source and using it to build Lookalike Audiences can be a great way to start your campaign.
This is just the surface of what second party data can do. It is an incredible resource with the right infrastructure behind you, but getting access to this data at scale can be cumbersome and expensive.
Next, we’ll talk about the most common ways businesses access and sell second party data.
How Businesses Access and Sell Second Party Data
How can you access second party data? Well, that answer is a bit convoluted. Outside of private deals, second party data is notoriously expensive and often requires significant internal tech investments to foster communication at scale. That being said, there are a variety of players entering the market aiming to solve just that by approaching it like an eCommerce business.
Here are the main ways you can collect second party data:
1. Private Deals With Other Companies
The simplest way is to work directly with the company you want to buy from. Contact their CTO or marketing head and see if you can get a call on the books. You’ll know exactly who you’re dealing with, be able to hash out details of the agreement, and are likely to get more hands-on support with this route.
2. 2nd-Party Data eCommerce Platforms
There’s a wave of platforms that are aiming at creating “data streams” that facilitate communication, buying, and selling of second party data. By creating simple ways to sell and buy, having pre-written use contracts, and data integrations, this is likely the future of second party data.
Examples include: Narrative I/O and Lotame.
3. Google, Facebook, or SaaS Companies
A lot of second party data drives key functionality in SaaS, social media, and tech businesses. For example, Google Affinity audiences are an example of second party data. This is data on its users, collected by Google, and then shared with advertisers.
The same goes for Facebook saved audiences. Targeting users by interest, group membership, etc. is data collected by Facebook and made available to you.
Second Party Data: No Longer the Best for Marketers or Consumers
Second party data is incredibly useful. There is no denying that, and it’s still a fantastic tool for segmentation and creating better interest matching between advertisers and consumers.
That being said, second party data is far from ideal. It’s often expensive and difficult for advertisers to collect and implement, and the users themselves don’t have control or transparency into who gets to use that data and why. Their data is constantly being handed back and forth between companies, and this data is often fragmented and difficult to integrate anyway — making the experience worse for advertisers and consumers alike.
So what’s the alternative? Give users back ownership of their data and set up opt-in advertising mechanisms. By using blockchain technology to reward users for interactions they have with advertisers – of their choice – we can revolutionize the advertising marketplace by prioritizing zero-party data.
This is the beating heart of zero-party data — by creating the tools and ecosystem in which opt-in ad advertising can happen at scale, businesses get better ways to target their consumers, and consumers get ads that are more relevant to their interests. This value-exchange will decrease costs, increase satisfaction, and boost conversion rates while giving users back the data that is currently being harvested and abused by internet barons.
Think that sort of infrastructure isn’t possible? Think again.
See how Permission is building that world right now.
What Is CCPA? Overview, Laws, Requirements, & Future
As we leave our data on every site we visit, personal information has become a valuable asset for both consumers and companies.
For that reason, organizations process increasing amounts of personal information every day.
While there is nothing wrong with that, many companies sell the data of consumers to make a profit without their consent.
At the same time, with a hacker attack taking place every 39 seconds, a great share of organizations have failed to protect their customers’ sensitive personal information from data breaches that cost $3.86 million on average.
For that reason, data protection and privacy have become an important issue, with 46% of consumers feeling they have lost control over their personal information.
Besides consumers, governments have also realized the importance of data privacy. As a result, they have passed laws to provide increased control to their citizens and regulate how businesses can interact with their personal information.
The California Consumer Privacy Act (CCPA) is among such data privacy laws, which we will explore more in detail in this article.
What Is the California Consumer Privacy Act (CCPA)?
The CCPA refers to the California Consumer Privacy Act, a data privacy law passed by the California state legislature in June 2018.
Also called the “California GDPR” and “GDPR Lite,” the CCPA follows the footsteps of the European Union’s General Data Protection Regulation (GDPR).
The CCPA introduces new rules related to how businesses can collect and process data, consequences for non-compliance and breaches, as well as rights that allow California residents to have increased control over their personal information.
When Did the CCPA Go Into Effect?
While the state of California passed the law on June 28, 2018, the CCPA only went into effect on January 1, 2020.
Affected businesses were given six full months to comply with the law as part of a grace period. Commencing July 1, 2020, California authorities have the right to enforce the law and fine companies for non-compliance.
Who Does the CCPA Apply to?
The California Consumer Privacy Act applies to two different parties.
On one side is the consumer, defined as a California resident under the CCPA. Every natural person who resides in the state – even if physically outside California for a temporary or transitory purpose – is considered a California resident.
Since the CCPA provides increased control over their personal information, consumers are clearly the ones who benefit from the state’s data privacy law.
Indeed, under California’s data protection law, businesses don’t have much choice other than to comply with the CCPA’s rules.
However, the CCPA does not apply to all organizations.
To qualify as a business under the CCPA, the organization has to be a for-profit company that “does business” in California.
While this definition is rather vague, it means that an organization doesn’t have to be located in the state (or even in the United States) to be affected by the CCPA.
Instead, any for-profit business that serves California residents have to comply with the state’s data protection laws if it meets one of the following:
- Has an over $25 million gross annual revenue,
- Purchases, receives, or sells the personal data of 50,000 or more California residents, households, or devices, or
- Earns 50% or more of its annual revenue from selling the personal information of California residents.
It’s important to mention since IP addresses are considered personal information under the CCPA, any for-profit organization operating a website that has at least 50,000 unique visits from California in a given year has to comply with the state’s privacy rules.
The CCPA also applies to data brokers that are defined in the privacy law as organizations collecting and selling consumer personal information to third parties without having a direct relationship with end-users.
However, the CCPA exempts organizations regulated by certain other laws from complying with the California Consumer Privacy Act’s rules.
Examples of these organizations include credit bureaus as well as certain financial institutions and insurance firms.
Why Is the CCPA Important?
The CCPA is an important step towards consumer data privacy.
Until the law came into force, organizations could interact with citizens’ personal information without any major rules or accountability.
Nowadays, personal information is precious and extremely valuable. While businesses benefit from the worth of personal data, consumers largely tend to share significant amounts of their data without realizing it.
Without a data protection law, businesses can’t be held accountable for how they store and interact with the consumers’ personal information. On top of that, they can collect and sell personal data to make a profit without the users’ knowledge or consent.
In the worst-case scenario, the lack of proper security measures could lead to consumer data being obtained by malicious parties, potentially causing serious damages to the victims.
Similar to the EU’s GDPR, the California Consumer Privacy Act focuses on fixing the above issues by introducing stricter rules for businesses with the goal to safeguard consumer data and the privacy of the users.
Businesses impacted by CCPA may need to allocate an increased amount of resources to comply with the new rules in order to handle consumer data with care and avoid being fined by authorities.
With that said, the CCPA also provides some benefits to organizations. Upon compliance with the privacy rules, businesses can highlight how they protect their customers’ data to earn the loyalty and trust of consumers.
It’s also crucial to emphasize that the CCPA is a state-wide privacy law designed to safeguard the personal information of California residents. Currently, the United States lacks a federal law that offers data protection on the national level.
Interestingly, it is increasingly becoming the standard for US businesses to use CCPA-compliant privacy measures not just for California citizens but also for all their users throughout the nation (and even overseas).
How Does the CCPA Define Personal Information and What Data Does It Cover?
The California Consumer Privacy Act defines personal information as data that identifies, relates to, or could be reasonably linked to an individual or his household. Examples of such include:
- Name
- Age
- Email address
- Postal address
- Demographics data
- Social Security Number
- Driver’s license number
- Records of purchased products
- Geolocation data
- Internet browsing history
- IP address
- Biometric data (e.g., fingerprints)
- Financial information (e.g., credit card data)
- Account name or another online identifier
- Inferences from other personal information that can be used to create a profile about someone’s characteristics and preferences
The CCPA does not cover publicly available data from federal, state, or local government records. Professional licenses and public real estate records are good examples of data not covered under the CCPA.
Are Cookies Considered Personal Information Under the CCPA?
For business owners, it’s essential to take a look at whether and how the CCPA impacts the cookies they collect about California consumers.
Cookies refer to small text files that a website places on a user’s browser upon visiting the site. By doing so, businesses can collect information about the consumer, the user’s device, as well as other data that helps them recognize the user when he or she returns to the website.
We differentiate two types of cookies.
Cookies fall into the first category if they are necessary for a website’s core functions, recording only random identifiers, which are often deleted after the user closes his browser.
However, most cookies are placed on websites by third parties, using unique IDs to collect a wide range of data on consumers for marketing and analytical purposes.
Cookies falling into this category often store user data for longer times (even tens of years), which is a practice that can violate the consumers’ privacy.
Categorizing them as unique identifiers, cookies fall under the CCPA’s rules.
As per the notice at collection rule (more on this later), the business has to clearly display its cookie policy to users upon their visit, including what kind of personal information it collects about them and for what purpose.
Are There Any Privacy Policy Requirements in the CCPA?
The California Consumer Privacy Act requires businesses to disclose their privacy policies at a visible place on their websites.
Besides that, the companies’ websites have to include information about the privacy rights of consumers outlined in the CCPA (e.g., the right to know) as well as how users can exercise them.
What Are the Rights and the Requirements Under the CCPA?
As mentioned earlier, the CCPA provides new rights to consumers over their data as well as rules on how businesses can interact with it.
The Right to Know
The right to know refers to the ability of California consumers to submit requests to businesses to disclose what personal data they have collected, used, shared, or sold about them, along with the reasons for doing so.
Consumers can request businesses to provide the following information:
- The categories of personal information collected
- Specific records of personal data collected
- The categories of the sources the business used to collect the data
- The purposes for using the personal information
- The categories of third parties the business shares the data with
- The categories of personal information the business discloses or sells to third parties
However, businesses can deny the consumers’ right to know requests in some cases, including:
- The company can’t verify the consumer’s request
- The request is manifestly unfounded or excessive
- The business has already responded to the right to know request of the same consumer more than twice in a 12-month period
- Businesses are prohibited from disclosing sensitive personal information (e.g., financial account number, social security number, account password) even with the consumer.
However, in such a case, the company still has to inform the user about the type of sensitive personal data it collects
- Revealing the data would restrict the organization’s ability to exercise or defend legal claims or rights or comply with legal obligations
- The personal data falls into a category that is exempt from the CCPA (e.g., certain medical information and consumer credit reporting data)
To exercise their right to know, consumers have to submit a request via one of the methods (e.g., email message, phone call) provided by the company.
After submission, the business has 45 calendar days to respond, which can be extended to a total of 90 days upon notifying the consumer.
Organizations have to provide the sought data free of charge for the 12-month period preceding the consumer’s request.
It’s crucial to mention that consumers must submit their requests directly to the company in order to get their claims accepted.
According to the CCPA, businesses often use the solutions of multiple service providers (e.g., payment gateways, shipping companies, etc.). The privacy act treats service providers differently than the businesses they serve, making the latter parties responsible for responding to CCPA-related consumer requests. For that reason, submitting a right to know request to a service provider instead of a business will likely result in a denied claim.
Notice at Collection
A notice at collection refers to the mandatory duty of a business to inform consumers about the personal data they collect about their users at or before the point at which it gathers the information.
As per the CCPA, the notice at collection should include the categories of personal information gathered about consumers and the purposes for which businesses use them.
There is a further requirement for companies that do not just collect and use the consumers’ personal information but also sell it.
According to the CCPA, such businesses must include a “Do Not Sell” link in the notice, which users can use to opt-out of the sale of their personal data.
The Right to Opt-Out
With the right to opt-out, consumers can use the “Do Not Sell” link on a business’ website to request the company not to sell their personal data to third parties.
After submitting the opt-out request, the business is prohibited from selling the consumer’s personal data unless he later authorizes the company to do so again.
However, businesses must wait at least 12 months before asking a consumer who decided to opt-out for authorization to sell his personal data again.
It’s crucial to note that the CCPA includes some cases in which consumers are unable to exercise their opt-out rights.
A business might refuse user opt-out requests when:
- The sale of the consumer’s data is necessary for the company to comply with legal obligations, defend legal claims, or exercise legal claims or rights
- The personal information falls into a category that is exempt from the CCPA (e.g., certain medical data, consumer credit reporting information)
The Right to Delete
Under the CCPA, consumers not only have the right to opt-out of the selling of their personal data but also to request that businesses delete the personal information collected about them.
Similar to the right to know, businesses have a maximum of 45 calendar days – which can optionally be extended by another 45 days after notifying the user – to respond to the request.
Also, consumers must submit their requests directly to the business instead of one of its service providers, which is the same process as in the right to know.
In addition to fulfilling the consumer’s request, the company has to notify its service providers to delete any records they possess related to the user.
The CCPA includes multiple exceptions for the right to delete, including cases when the business:
- Can’t verify the consumer’s request
- Needs the personal information to complete the consumer’s transaction, provide a reasonably anticipated product or service, or for certain product recall and warranty purposes
- The data is crucial to carry out certain business security practices
- The user’s personal information is essential for certain internal uses, which are compatible with reasonable consumer expectations or the context in which the data was provided
- The lack of the consumer’s data would prevent or limit the business in complying with legal obligations, exercising legal claims or rights, or defending legal rights
- The CCPA does not cover that type of personal information
The Right to Non-Discrimination
Without the right to non-discrimination, businesses could prevent consumers from exercising their control over their data.
As per the CCPA, the right to non-discrimination refers to the mandatory requirement in which businesses have to provide the same quality of products at the same price to both consumers who have and who haven’t exercised their data privacy rights without denying access to their services.
However, there is one exception to the rule.
When a consumer opts out of the sale or requests his data to be deleted, a business may not be able to complete the transaction if it needs the user’s personal information or a related sale to provide him goods or services.
But in such a case, the business can still provide services to the consumer by rightfully denying his opt-out or data deletion request (as this is considered an exception under the CCPA).
While businesses can’t discriminate consumers based on whether they have exercised their rights under the CCPA, the privacy law allows them to offer promotions, deals, and discounts in exchange for collecting, storing, or selling their users’ personal data.
However, organizations can only offer such deals to consumers if the financial incentive is reasonably related to the value of the users’ personal data.
According to the CCPA, by opting out of a sale or requesting to delete their personal information, consumers might not be able to participate in the special data-related deals of businesses.
How Is the CCPA Enforced?
It’s important to mention that the CCPA lacks a dedicated government body or agency responsible exclusively for enforcing the privacy law.
With that said, the California Consumer Privacy Act can be enforced in two ways.
First, consumers have the right to sue a business violating the CCPA but only in a limited number of cases, all of which are related to data breaches.
In the instance of a data breach, a consumer can initiate a lawsuit against a business if his non-encrypted and non-redacted personal information was stolen due to the company’s failure to use reasonable security measures to protect it.
In such a case, a consumer can sue the business for statutory damages.
But before doing so, the user has to first give written notice to the company of the specific CCPA sections it violated.
After submission, the business has a maximum of 30 days to respond to the consumer with a written statement about curing the violations the user referred to, as well as a guarantee that no further CCPA violations will occur.
Unless the business refuses to respond in the above timeframe or continues to violate the CCPA’s rules, the consumer is unable to sue a company that has managed to cure the violation.
Also, consumers can only sue a business in the event the following personal information types have been stolen in a non-encrypted and non-redacted form during a data breach:
- Sensitive government-issued documents or unique ID numbers used for identification purposes (e.g., social security and passport numbers, driver’s licenses, tax IDs)
- Financial information combined with the security code or password that allows someone to access the account (e.g., credit card number with a CVV or a bank account number with a username and password)
- Medical and health insurance information
- Biometric data used for personal identification (e.g., fingerprints, photos used for facial recognition purposes)
California’s Attorney General is responsible for enforcing all other CCPA violations.
While the Attorney General can file an action against non-complying companies, he doesn’t represent individual California consumers.
Instead, the Attorney General’s office monitors consumer complaints to identify patterns of misconduct and may launch a large-scale lawsuit against violating businesses on behalf of California citizens.
What Are the Fines and Consequences of Violating the CCPA?
In the last section, we have explored how the California Consumer Privacy Act can be enforced. Now, let’s see what the fines and consequences of violating the CCPA are.
For violating the CCPA, authorities can punish a business with fines, which fall into two categories.
In the first category, the consumer is the one that sues the company. Here, the fines are less severe for non-compliant businesses, ranging from $100 to $750 per consumer per incident or actual damages (whichever is greater).
However, the state can impose a fine of up to $2,500 per violation for an organization that unintentionally breaches the CCPA. Intentional infringements come with a higher price for businesses, which can be up to $7,500 per violation.
At first glance, the CCPA’s fines can seem rather mild compared to a strict privacy law such as the EU’s GDPR, where a single penalty can be as much as 20 million EUR ($23.66 million) or 4% of the annual global turnover of a company.
However, these can add up to a hefty fine as authorities punish companies by the number of violations or incidents (or actual damages) per consumer. For that reason, non-compliance with the CCPA bears high costs even for a business that serves only a few California consumers.
How Is the CCPA Different From the GDPR?
Upon passing the bill in April 2016, the EU’s General Data Protection Regulation (GDPR) has been pretty much in the spotlight, and remains so, long after it became enforceable in May 2018.
And it shouldn’t come as a surprise.
Applying to all businesses targeting EU citizens, the GDPR introduced strict rules for companies while providing increased control to 515 million people over their data.
With businesses facing maximum penalties of up to 20 million EUR ($23.66 million) or 4% of their global annual turnover (whichever is greater), European authorities have imposed nearly 260 million EUR ($308 million) of fines to non-compliant companies to date.
While the CCPA and the GDPR share similar features, there are some major differences between the two data protection laws.
In the table below, you can see how the two data privacy regulations compare:CCPAGDPRBusiness CoverageFor-profit businesses that do business in California fall into one of the three categories: 1.) Have an annual gross revenue above $25 million, 2.) Interact with the personal data of 50,000 or more California consumers, 3.) At least 50% of their annual revenue comes from selling the personal information of California consumers.All data controllers and data processors that are either based in the European Union or interact with the personal information of EU citizens (no matter where the organizations are located).Parties ProtectedCalifornia consumers, referring to any natural person that resides in the state for other than a temporary or transitory purposeEU data subjects, referring to all citizens in the European Union that have their personal information collected or processed by organizationsEnforcementCalifornia’s Attorney General with the option for the state’s consumers to sue businesses for damagesThe data protection agencies of EU member states with the option for European Union citizens to initiate lawsuits against non-compliant organizationsData Types CoveredAll personal information that relates to, identifies, or could reasonably be linked with a California consumer or household, with the exception of publicly available personal data from federal, state, or local government recordsAll data that relates to an identified or identifiable EU data subjectConsent RequirementsBusinesses must obtain the consumers’ consent in the case of minors, or when users have previously opted out of the sale of their personal informationUnless a legal basis applies, organizations must obtain the consent of EU citizens prior to processing their dataSecurity RequirementsWhile the CCPA lacks specific security requirements for businesses, consumers have the right to sue violating companies for damages that are the result of their failure to follow the appropriate security practices and proceduresAs per the GDPR, both data controllers and data processors are required to implement both technical and organizational security measures appropriate to the level of risk involvedConsequences of Non-Compliance$100 to $750 per consumer per incident or actual damages (whichever is greater) in the case of consumer lawsuits, and $2,500 to $7,500 per violation of civil penalties imposed by California’s Attorney GeneralUp to 20 million EUR ($23.66) or 4% of the annual global turnover of the violating organization (whichever is greater)
In addition to the differences listed above, there’s another main difference between the two data privacy laws.
While it includes most of the rights introduced in the GDPR, the CCPA lacks the right to rectification and the right to object to automated decision-making.
Also, the CCPA only provides partial coverage for the GDPR’s right to restrict processing and the right to object to processing in the form of the right to opt-out.
What Is the California Privacy Rights Act (CPRA) and How Is It Different From the CCPA?
Also called the “CCPA 2.0”, the California Privacy Rights Act (CPRA) is an extension of the CCPA.
Passed in California in November 2020, the CPRA aims to address the limitations of the CCPA to protect the state’s consumers more efficiently.
One of the most important changes the CPRA introduces is establishing an organization – called the California Privacy Protection Agency (CPPA) – that is solely responsible for enforcing the state’s privacy laws.
With this move, the CPRA seeks to relieve the California Attorney General’s burden and instead create an agency that has the necessary resources to take legal action against non-compliant businesses.
Furthermore, the CPRA introduces two new rights:
- The right to rectification: With the right to rectification, consumers can request businesses to correct inaccurate personal information.
- The right to restriction: Here, consumers can exercise their right to limit how businesses use and disclose their sensitive personal data.
Also, businesses collecting personal data from California consumers have to clearly and transparently inform users in case they use automated decision-making technology.
Regarding personal information, the CPRA differentiates sensitive (e.g., social security numbers) and standard consumer data, introducing separate rules for interacting with each. Also, authorities can impose three times the fines for violations that involve minors’ personal data.
Furthermore, the CPRA requires companies to protect the privacy of not only California consumers but also of their employees and independent contractors.
Although the CPRA was passed in November, it will only become effective on January 1, 2023, and enforceable on July 1, 2023.
With that said, the refined privacy law will likely have an impact on how companies collect personal information from January 1, 2022.
What Are the Advantages and the Downsides of the CCPA?
In this section, we have collected the advantages and the downsides of the California Consumer Privacy Act.ProsConsIncreased data privacy rights for consumersLess rights than in the GDPR, which only apply to California consumers on the state levelWhile the California Attorney General is responsible for enforcing the CCPA, consumers can sue companies for statutory damagesThe CCPA lacks an agency solely dedicated to enforcing the consumers’ privacy rights and California residents can only commence lawsuits against violating businesses in a limited number of casesAs the refined version of the CCPA, the CPRA introduces more rights to California consumers and fixes some of its predecessor’s shortcomingsConsumers have to wait until January, 2022 before noticing the effects of the privacy law, which will not become enforceable until July, 2023Since there is no upper limit for the fines, organizations violating the CCPA’s rules face dire consequencesThe CCPA doesn’t cover all types of personal information and only applies to for-profit organizations that do business in California and fall into one of the three threshold categoriesDespite being only a state-wide privacy law, since it applies to a large part of US organizations, the CCPA introduces a new standard for data privacy across the United StatesBusinesses can take advantage of their compliance with the CCPA to increase the trust and loyalty of their customers
CCPA: A Crucial Step Towards Consumer Data Privacy
Providing increased control to California consumers over their personal information, the CCPA is amongst the most important data privacy laws in the United States.
While it takes some extra legwork for businesses to comply with the CCPA’s regulations, they can showcase their dedication to follow the state’s data privacy laws and thereby increase their customers’ trust and loyalty.
CCPA may only cover California residents, but because the law applies to many businesses in the US and abroad, it introduces a new standard in data privacy (especially in the United States).
As a result, an increasing number of US states have come up with their own data protection regulations, with a growing chance for a federal consumer privacy law to be introduced in the (near) future.
On the flip side, the CCPA is not as strict as the EU’s GDPR and clearly has its shortcomings.
With that said, the newly passed California Privacy Rights Act (CPRA) will provide a solution to the majority of those issues.
Blockchain in Ecommerce — Benefits, Use Cases, & Future
The consumer behavior shift from offline to digital created a boom in the already fast-growing ecommerce market.
While global ecommerce sales accounted for only $1.34 trillion in 2014, Statista expects the market to reach $4.2 trillion by 2020’s end with further growth to over $6.5 trillion by 2023.
According to another study, online shoppers are anticipated to account for 95% of all purchases by 2040.
However, the ecommerce industry faces multiple issues that decrease its efficiency and contribute to the slowing of its growth.
Fortunately, blockchain technology can provide an effective solution for many problems encountered by ecommerce platforms.
In this article, we will explore blockchain ecommerce, as well as the use-cases and benefits that distributed ledger technology (DLT) can provide to the online shopping industry.
Blockchain 101: The Benefits of Distributed Ledger Technology
Before we deep-dive into blockchain ecommerce, let’s first take a look at the most important features of distributed ledger technology.
Real-Time Data Distribution
With its first major use-case pioneered with Bitcoin’s launch in 2009, the blockchain is a digital ledger that duplicates and distributes all recorded data across an entire network of computers.
How data is shared in blockchain networks is similar to how contributors see a Google Doc’s content. Instead of copying or transferring the document, it is distributed to all participants who we shared the file with.
Every participant has access to the document, while all changes to the Google Doc are recorded in real-time and in a transparent way.
Decentralized Network Infrastructure
However, unlike Google, blockchain solutions do not use central servers for data storage.
Instead, it operates in a decentralized way where miners (or validators) maintain the network. In exchange for validating transactions and adding new blocks to the chain, they receive a share of transaction fees and block rewards.
Since data is stored on thousands (if not millions) of servers across the whole network, blockchain platforms feature a much higher security level than record-keeping systems based on a centralized infrastructure.
51% Attacks and Public-Key Cryptography
A consensus is needed among validators to add new blocks and confirm transfers while each transaction is encrypted and linked to the previous one after approval. As a result, malicious parties have to control the network’s majority (called the 51% attack) to alter a single transaction on a blockchain.
Since the attack requires a significant upfront investment from hackers – and is almost impossible to carry out for large networks like Bitcoin’s –, it discourages cybercriminals from initiating it.
Blockchain networks use public-key (asymmetric-key) cryptography and digital signatures to encrypt and verify transactions. Unless a user’s private key is compromised, it’s nearly impossible to break the cryptographic encryption cryptocurrencies and DLT solutions use.
Transparency and Traceability
As a result of blockchain technology’s immutable nature, the data uploaded on the distributed ledger is accurate, transparent, and consistent.
On public blockchains, all information on the chain is available for anyone to inspect and analyze.
Therefore, unless the solution uses a privacy-based architecture to achieve (semi-)anonymous transactions (e.g., Dash, Monero, Zcash), users can track their transfers and get an insight into where a digital asset is at in its journey.
Smart Contracts and the Lack of Third-Parties
One of the best features of blockchain technology is the lack of middlemen.
Transactions are executed in a peer-to-peer (P2P) nature without third-party involvement. This limits the risks of human error and increases the efficiency of the network, speeds up transactions, and significantly decreases the costs of transfers.
To facilitate automation, multiple blockchain networks (e.g., Ethereum, EOS, NEO) feature smart contracts that allow a digital agreement between parties to be executed automatically upon its conditions being met.
DLT + Online Shopping = Blockchain Ecommerce
Due to distributed ledger technology’s benefits, companies are increasingly experimenting with blockchain solutions in multiple industries.
As a result, the blockchain market’s size is estimated to expand rapidly from 2018’s $1.2 billion to $39.7 billion by 2025 with a compound annual growth rate (CAGR) of nearly 65%.
Therefore, it makes sense for businesses to implement distributed ledger technology with online stores to create blockchain ecommerce platforms.
However, most existing blockchain-based ecommerce platforms are rather immature, featuring only basic implementations of the technology.
A good example is OpenBazaar, a decentralized, P2P ecommerce marketplace where users can buy and sell products via cryptocurrency without any fees or restrictions.
Instead of a centralized, company-managed structure, OpenBazaar is maintained by its users, contributing their computing power to support the marketplace. On the other hand, many of the platform’s activities take place off the chain (e.g., user feedback, shipment tracking).
With that said, multiple cryptocurrency projects and traditional companies (such as IBM, Microsoft, and Visa) are developing blockchain solutions to integrate with ecommerce platforms.
Top 6 Blockchain Benefits and Use-Cases for Ecommerce
Below, we have collected the top benefits and use-cases of blockchain technology for ecommerce.
Let’s see them!
1. Fast and Cheap Transactions
As blockchain technology eliminates the middlemen, cryptocurrency transactions are processed quickly while featuring very low costs.
Contrary to digital currency transactions, merchants pay anywhere between 2-6% for processing payments on ecommerce platforms.
In addition to the percentage-based fees, some payment gateways charge a fixed price for online purchases, while others feature monthly account maintenance costs.
On top of this, payment gateways often impose foreign exchange fees or use a spread on the conversion rates for transactions other than the merchant’s base currency.
These high fees hurt the profitability of ecommerce businesses that operate on small margins.
Despite the hefty costs, most payment gateways don’t immediately credit the sum on the ecommerce store’s account upon successful purchase. Card transactions go through multiple parties before they get processed, which can take anywhere from 24 hours to three days.
However, even after processing them, many payment gateways still put the transactions on hold, taking several days, a few weeks, or even a month for the merchant to receive. Service providers usually do this due to security reasons (e.g., for high-risk industries), while others use payment cycles to mass-distribute merchants’ transactions.
Holding merchant funds for longer periods decreases ecommerce businesses’ working capital to cover inventory purchases and operational costs, reducing companies’ potential for growth.
Integrating cryptocurrencies into a blockchain ecommerce platform is a good solution to decrease merchant fees and speed up the process in which stores receive transactions from customers.
Compared to payment gateways, it takes up to one hour for Bitcoin (BTC) transactions to be confirmed with an average fee of $2.27.
However, ecommerce stores can further limit their fees and cut transaction processing times by accepting a digital asset like Ripple (XRP) that takes around 4-5 seconds to be received with transfer fees under $0.0001 on average.
In addition to benefiting from faster and cheaper transactions, ecommerce stores can implement cryptocurrencies to expand the payment methods they offer to their customers.
However, digital assets often feature high volatility levels. In fear that the value of the coins decreases before they can convert them to fiat currency, businesses are often hesitant to adopt cryptocurrencies.
Fortunately, there are multiple cryptocurrency payment gateways on the market – including BitPay and Coinbase Commerce – that use stablecoins (e.g., DAI or USDT) or instantly convert a customer’s digital assets to the merchant’s fiat currency of choice to eliminate volatility risks.
2. Chargeback Fraud Protection
Since the dawn of online shopping, chargeback fraud has been a major issue for ecommerce businesses.
While there are a wide variety of reasons why customers request chargebacks from banks, a study revealed that as much as 81% of shoppers file chargebacks out of convenience instead of contacting the merchant for a refund.
Even if the reason is legitimate, filing a chargeback before contacting the merchant is called friendly fraud, which cost ecommerce businesses $4.8 billion in 2016.
On top of this, another share of fraudulent chargebacks originates from customers who never had the intention to spend money on a product. They buy the item and request a chargeback soon after the ecommerce store has shipped it.
Another popular reason why customers request chargebacks are due to actual fraud. Here, cybercriminals acquire a person’s credit card details and use it fraudulently to purchase a product from the merchant.
Whatever the reason, chargebacks are expensive for ecommerce businesses. Many businesses spend a significant part of their budget to combat fraud and reduce the risks of illegitimate refunds.
However, ecommerce businesses that integrate cryptocurrencies can eliminate chargebacks entirely.
Since there’s no payment reversal for digital assets, once a customer pays for a product, he can’t file a chargeback or circumvent the merchant via an external service to get a refund.
Shoppers can still contact ecommerce businesses to get a refund for the products they didn’t like or receive (or for any other reasons).
3. Cybersecurity and Data Privacy
While cybersecurity is one of the top challenges for ecommerce businesses, trust, and privacy are among the top pain points of online shoppers.
As they don’t possess the necessary resources or have other priorities, ecommerce businesses often fail to set up proper security measures against potential cyber attacks.Upon a successful hack, malicious parties can easily launch a Distributed Denial of Service (DDoS) attack against an ecommerce business. This causes severe downtimes and generates significant losses for the company.
The lack of proper cybersecurity measures can also put user data at risk. At the same time, ransomware attacks can threaten the deletion of an ecommerce business’s data unless a ransom is paid to the hackers.
As stolen financial information can cause significant losses for consumers, many online shoppers refuse to trust ecommerce businesses.
Furthermore, even if an online store features state-of-the-art security and efficiently protects customers against cybercriminals, the business can still decide to sell consumer data to advertisers and other third parties to generate extra profits.
Implementing blockchain technology could restore consumer trust in ecommerce businesses as DLT’s transparent nature reveals whether a company has misused its customers’ data.
Moreover, with public-key cryptography and decentralized network infrastructure, a blockchain-based ecommerce store would significantly decrease the risks of a successful cyber attack against the platform.
Permission takes data management to the next level.
As part of a blockchain-based, next-generation advertising platform, Permission.io users are in full control over their data. Consumers decide whether a company can use their personal information and how.
In exchange for permission to target a user based on that user’s data, Permission.io users are rewarded in ASK, the platform’s native cryptocurrency.
Consumers can choose to hold the ASK they earned, exchange it, or spend the digital asset directly on products in the Permission Redeem Platform.
4. Supply Chain Management
A supply chain refers to the network in which an organization and its suppliers work together to manufacture a product and distribute it to the end customer.
With multiple participants, supply chains allow companies to cut their costs while increasing their competitiveness. Therefore, effective supply chain management is crucial for every ecommerce business.
Supply chains include multiple stages – from producing the item and distributing it to the consumer. Due to this reason, if only a single-phase gets compromised, it could result in grave consequences and jeopardize the entire supply chain.
A problem can be as little as a delay in transportation to cause an ecommerce business (and the customer) big headaches.
Traditional supply chains struggle with increasing costs as well as the lack of transparency, traceability, and proper communication between parties.
As a result, ecommerce businesses are unable to get an insight into a product’s origins, ensure that it is manufactured using high-quality materials, or maintain reliable delivery times.
Moreover, there is a surging demand for traceability among consumers.
Fortunately, with the rise of blockchain technology and the availability of cheap and effective tracking equipment – like radio-frequency identification (RFID) tags and QR codes – ecommerce businesses can finally achieve effective supply chain management at a cost-efficient price.
With DLT tech, each participant of the supply chain adds data about a product to the blockchain.
Even if a company uses a permissioned blockchain platform, all the supply chain’s members are able to see at which stage an item is currently at in its journey while monitoring data points to detect dishonesties.
Furthermore, the blockchain’s immutability makes it impossible to upload fake data or tamper with the information in any other way.
Unlike traditional solutions, blockchain-based supply chains don’t require hiring third-party service providers for contract negotiations. Instead, businesses can decrease their costs by uploading all data about the agreements on the blockchain while enforcing them with smart contracts.
As a result, ecommerce businesses can allow their customers to trace the products they purchase in the supply chain, greatly increasing their services’ transparency.
VeChain is among the most popular blockchain projects working on enterprise supply chain solutions.
Using the Proof-of-Authority (PoA) consensus model, smart chips, and its high-performance blockchain network, VeChain seeks to add transparency and traceability to every stage of supply chains.
5. Enhanced Loyalty Programs
Loyalty programs are a great way for ecommerce businesses to motivate existing customers to stay devoted to their brand, encouraging them to shop more often and in larger quantities.
In addition to providing deals on items, efficient ecommerce loyalty programs reward consumer engagement beyond placing orders (e.g., social contests, active participation on different company channels).
While offering points after each purchase as a reward can work great for ecommerce loyalty programs, customers won’t be able to redeem them until they accumulate a certain amount. And this can discourage some consumers from joining the program.
On the other hand, with blockchain technology, ecommerce brands can introduce enhanced loyalty programs where consumers receive the project’s native cryptocurrency as a reward for active participation.
Since the token can be exchanged to fiat currency or other digital assets, customers will be able to turn the rewards they earned via blockchain ecommerce loyalty programs instantly into cash or other cryptocurrencies.
Or, even better, the ecommerce business can allow customers to spend their rewards directly on products in the company’s store.
A good example of the latter is the Permission Redeem Platform, where consumers can shop with the ASK they earned.
Offering rewards that can be (near-)instantly converted into cash after receiving them can help ecommerce businesses turn their existing customers into loyal shoppers.
Moreover, since consumers are always looking to earn extra income, ecommerce stores can also use blockchain-based loyalty programs to attract new prospects.
6. Eliminating Fake Reviews
Fake reviews have always been a major issue ecommerce businesses have been facing.
According to a Bazaarvoice study, 43% of consumers lose trust in a brand if it features fake or fraudulent reviews about its platform.
At first glance, one would think this issue only affects dishonest ecommerce businesses and their past customers.
However, that’s not the case here. After identifying multiple fake reviews, consumers will lose confidence in online feedback systems.
As a result, they will take the product feedback they read with a grain of salt while becoming increasingly hesitant to purchase even an honest ecommerce store’s top-rated items.
This alone can hurt business. But to make things worse, competitors can use deceitful tactics and techniques to post fake negative reviews about rival ecommerce stores.
Since 82% of consumers read feedback on a product before making a purchase online, it’s crucial for ecommerce businesses to combat fake reviews.
A good solution to the problem is to adopt blockchain technology where all data points can be traced back to its origins without the ability to alter them.
For example, by tracking transactions, an ecommerce business will be able to verify whether a customer has ordered the product he sought to post a review on.
Also, service providers can incentivize their customers via cryptocurrency rewards to post comprehensive, honest, and helpful reviews on the products they purchased.
Revain, a blockchain-based review platform, provides incentives in tokens to users for doing just that.
Furthermore, the solution utilizes IBM Watson’s Tone Analyzer and Natural Language Understanding for accurate feedback filtering while continuously verifying reviews on the platform.
Blockchain: The Future of Ecommerce
Since Bitcoin’s birth in 2009, blockchain technology has disrupted multiple industries, such as the payments, finance, and digital identity sectors.Now, distributed ledger tech is coming to a new market: ecommerce.
By facilitating fast and cost-efficient transactions, featuring increased security, combatting chargeback fraud and fake reviews, as well as creating next-generation supply chains and enhanced loyalty programs, blockchain-based ecommerce provides benefits to both merchants and consumers.
Leveraging DLT’s advantages, businesses can create next-generation ecommerce platforms that feature lower costs and increased transparency while eliminating the need for third parties.
Therefore, companies can increase their competitiveness and attract loyal customers to their brand.
Interested in earning cryptocurrency by engaging with advertisers and leveraging your data?
Register an account at Permission to get started and earn 100 ASK right away!
Ad Fraud and the Taming Power of the Blockchain
A recent report from the World Federation of Advertisers claimed that ad fraud was second only to drug trafficking as a criminal enterprise. It’s certainly big business; Juniper Research estimates that it harvested $35 billion globally in 2018 and $42 billion in 2019. That’s not exactly chump change.
For criminals, ad fraud has quite the allure. Startup costs are low—a good PC, software tools, and an Internet connection are all that you need to get started. Compare this to establishing a drug cartel: organizing peasants to grow drug crops, hiring thugs, establishing an international supply chain with smugglers and mules, and bribing officials. Competition can be fierce, and when I say fierce, I mean drive-by-shooting fierce. Then there’s jail time to worry about, not to mention finding ways to launder the profits.
Cybercrime and the Ad Fraud Business
Cybercrime has much more to recommend it. Admittedly, you will need software skills honed by a few years of experience, and location can be crucial. It’s going to help if you live in a country like Russia or Belarus which has no extradition treaty with the US. The risk of jail time is lower than drug trafficking, but hackers do get caught every now and then.
Ad fraud is by no means the only financial opportunity out there. You can make a healthy living from ransomware; Netwalker ransomware earned its perpetrators $25 million in just a few months. Data theft can also be lucrative. Credit or debit card information fetch up to $110 and medical records up to $1000 on the black market.
In case you think such diversification is too ambitious for a ‘mom and pop’ hacking outfit, don’t be concerned. They are natural sidelines that will integrate neatly with your main line of business: ad fraud, the most lucrative form of cybercrime.
The Ad Fraud Industry
Ad fraud is a game of deception. The goal is to create fake traffic (clicks on ads that were not made by real people), fake leads (apparent sales leads that are not real), and fake placement of ads (on websites that are not real websites). Advertisers pay for activity that appeared to reach an audience but never did.
Organizing this requires computer resources. That’s where a significant investment, mainly of time and effort, will be necessary. The hacker needs to create bots (automated software placed on hijacked computer devices) and botnets (networks of bots, automated to work together). There are many applications that need to be run; you need apps for password cracking, for encryption, for virus generation, for phishing and spear-phishing, for network probing, and for specific exploits. Most of these can be bought at competitive prices on the darknet.
Nevertheless, growing a sizable botnet takes time, and the size of the botnet is proportional to the income it generates. The largest recorded ad fraud operation was perpetrated by the Methbot botnet. Run by just eight Russian hackers, it harvested over $1 billion per annum at its height. It spread across 571,904 compromised devices, mainly servers located in Europe and North America—equivalent to a fairly large data center running 24/7.
It supported 6000 websites with over 250,000 web pages for showing video ads. The hackers fooled the digital ad market’s selection algorithms into choosing fake web pages over legitimate ones and charged advertisers at a premium for the ads.
And that is just one kind of ad fraud. There’s ad hijacking, where the hacker hijacks a website’s ad slots, from a user device or directly, either to generate false clicks or place their own ads. Another possibility is to hijack the ad click itself, directing the user to a different web site. There’s ad stacking, where ads are stacked on top of each other on the web page so that one click is registered for every ad in the stack. How about cookie stuffing, where hackers add affiliate strings to URLs to mimic conversion activity. There are fake apps for mobile phones that can hijack ad traffic. The possibilities are legion.
What’s more, the botnets a hacker builds can be rented out to companies that wish to sabotage competitors’ ad campaigns or bombard competitor websites with denial of service attacks. They can even be rented to other hackers working on different projects. You can think of it as a cloud service.
How Can We Fix This?
Figures (from both Juniper Research and AdAge) suggest that roughly a third of digital ad revenue is collected by the hackers. The sad fact is that ad fraud is far too successful and radical solutions are needed. The underlying problem is the lack of authentication and audit trails in digital interactions. It’s simply too easy to pretend to be legitimate.
Luckily technology, blockchain technology, provides a solution. When users achieve data sovereignty it will be easy to enforce bullet-proof user authentication. The same will be true for all organizations. The same is also true of devices whether servers or simple IoT sensors. As long as they are linked directly to an authenticated owner, an audit trail can be established. By linking together and storing audit trails on the blockchain, it becomes possible to forge a web of trust, where bad actors are ejected as soon as they are detected.
The best solution to fighting ad fraud is to create an ad ecosystem where clicks are provably human and ads can be sourced back to real businesses. The upside of this, aside from the obvious reduction in ad costs, is that an ad market based on trust can be established, where users willingly and securely share their data with advertisers to enable accurate targeting and verified ad impressions. Given the cost savings, a cryptocurrency-based arrangement would be possible, allowing advertisers to regularly reward consumers who watched their ads.
If that sounds like what we are doing at Permission, you’re getting the picture.
Of course, this would be terrible news if you were pursuing a career in cybercrime.
First Party Data — A Complete Guide for Marketers
If you work in marketing, chances are you use first party data every single day. Traditionally referred to as the most valuable of all data types, we use first party data to retarget consumers online, deliver specific products based on purchase behavior, and much more.
In the data economy, the smarter you are with your data, the more you will succeed. We’d also argue that the more respectful and permission-based your data collection practices are, the better experience your users will have. This positive experience turns into goodwill, which turns into loyalty and ultimately results in more sales.
Before we go into the details on first party data and how to best use it, let’s briefly cover all four major data types marketers use.
Defining the Most Commonly Used Data Types
What Is First Party Data?
First party data is any data collected by companies on their own customers.
This means any CRM data, purchase history, or demographic information you have within your system. If it was requested or collected by your company and is exclusive to your company, then it’s first party data.
Businesses collect first party data with forms, surveys, pixels, shopping records, shipping addresses, and more. This data is extremely valuable to businesses because it offers direction on how to message existing customers while giving companies a blueprint for attracting more of their best customers.
First party data is also where many privacy issues arise, with major breaches leaking sensitive information around the internet ecosystem and generally undermining the privacy of users.
What Is Second Party Data?
Second party data is any first party data sold to other companies.
If you collect data from your customers, package it up, and then sell it to another company, then that first party data becomes second party data. Conversely, if you purchase email lists, demographic information, or purchase history data directly from the company that collected that data, then you have purchased second party data.
What Is Third Party Data?
Third party data is any data that you use or buy from a company that isn’t the original collector of that data.
Third-party data is most commonly packaged into large data sets built off of first party and second-party data. It commonly includes demographic data, psychographic data, bulk email lists, and other expansive data sets.
What Is Zero-Party Data?
Zero party data is any consumer-owned data that is given up voluntarily by a consumer to a company in return for some benefit.
Meet the new kid on the block, zero-party data. This could be notification of buyer intent, shopping preferences, product feedback, identifying information, or ad preferences.
Zero-party data is the future of advertising data because users own their data in a zero-party data relationship. In first party data, companies own the data they collect.
Zero-party data is made possible through opt-ins on both sides of the advertising equation. Certain blockchain currencies require that companies pay consumers for their data. Zero-party data champions user rights while better matching users with brands, resulting in a win-win relationship that is mutually beneficial for both parties.
While zero-party data isn’t yet widely adopted, big changes are coming to the internet that will make it mainstream.
The Power of First Party Data: How Marketers Use It
Again, first party data is data you collect on behaviors and actions taken across your website, app, and/or product. This includes information in CRM profiles, your social media data, any survey responses, any email marketing data, and any other data your company has based on your users’ actions.
This is important data to advertisers and allows them to advertise with specificity and purpose. Here are a few ways you can use first party data:
1. To Build Accurate Customer Profiles
Customer-relationship-management software (CRMs) like HubSpot, ActiveCampaign, Salesforce, and others are really just software designed to utilize first party data that your company collects. FPD gives companies the opportunity to build unique customer profiles, which allows you to use product and demographic-specific messaging while keeping track of sales conversations at the same time.
2. To Segment Your Customer Base
Segmentation is an incredibly important tool marketers use to create a sense of specificity. Specificity is simply targeted actions based on what you know about a customer. This could be behavior information such as pages they have viewed on your website, demographic information like gender, age, and occupation, or any other first party data that you have collected.
Any time you differentiate one set of customers from another, you are performing segmentation. If you haven’t taken the time to create buyer personas and use those to dictate your decisions around the first party data you have, then that’s your first step.
3. To Create Personalized Retargeting Campaigns
Platforms like Facebook, Adroll, Google Ads, and Pinterest allow you to deliver ads to the same people who have interacted with your profile or site. This isn’t possible without first party data. When you install a pixel on your site and track user behavior, you are collecting first party data.
4. To Build Email Automations
Email automations are built on triggers based on buying behavior, demographics, website data, and surveys — all of which are types of first party data. Whether you’re building in ActiveCampaign, Mailchimp, Drip, or WildMail, it’s all powered by FPD.
5. To Educate Your New Advertising Efforts
Marketers also use FPD to give them insight into potential customer pools. For example, if you know through surveys and collected information that your best customers are U.S.-based, 35-44 females interested in science and politics, and your company is about to expand in the U.K., your first campaign in that market should target 35-44 females interested in science and politics.
You can structure your entire U.K. marketing campaign around these facts, and while any new market is unique and deserves to be treated as such, FPD helps marketers make more educated decisions and refine their experiments.
6. To A/B Test Your Marketing Efforts
A/B testing occurs any time you compare the results of two assets over a time-bound period. Let’s say you had a new product that allowed users to put a physical picture inside an item of their choice, and you identified two major selling points: the ability to “capture a memory” and “personalization.”
You could construct two separate landing pages, one with “Collect Your Memories” as the headline and the other with ‘The Most Unique and Personalized Gift Ever!” By using tools to collect how often users click and buy — a type of FPD — you could figure out which headline is more profitable and use that information to improve your campaign.
7. To Collect Product Feedback
Requesting product feedback and reviews is another useful type of FPD. Because you are collecting information from your consumers, any recorded feedback or reviews fall under the umbrella of first party data. Marketers and companies can use this data to redesign their existing products, develop new sales, find inspiration for additional features, and more.
8. To Sell Your FPD to Other Companies
Again, any first party data that is sold becomes second party data, and some companies make all of their money this way. Social media companies do this most famously, but anytime you’ve heard of email lists being sold or purchase behavior information being given to complementary businesses, that’s an example of second party data.
And so much more…
First party data is a broad umbrella under which most major marketing ideas, functions, and best practices come from. It’s the first type of data most companies use, and it is often the most valuable, although zero-party data is set to become the next star-child.
5 Common Ways Businesses Collect First Party-Data
If you’re a business operating in any capacity, you’ve already collected some types of first party data — at the very least, the data collected when you make a sale. Here are a few of the most common ways businesses collect FPD:
1. Pixels
Pixels, or site tags, are bits of code that are dropped into the header of your website pages. Every time a user loads a particular page, there’s a bit of communication that happens between that code and whatever service the pixel or tag belongs to. This communication sends anonymous information about the user, including demographic information, the actions they took on the page, and more.
Pixels are most famously associated with Facebook and Google Ads, and they are essential to any business marketing themselves online. You can figure out how to get and install your Facebook pixel here, and you can learn more about Google remarketing tags here.
2. Email Captures
There are countless ways to collect email addresses, but the most common include:
- Putting an email sign-up on key website pages like your homepage.
- Collecting them in person.
- Collecting them during an eCommerce or in-person checkout.
- Collecting them as part of a rewards program.
- Collecting them in return for a PDF or other type of free information.
All major website platforms support email captures and integrate with other major email service providers. Email service providers are the companies that act as a database for your emails and allow you to contact people through them. Major ESPs include:
- Gmail
- Outlook
- HubSpot
- ActiveCampaign
- Drip
- MailChimp
Your choice will depend on your needs, although we are partial toward Gmail for personal use and ActiveCampaign and Drip for businesses.
3. Point-of-Sale Systems (POS)
Your POS is what gives you the ability to accept payments. It is most often used in reference to the software that powers your terminal, although most POS systems include and communicate with an online payment gateway as well.
Each time a card is swiped, information about that customer is collected. Some of this information, like purchase amount, product purchased, etc. happens automatically, and other information like email addresses, preferences, etc. are collected voluntarily when requested by the business to the customer.
The best POS systems tie directly into your CRM, allowing you to use that data to educate your marketing decisions. For example, let’s say you have a product that expires every three months. You could export all of the customer email addresses who purchased three months ago, tag those addresses in your CRM or ESP, and send a targeted email to those customers with a discount because you know it’s around the time they should be purchasing again.
4. Customer Relationship Management Systems (CRM)
CRMs come in all types and variations, but they are fundamentally a way for you to centralize all the information you need to contact and interact with prospects and customers. CRMs usually include a combination of email sending and creation tools, SMS messaging tools, landing page tools, customer profile information, and email automation capabilities.
5. Manual Input via Call Centers and Employees
While first party data is much more efficient and effective when collected automatically, there is plenty of reason and opportunity to collect FPD when your team is working with your customers. Manual collection of FPD includes collecting email addresses at trade shows and writing down data from inbound sales calls.
Companies are always in pursuit of more FPD, and the best system for your company will inevitably change over time — look at data collection as a consistent effort. The cleaner, more refined, and more actionable your FPD, the better you will be to use it.
First Party Data: No Longer the Best for Marketers or Consumers
Here’s the issue. First party data is clearly one of the best tools marketers and companies have to grow their businesses, but it is a world away from perfect. For starters, users don’t own their data, meaning their personal information is constantly exploited by data-driven companies, and companies are stuck with patchwork data that doesn’t always integrate.
The solution? Give users back ownership of their data and use blockchain technology to pay users to interact with advertisers. This new model is a win-win for both users and advertisers because users have incentives to choose brands that they are genuinely interested in and advertisers eliminate ad spend and build loyalty and trust.
This gets to the heart of zero-party data — by creating an infrastructure that allows for opt-in ads to occur at scale, advertisers will have more complete, more active pools of users to engage. It eliminates so many of the headaches of targeting while giving users back control of their data that is currently harvested without their consent from internet barons like Google, Facebook, and Amazon.
Think it sounds too good to be true?
See how Permission is building that world right now.
Eyebrow Text Here
Don't miss anything
Join our newsletter for the latest news and product updates